It has been said that “If you can’t measure it, you can’t manage it” (Peter Drucker).
That may not apply universally (most rules have exceptions), but it is an interesting way to look at cyber crime; or more accurately the ability to withstand and/or recover from a cyber crime attack.
There are several factors that make cyber crime more or less likely for a given organisation; and if it does occur (i.e. if your organisation becomes a victim) there are other factors that determine how bad it can be.
This combination of likelihood and impact is a significant element in measuring the cyber risk you face.
Gain continuous visibility of your cyber risk
Cyber Crime: Factors that increase the likelihood
So let’s consider some factors that increase the likelihood of your organisation being a victim of cyber crime.
Profile and Noteworthiness
The level of public profile and fame (or infamy) of your organisation is certainly a factor. It is obvious in one sense as if an attacker hasn’t heard of you then how would they know you were there to attack? However this isn’t the full story as an attacker might easily find organisations he is able toattack and then choose one (which could be you).
Certainly, the fact that your name, business, brand etc. is recognisable, famous, notorious or significant in some way makes it a lot more likely that the attacker will decide you are not just a possible target, but the target. It depends partly on their motivation; but if it is any of: money, renown, publicity then the better known and bigger you are the more likely they’ll choose you from a list of organisations that might have some particular vulnerability.
If your profile is such that you are also controversial or contentious maybe in terms of global expansion, or tax affairs, or testing and health/safety, then this itself is also a factor. You might have people out there for whom you are not just a possible target, but actually a prime target.
Reputation and Karma
The degree of social responsibility you have exhibited or “do no evil” that your organisation is associated with could play a big role in you being targeted. Aside from those motivated by a particular grudge against you for a personal reason; there will be factors that determine whether you are seen as “fair game” to everybody else because of some controversial or widely unpopular stance on a topical issue.
For some attackers any target, any database, any list of email addresses and passwords might be enough, even charities have been attacked in the past. Some attackers however might feel that a normally trustworthy, benevolent, or altruistic organisation might deserve to be told about a weakness and vulnerability rather than have it exploited. Whereas one that has a worse reputation may find themselves treated much less cordially.
Perceived level of defence
The difficulty of getting access to your networks and systems may itself be a draw for some attackers. Prestige among the cyber criminal community and even the intellectual challenge of getting somewhere that’s hard to reach might make you a more attractive target.
The higher your actual level of defence is the less chance someone has to defeat the controls you have in place. But there are a lot of people out there trying to gain access to systems with various motivations and you have a finite number of people and resources with which to defend your networks.
The asymmetry between attackers and defenders is very real; so even if you do have good cyber defences there is a chance someone will get access through some ingenious ruse, particularly if they are determined – good cyber security just makes it less likely.
Volumes of customer/citizen/personal data
The volume of data you hold (irrespective of other measures of the size of your company) definitely increases the chances that someone might want to steal it.
For one thing, many cyber attacks rely on scale of inputs to net a single objective. So you need lots of email addresses to send phishing emails in order to get one careless recipient to click on a link or attachment. You need lots of usernames and passwords to crack or find one that is easy, and lots of bank accounts to spread numerous small transactions over to avoid anyone noticing.
In simple terms, every personal data record, credit card number or password has value whether in mounting another attack or in carrying out a subsequent fraud; hence a business with 1m subscribers is more likely to be a target than one that only has 1,000.
Amount and nature of IP
How much intellectual property and sensitive data (non-personal) do you have and how valuable is it?
In some cases the value or nature of your IP might be the very target of the attacker, in others it might just be something they stumble upon that changes an event from being simple and brief intrusion into a more determined and prolonged theft of data.
As an example, there are often fears spoken about the vulnerability of data aggregators (consulting, audit, legal, services companies). They themselves “have data”, but also through services they provide will have data and information pertaining to a whole lot of other businesses. This volume, diversity and richness of intellectual material makes it more likely they will find themselves a target.
Is there money?
People rob banks because that’s where the money is.
That’s certainly true when one considers the financial information that is held by banks, retailers and service/billing organisations. However any identity information can have value if its theft could then allow fraud on another site; additionally a business may have staff or corporate finance information that has monetary value either in it, or in the knowledge it holds about planned activities.
Mergers and acquisitions, product launches and stock exchange filings can all be immensely valuable if they are accessible before they become public; so it is more than just liquid cash assets that can be defrauded, accessed or transferred, it’s the financial benefit the attacker can gain from any data or information that attracts them, so think wider than just the content of the bank accounts.
Achievement of real world effects
A final motivation for attackers that needs to be factored into your risk calculation is whether or not there is scope to achieve visible, tangible, real-world effects resulting from an attack on your systems.
We’re not talking necessarily about spoofing order details so that you accidentally end up over-stocked with inventory like Al Harrington:

“Al Harrington, President and CEO of Al Harrington’s Wacky Waving Inflatable Arm Flailing Tube Man Emporium and Warehouse! Thanks to a shipping error I am now currently overstocked on wacky waving inflatable arm flailing tube men…”
The concern is more about whether access or compromise of your systems could be used to affect power, water, gas supplies, robotic systems, manufacturing etc.
This has been a real problem for a number of businesses that have suffered cyber attacks that have had the effect of making pumping systems, flow control systems, real-world switching systems or other computer-controlled, network connected machinery go… well haywire.
If you are in this situation, then your business might be a target for all sorts of reasons; from creating genuine civic disruption and terrorism to just a desire to cause mischief.
To summarise though, you can measure most of these factors ahead of time as part of your risk management calculations. Sure, for any particular case you would know how many records are stolen or how much money is misappropriated; but you can establish minimums or maximums or averages:
- What is the average account balance?
- How many customer records do you have?
- How much past R&D spend or future revenue can be attributed to your store of intellectual property?
- Are you high or low profile?
- How controversial is your business on a scale of 1-10?
Cyber Crime: Factors that make being a victim worse
The severity of a cyber crime can vary enormously depending on a whole range of factors. Loss of customers might depend on how happy they are and what your normal retention approach is for example. However there are some factors that are universal in determining how bad a breach is and so knowing likely outcomes could help decide what level of risk you face.
The volume of exposed data
Clearly the more data you lose the worse the breach is, in almost all cases. A data theft involving 1 personal data record is a nuisance (especially for the individual), but one that affects 10 million customers is much worse, more newsworthy and the costs/effects will be a lot more severe.
This isn’t always the case of course, a theft of a single document that outlines your plan to invest by acquiring a third party company might mean that the market price of a leaked deal renders the whole thing futile; hence one single fact could be significant. However those sorts of cases tend to be one significant document amongst a whole stash of information that is extracted en masse– with the corresponding embarrassment that causes.
If you have a lot of data though be aware that you might be a target for that very reason alone; and that a resulting breach, in raw numeric terms, will be a problem.
How long it takes you to detect cyber crime
In simple terms, the longer a breach goes undetected the worse it is. Some breaches have been newsworthy almost because of how long it took to detect – Dixons Carphone and Yahoo! are two examples of where this was months. It certainly adds to the newsworthiness and incredulity.
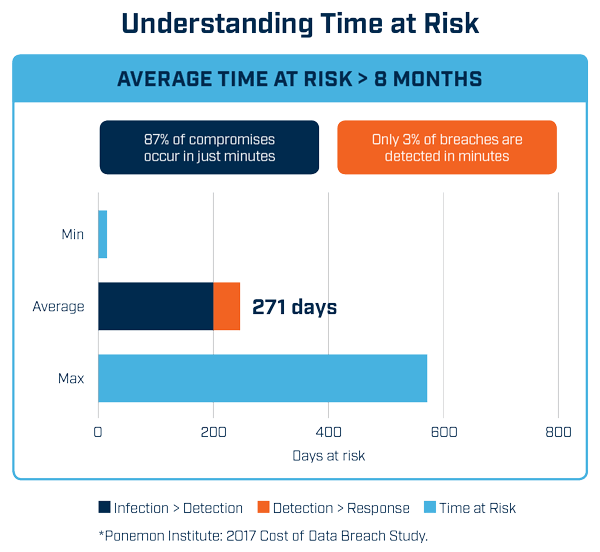
But at a much more specific level if you are able to detect a breach, loss or theft as soon as it happens, or perhaps even while it is still in progress you can much more quickly contain the attack, possibly disable credentials being used, disconnect systems affected or stem the data loss.
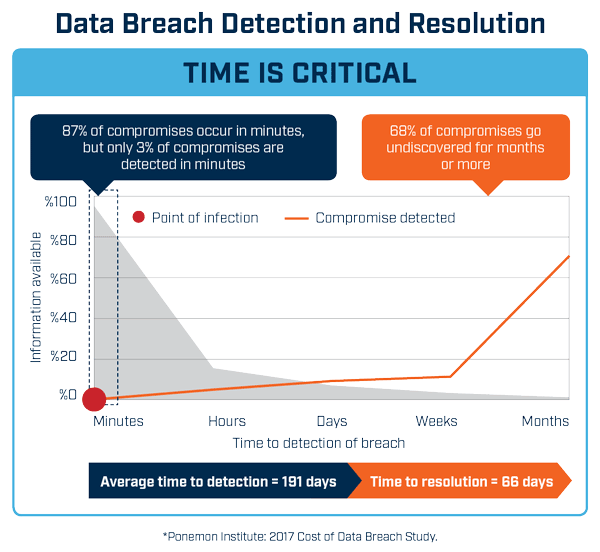
If an attack is extracting 100Gb of customer records or intellectual property and you can detect and close the connection before they get past 10Gb then your exposure is only 1/10thof the numbers of records or value of IP.
The difficulty in this case is predicting ahead of time how fast a breach would be identifiable based on the technologies, visibilities and oversight you are currently deploying.
How sophisticated was the attack that affected you?
This is really a measure of how harshly the court of public opinion will judge your failures.
At one extreme, if you are attacked by a skilfully, well-resourced and determined intruder (by a highly skilled foe, possibly a nation-state sponsored hacking group) with some bespoke zero-day exploit and a devious low-and-slow approach that slipped under your detective radar, then you may have some leeway to say “We are just a manufacturer, we can’t hope to fend off an attack of this sophistication”.
On the other hand, if someone casually finds a SQL injection vulnerability or a default password, and is able to quickly dump your entire customer list complete with credentials and unencrypted passwords, and drop the lot onto a hacking forum, then you’ll have a harder time justifying your defensive resistance.
Again, having visibility of the nature, frequency, likelihood of “low hanging fruit” vulnerabilities in your environment in advance is important.
Do you have sufficient defences to really close off the trivial and simpler attacks?
Your response to cyber crime
If you haven’t had a breach thus far your responses will not have been tested with a real situation and hence are likely to be found wanting. “No plan survives first contact with the enemy” is a useful quote here.
But your level of preparedness around plans, communications paths, data, escalations, roles/responsibilities is something you can assess. Do you have these processes in place? Is there a retainer with a third party forensic or investigation firm? Do you have cyber insurance? Are there pre-prepared press statements or lines of communications with corporate comms? Is your CEO informed enough to say the right things?
You’ll know this – or you can score yourself on this against any number of defined incident handling frameworks such as the NIST or UK government guidelines.
To summarise once again you might not be able to pre-empt the measurements around these factors ahead of a breach occurring; but you can establish some likely bounds around at least some of them. You will know how attentive and responsive your detective capabilities are – do you spot things by actually detecting them, or from the effects or reports of them happening from the business or external parties for example.
Consider, how much coverage you have over the more basic cyber hygiene controls like passwords, patching and privileged management – these fall under the umbrella of “obvious stuff” and if you are getting these things wrong and it leads to a breach you can expect the embarrassment factor to be much higher and the level of sympathy for your organisation to be minimal.
Which factors can you control in the fight against cyber crime?
This is an open question for the purposes of this blog. The circumstances of a breach aren’t known till it occurs. But it is important for you to answer and decide what can be known or anticipated in advance.
If you have a customer database of 1 million records, then a personal data breach of 1 million records and the associated costs of fixing it is not something you can fail to expect. So outline answers to these questions:
- What things do I know?
- What things can I control?
- and What can I not control?
- What things can I measure or assess now?
- and What won’t be evident until something happens?
- What is the minimum, average and maximum likely scale of any given problem?
Measuring cyber crime risks
Measuring cyber risk is tricky. There are a number of factors that affect the likelihood of you being attacked and a number that affect the impact if you are:
Factors affecting cyber crime likelihood
- Profile and Noteworthiness
- Reputation and Karma
- Perceived level of defence
- Volumes of customer/citizen/personal data
- Amount and nature of IP
- Is there money?
- Achievement of real world effects
Factors affecting cyber crime impact
- The volume of exposed data
- How long it takes you to detect
- How simple was the attack that affected you?
- Your response to a breach
The skill is in limiting, controlling and estimating these, and then managing the risks accordingly.
One area where businesses can take real strides is in measuring the baseline levels of cyber hygiene and what they might term “core controls”. This provides a number of benefits:
- It gives you firm metrics for the state of cyber maturity and so allows quantified risk calculations rather than estimations or guesses;
- It reduces the likelihood of attack as baseline controls like patching and privilege management are reported on, and hence exceptions or improvements are handled;
- It lessens the likelihood of a breach being embarrassing due to its trivial nature and means that when an attack does occur it is likely to have been sophisticated rather than facile, and hence easier to defend your handling of;
- Having automated enforcement and reporting around the “low hanging fruit” and core controls means you start to free up resources to allow them to focus on more challenging and taxing problems that can boost security in more complex areas;
And finally, when the worst does happen… you can respond to it more quickly because you can eliminate what it WASN’T caused by; and focus straightaway on looking for what the cause WAS.
Footnote: This blog post was published on 27 November 2018, on 3rd December Forrester Research published some similar views (gated content).
 About Huntsman
About Huntsman





