The 2019-20 ‘Interim Report on Key Financial Controls of Major Entities’ has been released. The Australian National Audit Office’s (ANAO) review focused on the financial and HR systems of eighteen Australian Government agencies.
The report revealed that only one of the eighteen agencies that were reviewed was rated as achieving and managing their cyber resilience to Essential Eight Maturity Level Three requirements. It also found that four agencies had incorrectly self-assessed, due to a poor understanding of their requirements.
Australian Government cyber resilience
The current Australian Government advice, recommendations and mandates associated with the Essential Eight Framework provide a clear target and benchmark for both government and non-government entities, in their pursuit of cyber maturity. However, having the knowledge, resources and time to operationalise the critical security controls, and then maintain them, is where the biggest challenge lies. In a dynamic threat environment, cyber security is an ongoing responsibility.
Self-assessment of security control performance can be subjective and unreliable. In 2019, ANAO reported that 29% of agencies audited were compliant with the Top Four security controls. Whereas 60% of self-assessments found themselves to be compliant. An objective and current measure of cyber maturity is key to maintaining your organisation’s cyber defences.
Establish and maintain Essential Eight controls over time
Security Audit Tool
Huntsman Security’s Essential 8 Auditor, a tool designed specifically to measure the implementation and operational effectiveness of the Essential Eight controls, was developed to support Australian entities and their requirement to implement and measure against the Essential Eight Framework.
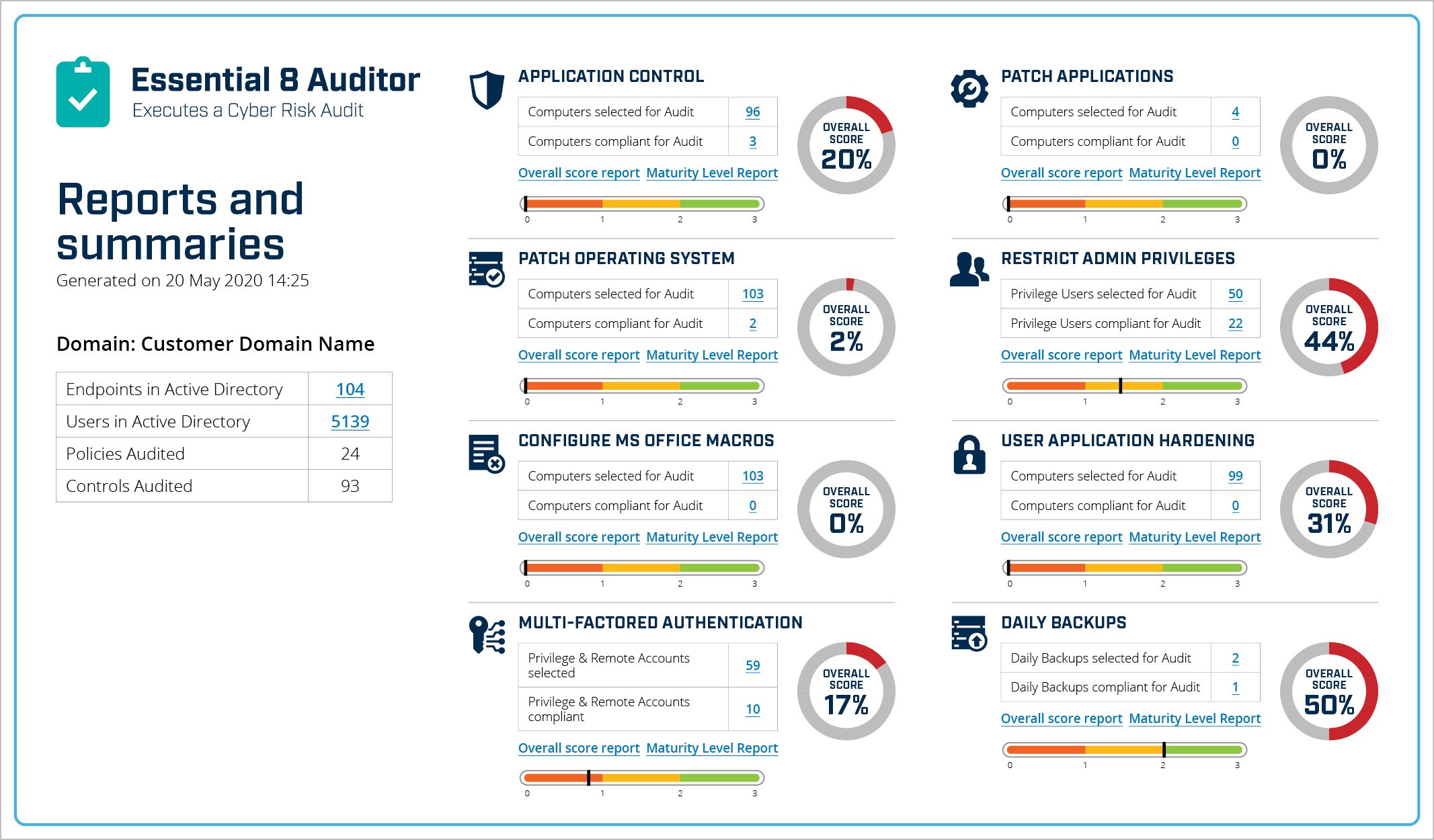
Essential 8 Auditor – Security Control Summary Dashboard
The tool is self-install, and can be implemented and operated by IT staff. Data and evidence is collected from across the environment to produce outputs that include identification of areas of non-compliance, performance metrics and cyber maturity scores. Results are exportable, for inclusion in audit reports or for sharing with security team colleagues and wider business stakeholders locally and remotely.
You can watch a short (3.5 minutes) video overview of the Essential 8 Auditor here:

Uses for the Essential 8 Auditor
The Essential 8 Auditor can be used for a number of purposes:
- Internally, to determine an objective measure of cyber risk exposure
- Internally, forms the baseline for annual compliance reporting and Cyber Risk Attestations
- Auditing tool for Security Consultants, Security Auditors and Risk & Compliance Managers
Find out more
If you would like to see a demonstration, discuss the solution’s capability further or find a reseller please contact us. Alternatively, you can visit the Essential 8 Auditor page here:
https://www.huntsmansecurity.com/products/essential-8-auditor/
 About Huntsman
About Huntsman




