On the 1st July 2019, the Australian Prudential Regulatory Authority (APRA) Prudential Standard CPS 234 came into effect. APRA CPS 234 mandates organisations under APRA’s jurisdiction implement an information security management programme to deploy multiple layers of cybersecurity controls such that if one control fails, others limit the impact of a breach – or as we know it in the security industry, defence in depth.
Top-Down and Bottom-Up Cyber Security
From an entity perspective, roles and responsibilities in relation to information security must be clearly outlined by management. The Board must explain how they will engage in information security matters, including how they have delegated responsibilities, how risks are escalated and what kind of reporting is required (schedule, format, scope and content).
Organisations must ratify the policy framework they intend to use, and it must be reported on to show the Board and senior management areas of non-compliance so they can investigate and remediate through their management structure. The Board is also responsible for ensuring the people undertaking information security roles within their organisation are appropriately skilled and experienced to undertake their duties – which means they cannot just pile the security responsibilities on an existing manager, unless that person already has suitable knowledge and qualifications to take on security.
Further to this set of board-level governance requirements, entities are expected to implement management systems that allow them to fully test security control effectiveness, providing regular assurance checkpoints and allowing the board to challenge management on the efficacy of control coverage. In part, they achieve this by monitoring and internal auditing, where they assess controls against an agreed baseline.
At the sharp end of the organisation’s security management system, APRA has asked entities to have proven, tested security mechanisms in place to promptly detect and respond to real and potential cyber threats. Furthermore, detection mechanisms such as event collection correlation and logging should be used to identify potential incidents and monitoring should be used to identify unusual behaviour, allowing the entity to preserve digital forensic evidence. In the case of protective monitoring, the solution should consider the broadest possible set of events, from sensors operating at the physical hardware layer through to frontline business activities, such as payments and user access modifications.
APRA calls out monitoring techniques to include baselining of activity to determine what normal looks like, combined with more traditional security information and event management (SIEM) style logging and alerting to detect anomalous or suspicious activity. Also included in their recommendations are unauthorised hardware scanning solutions, unauthorised software and configuration changes, and a solution to alert when an activity breaks an accepted threshold, such as the amount of data a device sends out of the network, the loading on a database server or unusual communication out to a remote location, such as outside of Australia.
Ongoing Monitoring and Remediation is Critical
APRA-regulated organisations will undoubtedly take this new set of regulatory compliance requirements seriously, and the guidelines will help many of them set appropriate targets for their security programmes. The standard allows them to elevate their security posture to a well-managed and mature level and give their shareholders and customers some level of assurance they treat their information with care.
An ongoing problem for many organisations is that when they go through a security uplift and achieve their goal of completing the implementation of systems and processes, they proceed to drift out of compliance between annual audits. An example of how this can happen is in the world of security patching. On the day systems are audited for patch compliance (i.e. checking if systems have the latest security patches) an organisation may be fully compliant – a great result. However, the audit won’t show that compliance was only achieved in the last few days, or that a last-minute race to get them all applied before the audit only started two weeks preceding the audit. For the rest of the year, it may well have been that the organisation was one, two or even six months behind in their patch deployment, which means they were carrying all that information risk by leaving critical systems and information exposed.
Even in the patching example, it’s unlikely that the organisation actively chose to ignore their security requirements, rather operational priorities took over, where keeping systems running and access available outweighed the immediate concerns about compliance. Only when the operations management team started preparing for their audit did they kick their patch compliance programme into high gear.
For this reason, it’s important that organisations look at continuous monitoring for senior management, where the Board or executive management layer of the organisation can see where major areas of non-compliance exist. This enables them to prioritise resources on the greatest risks to the organisation.
Technology for Real-Time Compliance Reporting
To create a Board-level view of control compliance, organisations can adopt a security scorecard approach, where the scorecard reports on the state of controls, such as patch compliance or the successful running of daily backups. By showing controls as a RAG status (red, amber, green), management is empowered to challenge the security team as to why something has changed from green to amber to red.
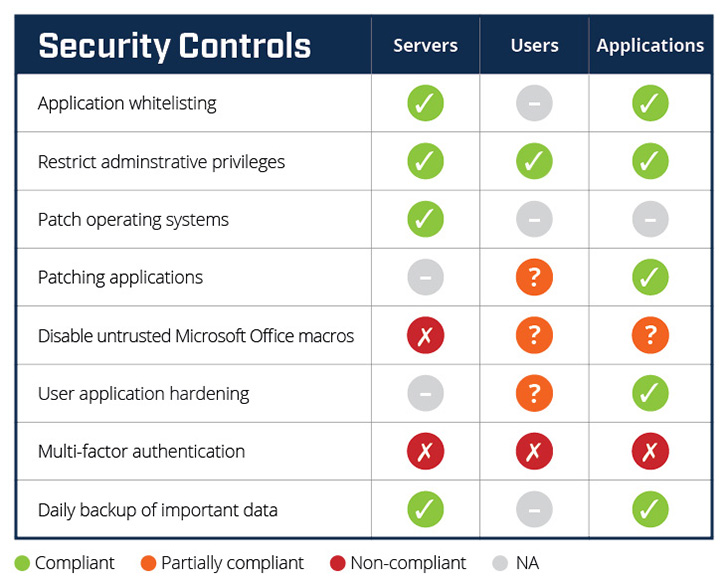
Figure 1 Huntsman Security’s Essential 8 Scorecard – an ideal solution for APRA CPS 234
This contemporary approach to security monitoring provides continuous, real-time feedback to help defend against cyber attacks. In the event that an attack is successful, it also supports limiting the extent of an incident and recovering data and system availability so the business can continue to operate without interruption.
Security Scorecards and Policy Frameworks
When choosing a security scorecard, it is critical to ensure that it’s aligned to a recognised security policy framework. Any reporting must cover the primary areas of interest to ongoing cyber security health. The Australian Cyber Security Centre’s ‘ACSC Essential 8’ framework is an excellent model to benchmark the effectiveness of your organisation’s security controls. The eight security controls are internationally recognised as fundamental to cyber resilience.
APRA CPS 234 regulated entities are obligated to test the effectiveness of their information security controls through a systematic testing program. By choosing a solution that continuously monitors and reports on security control effectiveness they will have a live view of current risks. When the annual audit comes around, there should be no surprises, resulting in costly remediation programmes or, worse, an order to cease trading until issues are resolved.
 About Huntsman
About Huntsman



