In late November 2021 an APRA Insight report noted that it expected boards to have the same level of confidence and capability in reviewing IT cyber security issues as any other business issue. It also noted that during the preceding period, described by the Australian Cyber Security Centre (ACSC) in their Cyber Threat Report 2020-21 as having seen heightened complexity and sophistication in cyber attacks, an APRA survey had confirmed a definite need for boards to improve their oversight of cyber resilience.
Little evidence of active management of cyber security information
The APRA survey sought to assess the availability and understanding by boards of the cyber security information and controls necessary to improve cyber resilience. Banks, superannuation and insurance organisations were included in the pilot survey. The observations were that boards need to play a more active role in:
- Reviewing and challenging information provided to them about cyber resilience;
- Ensuring their organisations can recover from a high impact attack – like ransomware, and
- Ensuring cyber security controls operate effectively across their supply chains.
APRA found that there was little evidence of boards actively reviewing and challenging cyber information provided by management. Sometimes the information was not fit-for-purpose or easily accessible. On other occasions, key information about the operation and effectiveness of security controls was not available at all.
Reports to the board should provide accurate visibility of cyber security KPIs
To improve board performance APRA suggested a set of questions for boards to review and better challenge the security information provided to them, including:
- What are the security vulnerabilities and threats facing the organisation?
- What is the organisation’s current cyber security readiness?
- What is the health of information assets and security controls?
These questions are undoubtedly instructive but, in an environment where the cyber threat landscape can change overnight, the effective communication and interpretation of cyber security information needs to be clear, accurate and timely. A cyber security report prepared for the board some weeks ago is a report about another time; and results of an annual audit conducted months or more ago are largely irrelevant.
In the mid-90s, the Kaplan and Norton’s Balanced Scorecard (see summary) enabled business strategy to be transformed into a management process with the use of performance measurement and reporting dashboards. KPIs were established and changes in those measures were used to support systematic management review and decision making. Today, with evidence-based decision-making being a part of everyday business activities, it is time that organisations use similar style scorecards to quantitatively measure and inform the management of cyber security; with the empirical measurement of KPIs, gaps in security controls and mitigation efforts, trends over time and a summary of residual risk for risk management and resilience efforts.
Translating cyber security information into quantitative management metrics
The ACSC Essential 8 cyber security framework can help here. The Essential 8 is an easily accessible and acknowledged international security standard that incorporates answers to many of the key technical questions that directors need to ask about the effectiveness of their cyber security strategy and their security controls.
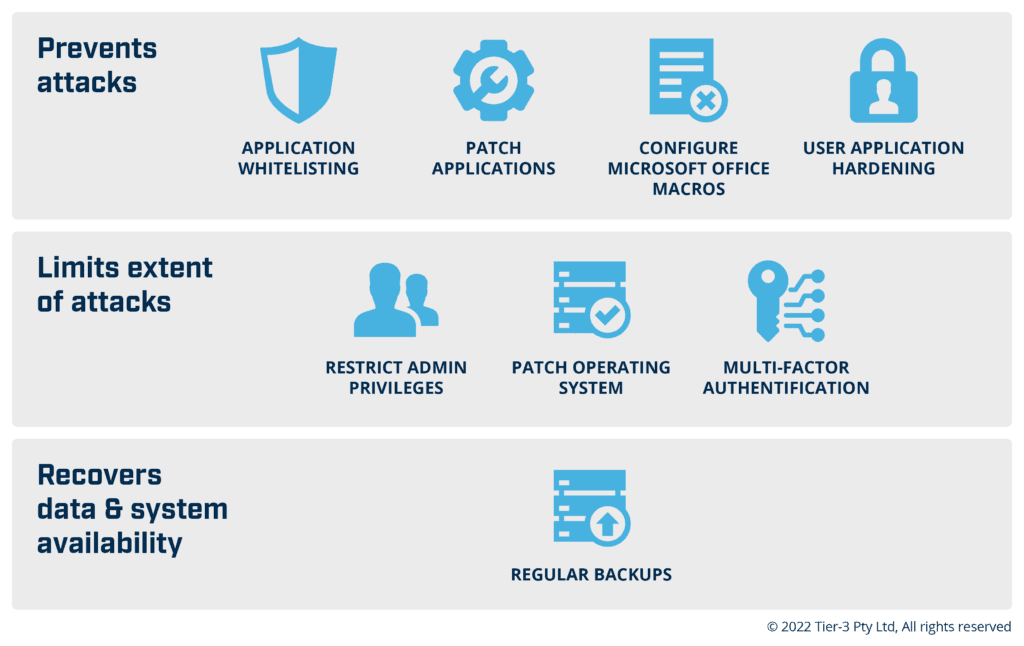
Figure 1.0 The ACSC Essential 8 Cyber Security Framework
Equally important is that information about these technical controls can be automatically measured and reported in a scorecard format to visualise the state of each security KPI and so drive evidence based cyber security risk management decision making and board oversight. A standardised scorecard format quickly informs the key cyber security KPI scores, provides traffic light metaphors for performance and informs trending for the timely management of cyber resilience. It also highlights to executives and boards matters of concern or weakness that might require urgent clarification or intervention.
The growing importance of the timeliness of cyber security reporting to boards
ACSC in their Cyber Threat Report 2020-21, made the important observation that “the increasing frequency of cybercriminal activity is compounded by the increased complexity and sophistication of their operations”. This highlights the increasingly dynamic nature of the cyber threat environment and the increasing need for more timely risk measurement, reporting and board decision making.
It’s true that dialogue with management to challenge and review cyber security information is an important task of director oversight but increasingly the success of resilience efforts depends firstly, on the accuracy, timeliness and relevance of the available security information and secondly, the rigour of decision-making. Reflective of the fact that cyber security circumstances can change overnight, there is a growing demand in some sectors for near real-time cyber security reporting and decision-making. The Securities and Exchange Commission (SEC) in the US, for example, is currently considering mandated on-going cyber security disclosures for public companies.
There is an unquestionable need for increased frequency of information updates on cyber security controls and levels of resilience. As any security engineer will tell you, the day after “patch Tuesday” is “exploit Wednesday” when a new set of vulnerabilities is revealed to the very real concern of security and risk teams. All stakeholders need to understand that reality – there is no such thing as set and forget in cyber. Additional questions and rigour in the collection and analysis of the information provided to boards is important but the accuracy and currency of that information are key determinants of the effectiveness of a cyber resilience program.
Not all controls are easily measured quantitatively
The APRA survey revealed that not only was key cyber security information not available for some boards to adequately interpret and understand, but information on “measures” of controls like testing of data backup and incident response programs, was limited. More than 1/3 of respondents (a term which still suggests a degree of subjectivity in the survey) admitted to not testing data backups for more than 12 months. Again, APRA suggests that: Boards should enquire as to the status of back-up and recovery testing and their adequacy.
As with technical security controls, metrics about the extent and frequency of staff cyber security training, and the data back-up and incident recovery programs, can easily be added to a cyber security type scorecard and provided as part of a broader report verifying the effectiveness of each security control. Scorecards that include both technical and non-technical cyber security controls and their effectiveness are already available for senior managers and directors to assess their preparedness for a ransomware attack.
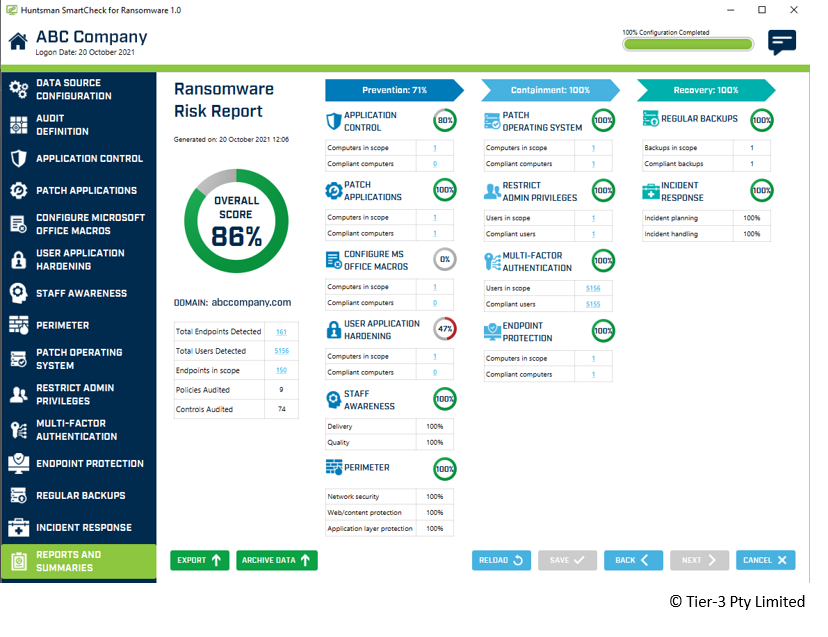
Figure 2.0 A scorecard measuring the effectiveness of 12 key security controls for resilience against ransomware
Poor cyber posture by a 3rd party supplier can be contagious
The final concern raised in the APRA survey was that organisations should ensure that information about security controls is effectively communicated across supply chains. The interdependence between organisations in the finance sector is already significant and will only grow as increasing numbers of customers access the greater innovation, competition and productivity offered, for example, by Open Banking. The security implications for the financial sector are significant: increased attack surfaces, securing APIs that enable access between systems and ongoing protection of sensitive data, will challenge 3rd party service providers and the overall resilience of the sector.
Financial institutions and their downstream 3rd party service providers need assurance that trust between parties and cyber security maturity levels are being maintained. It’s now, however, just as important that your high priority 3rd party suppliers undertake similar quantitative security assessments and share those results between supply chain participants. Any lack of rigour in the measurement of the effectiveness of cyber security controls of 3rd party providers puts the resilience of all stakeholders at risk. APRA noted that the heavy reliance by many organisations on self-assessments and questionnaires by their service providers limits the ability of organisations to verify the adequacy of their cyber security posture.
Again, the use of the ACSC Essential 8 security framework and regular measurement and scorecard reporting, as part of the broader communication of security information and resilience, will alert the board of any matters needing attention.
How can boards better challenge and review security information?
In their November 2021 Insight, APRA recommended that boards review and challenge security information on cyber resilience. It encouraged entities to test the effectiveness of their data backups and business recovery plans, and to ensure verifiable security information is available to participants across the supply chain.
These are the ambitions of regulators everywhere. The question, however, is how is this best achieved by professional boards very familiar with the assessment and management of risk, but often not the persistent nature of cyber security risk. Risk committees and advisors can always assist but it’s paramount that cyber security risk and resilience management information is timely, couched clearly and accurately, in the familiar lexicon of risk. Familiar graphical reporting, key performance indicators and trends against internationally acknowledged markers can inform on the quantitative status of resilience efforts. They can also prompt enquiry and investigative rigour by boards as they guide the management and oversight of an, as yet, unfamiliar but significant risk to the digital enterprise.
 About Huntsman
About Huntsman




