Too many boards still lack visibility or understanding of the problems, while internal audit functions can lack the specialist skills to challenge boards and management to plug urgent gaps.
Geoff Summerhayes, APRA Executive Board Member
Australian Prudential Regulator, APRA, has announced its intention to tighten its grip on cyber governance, as part of its newly released Cyber Security Strategy for 2020 to 2024. The financial regulator plans to elevate the importance of good cyber hygiene and board accountability for cyber exposure by, if necessary, formally enforcing adherence for those organisations that don’t meet the new requirements.
Eighteen months ago, APRA released a cyber security standard, CPS 234. Yet as stated in a recent speech, while they directly supervise 680 organisations, there is a broader community of up to 17,000 interconnected entities in the APRA ecosystem that will be affected by the changed requirements.
As a regulator, it’s becoming increasingly important to set the tone for security-related compliance standards and oversight, which is why APRA’s lead is so important. The new strategy lists APRA’s three new primary areas of strategic focus, in its ambitions to “…make a step change in Australia’s financial system cyber resilience.”
APRA Strategic Focus Areas
APRA’s strategic focus areas are:
- Establish a baseline of cyber controls covering prevention, detection, and response;
- Enable board and executive oversight and direct correction of cyber exposures; and
- Rectify identified weak links within the broader financial services eco-system and supply chain.
Establishing a baseline of foundational controls is key to effective cyber security. APRA’s stance is that these baseline controls are non-negotiable. By improving cyber hygiene through increased monitoring of controls APRA hopes to eliminate careless and unnecessary cyber exposure for organisations.
Board and executive-level oversight compels those in charge of financial institutions to oversee and take accountability for the overall cyber resilience and even risk mitigation within their organisations. APRA promises to enable this by formulating what they call “sound practice guidance” and ensuring greater oversight of those accountable for the implementation of the new requirements.
Anyone in cyber security knows how important, yet challenging, 3rd party or supply chain security is, the third area of strategic focus. Even if a business has vastly improved its own cyber resilience, financial services organisations, like any other sector, exist within a network of suppliers, partners and subcontractors, all of whom can share and process information, or store and transmit customer data. Initiatives like open banking and the high levels of digitalisation in the sector have also added to these risks. APRA acknowledges it’s not the easiest requirement to meet, so they will develop in consultation with suppliers and regulators, a set of third-party assessment criteria and information assurance practices that entities can use to govern their supply chains.
Maintaining Baseline Controls
APRA’s push to establish a set of baseline controls is an important one. Their focus on enabling this sort of innovation is crucial to the success of their ambitious plans to strengthen the cyber posture of their market sector. Cyber security is not a set and forget problem. The threat landscape continues to evolve and so sharing information learned from regular security control assessments will help to ensure the efficacy of any prudential framework for cyber security.
The simple decision to benchmark cyber security controls immediately establishes a systematic process and ensures security posture improvement for any organisation. Controls, however, like the mechanics of a car, need maintenance; without proper care and attention they become less effective and even fail.
The Australian Cyber Security Centre’s Essential Eight, for example, is one such security framework which sets out the guidelines for security baselining of Australian Government entities. The Essential 8 is regularly revised and updated to maintain its efficacy against changing cyber vulnerabilities. One control in the framework is that organisations implement application patching (or application control). At its most basic, this means they must patch all applications used by their business. Once the control is implemented and all applications patched, the business is compliant with that control.
As time passes, new applications are implemented and new hardware and peripherals are installed, which can result in reduced levels of patch efficacy. The problem is that this constant requirement is hard to stay on top of, and as a result, your cyber resilience is being continuously diminished. Security risk and executive teams need to be aware of this and find new ways to manage the risk.
Regular or Continuous Assessment
You may choose to regularly compare current control performance levels against an original baseline measurement to determine any changes over time. These changes can then be used to inform periodic management decisions or, for more mature organisations, become part of a broader security improvement program.
In some cases, monitoring may be procedural (manual), where an auditor checks compliance once a quarter, or even more frequently. In other cases, such as with the Essential Eight controls, it may be possible to implement a technical solution that monitors security control implementations for any gaps and highlights any shortfalls. With reports that clearly identify current maturity level measurement for each of the security controls, both operational and senior executives (internal auditors and board members) can have clear visibility of the cyber security exposure and any corrective action that is necessary.
Depending on nature of the business and its assessed level of cyber risk some operational or senior executive team members may determine that the organisation should monitor the state of its security controls continuously. This could be through an abundance of caution or more likely because the assessed outcome a successful cyber attack was so costly that an ability to detect and then immediately respond to a cyber hygiene issue was seen as paramount. This may be the case for large financial institutions.
Huntsman Security’s Essential 8 Scorecard (see Figure 1) can quickly identify gaps in implementation and compliance with each of the ACSC’s controls, highlighting the technical issues to security management teams while summarising the overall state of cyber compliance to the board. It’s vitally important that the same information is presented in different ways to different audiences, thus the board level view of the security posture is based on real metrics gathered from running systems.
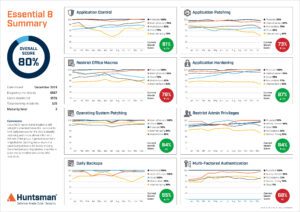
Figure 1 – Essential 8 Scorecard Summary
APRA’s “community of cyber defenders”
APRA concludes: “By sharing information and expertise, pooling resources and taking prompt action to plug gaps and fix weak links, we create a community of cyber defenders that is greater than the sum of its parts.” In doing this, APRA believes its members will build resilience across the whole of the financial ecosystem. If they can get the right blend of shared expertise, coupled with consistent processes and well-implemented technical solutions, this future state is achievable.
For more information on how Huntsman Security’s Essential 8 products can help financial services organisations enhance their cyber hygiene, improve their security posture and deliver control back to the board, contact our team.
 About Huntsman
About Huntsman



