The result of three recent cyber resilience audits conducted by the Australian National Audit Office (ANAO) was released on 4 July. The report showed some encouraging results, but also highlighted some concerns. The need for real-time visibility of cyber security posture is becoming increasingly evident.
In these modern times where everything is available ‘now’, why does cyber security still rely on external auditors to give an organisation objective visibility of their cyber security posture? Like any good performance management programme, there should be no ‘ta-dah’ moment, only full disclosure and continuous development in the pursuit of excellence.
The Audit Process
ANAO reviewed three well-known Australian government enterprises. The purpose of the audit was to conclude whether these organisations manage cyber security risks appropriately (in line with their own risk arrangements), whether they manage cyber security risks in line with the Australian Signals Directorate’s (ASD) Information Security Manual (ISM), and whether they have a culture of cyber security resilience.
ANAO investigated how the organisations met the requirements of their own security risk management frameworks, including a detailed assessment of the controls implemented to mitigate named risks. Furthermore, ANAO looked at whether each organisation’s approach to security management aligned with ASD’s ISM, and whether each one has a cyber security culture of, “shared organisational attitudes, values and behaviours,” regarding cyber risks.
ANAO’s primary focus was on each entity’s corporate ICT platform, as well as any systems considered critical to their operation (this selection was done in consultation with the entities themselves).
Cyber security risk frameworks
Adopting a recognised cyber security risk management framework provides assurance that an organisation’s chosen set of security controls are comprehensive and robust. It enables an organisation to benchmark its cyber security posture against said framework. Secondly, with residual risk identified, CISOs and risk executives can prioritise actions to manage the risk.
There are a number of these frameworks in use around the world, many with significant similarities; ACSC Essential 8 (Australia), NCSC Top 10 (UK) and NIST (USA).
Australia’s ACSC Essential 8 Framework incorporates the eight most fundamental mitigation strategies. It is simple, measurable and the ‘Top 4’ of the ‘Essential 8’ controls alone have has been found to mitigate 85% of targeted attacks (Application Whitelisting, Patch Applications, Restrict Administrator Privileges and Patch Operating Systems).
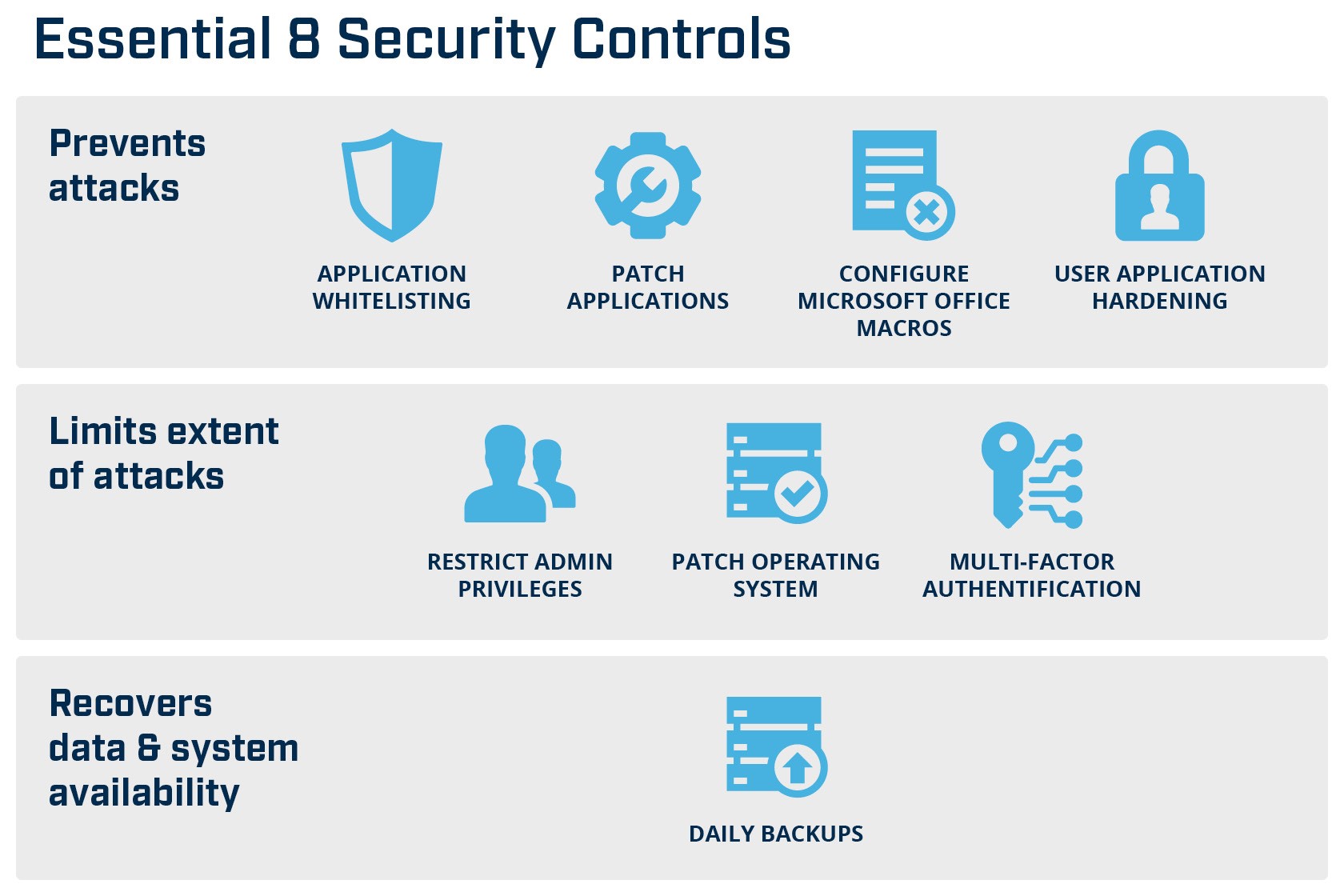
ACSC Essential 8 Framework
The ANAO found that the two organisations that followed a recognised framework were more resilient than the one that did not. ANAO’s assessment of risk management framework compliance includes investigation of:
- Enterprise-wide governance arrangements
- Information security roles assigned and responsibilities communicated
- ICT security incorporated intro strategy, planning and delivery of services
- ICT operational staff understand the vulnerabilities and cyber threats to the system
- Integrated and documented architecture for data, systems and security controls
- Systematic approach to managing cyber risks, including assessments of the effectiveness of controls and security awareness training
Alignment with the ISM
The audit identified that the two cyber resilient organisations implemented controls in line with those proffered in the ASD’s ISM, including those of the ‘Top 4‘ and the ’Essential 8‘ while the third company did not fully implement these controls, rather they had implemented two: patching ICT applications and minimising privileged user access (both of which are highly effective).
Some of the controls are harder to implement than others. For example, Application Whitelisting is notoriously difficult to get right as it often has a negative impact on running systems and critical ICT service management processes such as software deployment. However, the Top 4 controls are mandatory for government entities so must be prioritised.
ANAO assesses controls and benchmarks performance against a set of measures:
- Controls not in place and no dispensation authorised by the Accountable Authority
- Controls not in place but dispensation is authorised by the Accountable Authority
- Controls not in place but entity is actively implementing, with a minimum of design deliverables in evidence
- Controls in place and meeting control objectives
- Controls in place and maintenance is part of business processes, including monitoring and taking corrective action as required
It is interesting to note that whilst controls are in place and meeting control objectives, best practice dictates that there must be a maintenance programme as cyber resilience can change at any time.
Cyber resilient culture
The cyber resilience of an organisation’s culture is the third area that ANAO assesses in its audit process. The thirteen behaviours and practices that are reviewed sit within the following areas:
- Establish a business model and ICT governance that incorporates ICT security into strategy planning and delivery of services
- Manage cyber risks systematically, including through assessments of the effectiveness of controls and security awareness training
- Task enterprise-wide governance arrangements to have awareness of cyber vulnerabilities and threats
- Adopt a risk-based approach to improvements to cyber security and to ensure higher vulnerabilities are addressed
Take control of Security Controls
What is clear from the ANAO audit process, it that an organisation’s actual cyber security posture may not be what a self-assessment deemed it to be. An objective and current measure of cyber maturity is key to maintaining your organisation’s defences.
Security scorecard technology can help in the area of security control effectiveness. Having a capability that can monitor, measure and report on cyber health means your business can be fully aware of its residual risk to then prioritise and manage. You can explore our Essential 8 Scorecard here. It has been designed to benchmark performance against the ACSC Essential 8 framework.
The importance of security monitoring
There is one very important observation of the audits conducted by the ANAO; the use of security monitoring to detect cyber threats. This is particularly relevant to organisations that cannot implement a security control such as blocking or whitelisting. With proper configuration by your security team it can be a great substitute for a more obvious control. If you cannot directly block something, then knowing when it’s being targeted by an attacker so that you can block that connection or lock that specific access down can be equally as effective.
A Security Information and Event Management (SIEM) system will provide that failsafe where threats can be detected anywhere within the organisation, not just where the active security controls are in place. What’s considered baseline normal behaviour can be assessed and a picture developed of what normal looks like, that way the SOC team can act when they see something suspicious.
 About Huntsman
About Huntsman



