Australia’s Federal Government Attorney-General’s Department is taking a new approach to cyber security audits when assessing cybersecurity preparedness in government. Until recently, each department’s security controls were audited against the Protective Security Policy Framework (PSPF), with adherence to controls recorded as either a yes or no answer.
However, the evolution of cyber security audits, has seen the creation of a new maturity model that reduces the 36 mandatory requirements within the PSPF to just 16, and the assessment will no longer be a yes or no answer; instead, it will require a detailed understanding of how well each of the controls is implemented, on a Capability Maturity Model Integration (CMMI®) -style maturity scale.
Maturity models are an excellent way to show the real effect of security readiness since security control implementation needs to be holistic and diligent to ensure coverage across all critical areas of the business. Indeed, the forthcoming release of the United States Government’s Cyber-security Maturity Model Certification (CMMC), a Department of Defense certification process for the Defense Industrial Base sector to enhance the protection of sensitive data, is introducing plans to include a certification element that verifies implementation of cyber-security requirements.
Let’s look at why organisations should adopt a reliable framework to benchmark and continuously check security control performance.
Cyber security audits are not a tick-box exercise
Every organisation knows what an audit can mean: a week of tedious questioning by an external party, where they look for implementation evidence for specific controls and processes. Questions often don’t uncover implementation reality, so while goals are for the betterment of all, audits frequently don’t detect underlying issues and offer a false sense of security.
Furthermore, just because a process is in place, it doesn’t mean it gets followed, and even if the team that the auditor speaks to always diligently follows the correct workflow, another team in another state might have decided to do something differently, forgetting a crucial step that renders the process ineffective. If this is a process for applying critical security patches to all key business applications within 24 hours, for example, then failure to do this exposes the business to undue levels of security risk.
In today’s landscape of ever-present cyber threats, it is dangerous for a business to approach a security audit as a tick-box exercise; the stakes are too high. Instead, the audit should be used as an opportunity to build cyber resilience. Aim to turn security reviews into positive experiences that help implement a robust security framework across the enterprise, utilising each control definition to align the outcomes to the goal of tangible threat protection.
What if you don’t have a cyber security audit requirement?
Most industries are moving towards adoption of better cyber security requirements, and over the past few years we have seen security frameworks appear in all sorts of places, such as the shipping industry, aviation, automotive, health and across the broader government ecosystem (both at federal and state levels). However, it’s still the case that not every business has a security audit framework with which they need to comply. Is there something that can be adopted that’s not too onerous or costly to comply with but ensures you are improving your security posture enough to protect against most security threats?
As far as a useful framework for all businesses of all sizes goes, the Australian Cyber Security Centre (ACSC) maintains a list of eight security controls, that once implemented, will protect organisations against a massive 85% of targeted cyber attacks. A list of security controls was published back in 2017 containing 37 security strategies organisations can adopt to improve their chances of keeping hackers out of their systems: you’ll find this publication here.
ACSC realised that while all 37 security controls provided good defensive value, it was an onerous goal for government departments to meet, especially if they were starting from a position of low maturity, and many wouldn’t know where to start at all. Hence, they published a new set of guidelines called the Essential 8, which is essentially the most impactful set of eight security controls that any organisation (government or private, no matter what size or industry) can implement to ward off the majority of targeted cyber attackers.
Use the Essential 8 as your security target
The Australian Signals Directorate considers the Essential 8 Framework, if implemented correctly, as providing the most effective cyber resilience ‘baseline’ for all organisations, no matter the size or shape. The controls that make up the Essential 8 are all within reach of even the smallest organisation but are equally as applicable to the largest listed companies, turning over billions of dollars.
Each control offers a practical approach to raising the security posture with a specific goal in mind. For example, user application hardening details how applications should be locked down, and user access restricted to just the data they need to do their job. This might seem obvious, but most of the time, when applications are installed all users have access to all functionality, which in some cases can mean they have access to administrative functions.
By taking the time to restrict access to just the data users need to do their job and ensuring that only a couple of trusted administrative users have the rights to change what the general user population can do, you can restrict both external threats, if users are hacked, and also insider threats if users turn malicious.
Look at the rest of the Essential 8 controls and you’ll quickly see why they are so powerful.
Continuous monitoring and real-time visibility using scorecards
Once you see the value of the Essential 8, the implementation should be planned with continuous monitoring in mind. A fundamental flaw of the traditional auditing approach is that the day after the audit completes, compliance can change; you could go for a long period of time (until the next audit) without realising you are exposed to excessive levels of risk.
Huntsman Security recognised this issue and looked at how we could help businesses establish a method to monitor continuously and report on compliance against these controls. The goal was straightforward: identification of real-time deviations from a known, recognised acceptable control baseline.
Taking a progressive approach to security scorecard technology, we developed a capability that allows organisations to continuously monitor security control effectiveness and show you exactly where you have weaknesses or gaps in security coverage, even if you have a limited number of skilled security staff and a modest security budget.
Security scorecards offer several outcomes from which a business will benefit. They communicate the live security posture in real-time to all levels of management, aggregating data for executives in easily understood dashboards while showing the detail at an operational level to help direct and prioritise remediation activities. Maturity can also be calculated, based on a set of KPIs like those defined by the ACSC in the Essential 8 Maturity Model, which helps businesses (and government departments) meet their regulatory compliance objectives, such as those we mentioned early from the Attorney General’s new approach to PSPF auditing.
Huntsman Security’s Essential 8 Scorecard
Huntsman Security’s Essential 8 Scorecard continuously collects evidence from information and log sources across the ICT environment and measures the effectiveness of security controls against each of the Essential 8’s KPIs. This data is communicated in dashbords and reports, so a range of stakeholders have full visibility of the current level of cyber risk exposure.
For CIOs and Risk Managers, for example, the Essential 8 Scorecard provides a Trend Report that details the performance of each control over time, for different business units or domains.
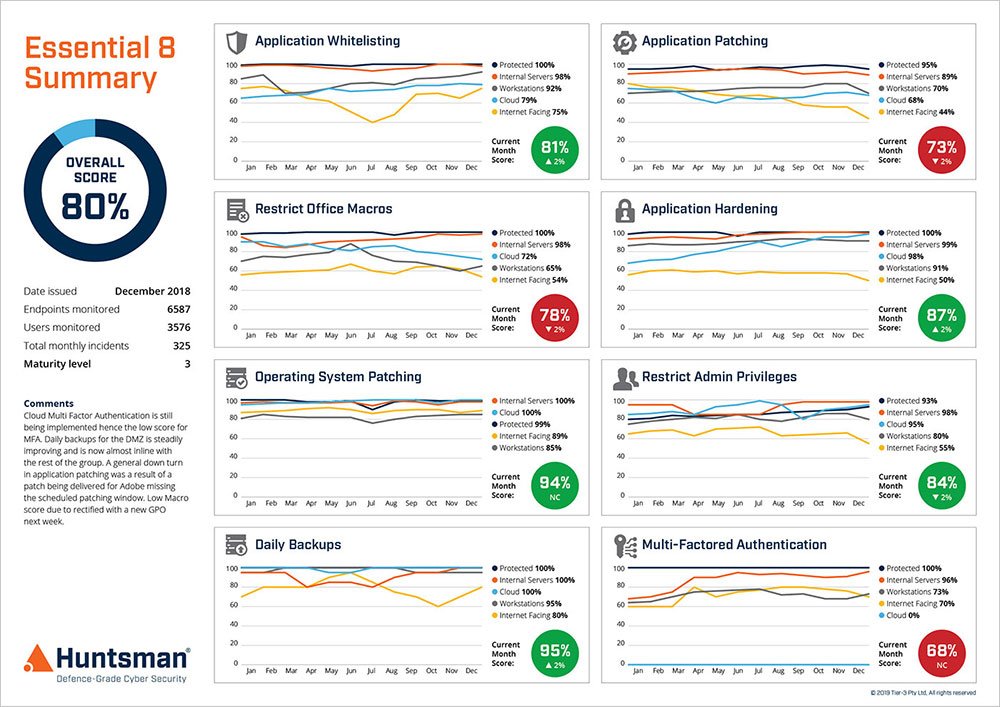
Essential 8 Scorecard – Performance Trend Report
For Information Security Managers, we provide a report giving detailed performance metrics for each of the Essential 8 mitigation strategies in relation to the Essential 8 Framework.
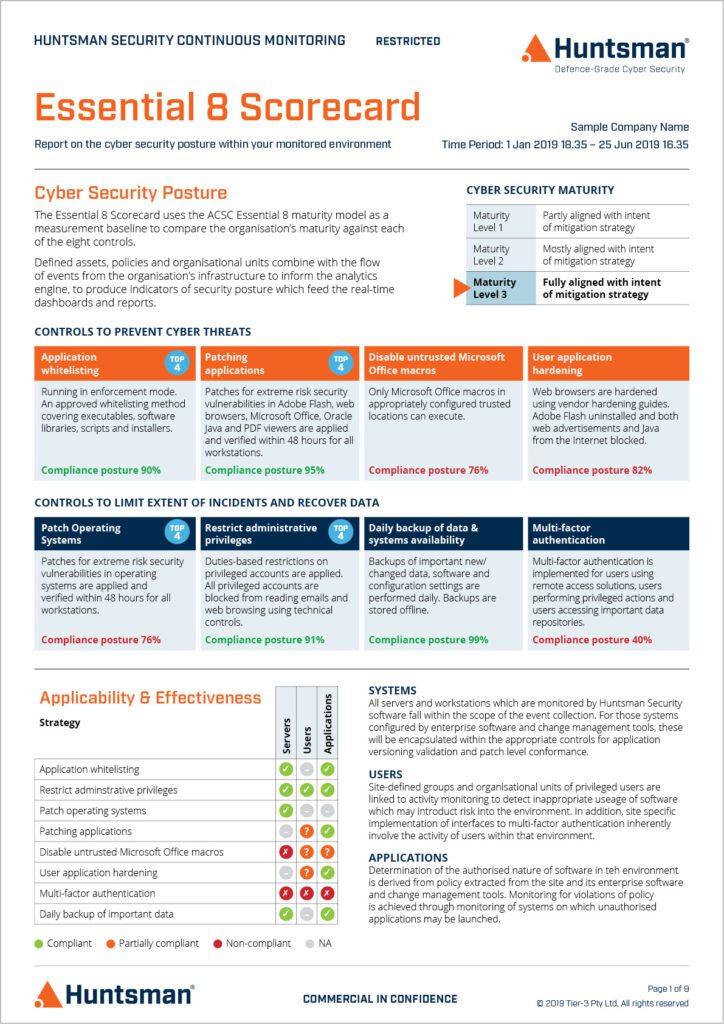
Essential 8 Scorecard Report
At an operational level, the ICT support teams have real-time visibility of what’s going on with regard to the compliance of each control; alerts notify when specific concerns arise, allowing better prioritisation of tasks related to risk exposure.
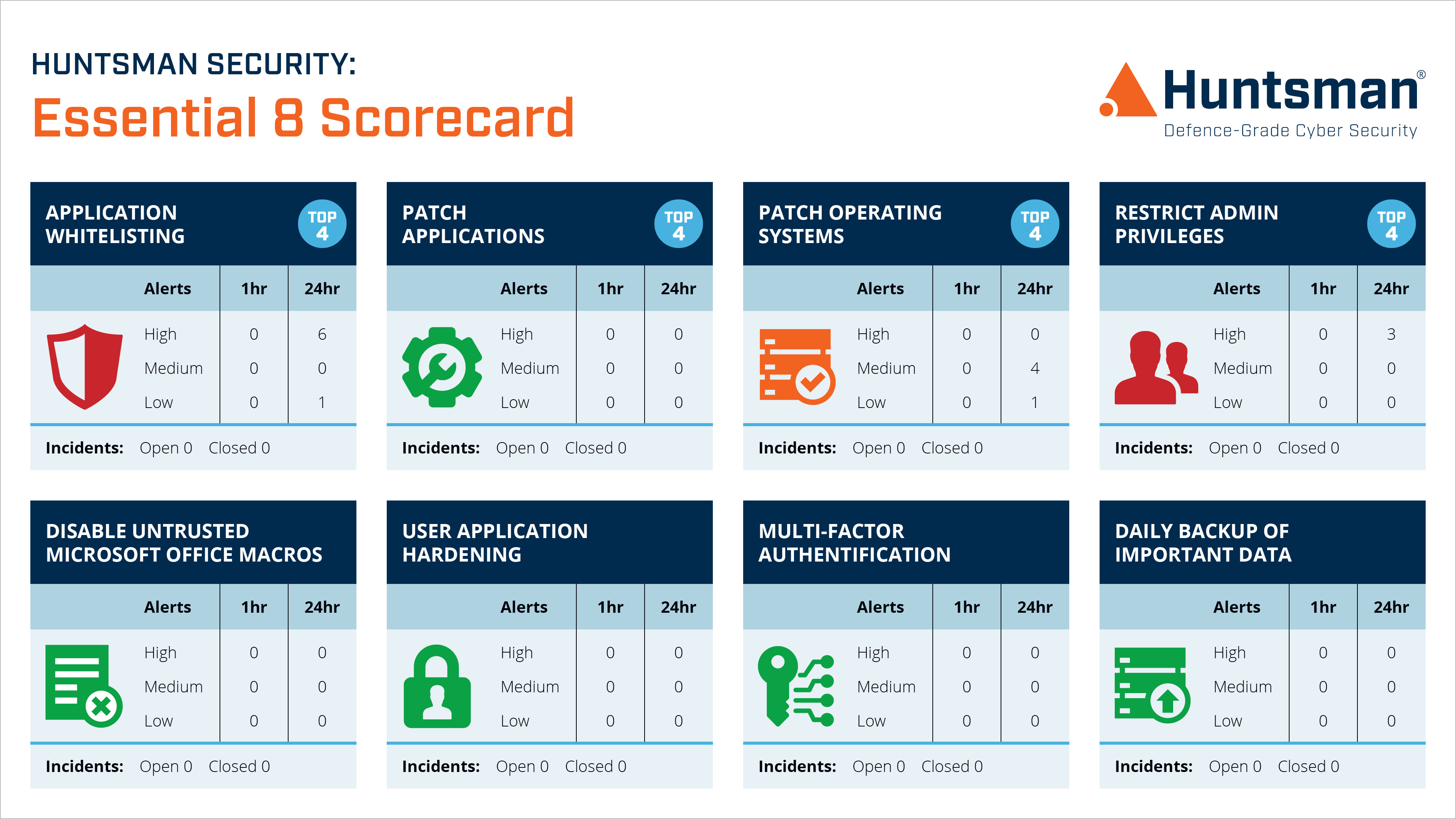
Essential 8 Scorecard – Operational Dashboard
Focus on having a reliable framework you can continuously monitor
No matter if you are a government department complying with the PSPF, or a small business wishing to make sure cyber attackers don’t steal your customer data, by choosing a reliable security framework like the Essential 8 you can continuously monitor, benchmark and improve your business’s cyber resilience against a known security baseline.
Effective performance measurement in cyber security is no different to any other business function, the more continuous and open the process, the greater the awareness and focus to improve it. Security control compliance, or as it should be known ‘security control effectiveness measurement’ needs to shift from annual audits towards a goal of real-time monitoring. Only then will your organisation benefit from the investment it makes in implementing security controls in the first place.
 About Huntsman
About Huntsman





