Cyber criminals are making the most of the spread of the Coronavirus. The financial services industry is being hit particularly hard, with attackers creating their own pandemic of phishing emails trying to steal money, personal information and intellectual property.
This is hardly surprising, given the value of their assets, and as their workers shift to remote access models and isolate themselves from their colleagues, the attack surface and opportunities for cyber attackers increases.
Cyber criminals attacking Financial Services
Phishing – a cyber criminal hobby
Phishing is by far the most prevalent threat during the current pandemic, with dozens of new domains registered to serve as the landing page for fake Centers for Disease Control and Prevention (CDC) broadcasts and World Health Organization (WHO) recommendations. Scammers claiming to be CDC officers with information on the virus, or information on a cure, are rife. Scam emails pretending to be from the WHO have been seen to contain a malicious attachment that installs a keylogger on the target’s machine and sends the keystrokes back to the attacker’s command and control system. Scams have already been seen relating to charities, financial relief packages, airline refunds, fake cures and vaccines, and the availability of fake testing kits. Clearly no topic is off limits.
Cyber security for remote working
We know that users need education, but businesses need to impose stricter controls over remote access working in their security architecture. In the rush to get everyone safely working remotely, many of the usual considerations we’d expect from a large-scale ICT project have been put to one side for the sake of expediency. Of course, that was the right decision, given the severity of the COVID-19 disease. However, all organisations should now re-look at their security model and consider better detection and response solutions for remote access.
Adopt a Risk Management Framework
We talk a lot about cyber hygiene, using the Essential 8 framework in Australia and the Cyber Essentials framework in the UK as two examples of basic controls all organisations should have. Financial services organisations are also encouraged to build good security governance models, that ensure any controls they use to protect the business are maintained over time. There is a need to automate cyber hygiene checks since many of the controls relate to underlying technology such as the organisation’s access control and authentication solution, their operating systems, backup solution, and the way they permit use of administrator privileges. In a time of much distraction, systematic processes provide focus.
Financial organisations that don’t yet have a security program in place should consider adopting the Australian Cyber Security Centre’s (ACSC) Essential 8 Strategies to Mitigate Cyber Security Incidents. By implementing and maintaining these eight, globally recognised, security controls, ACSC have found that organisations can protect themselves against approximately 85% of targeted cyber attacks, so they are the perfect baseline for financial services organisations to adopt.
Essential Eight Framework
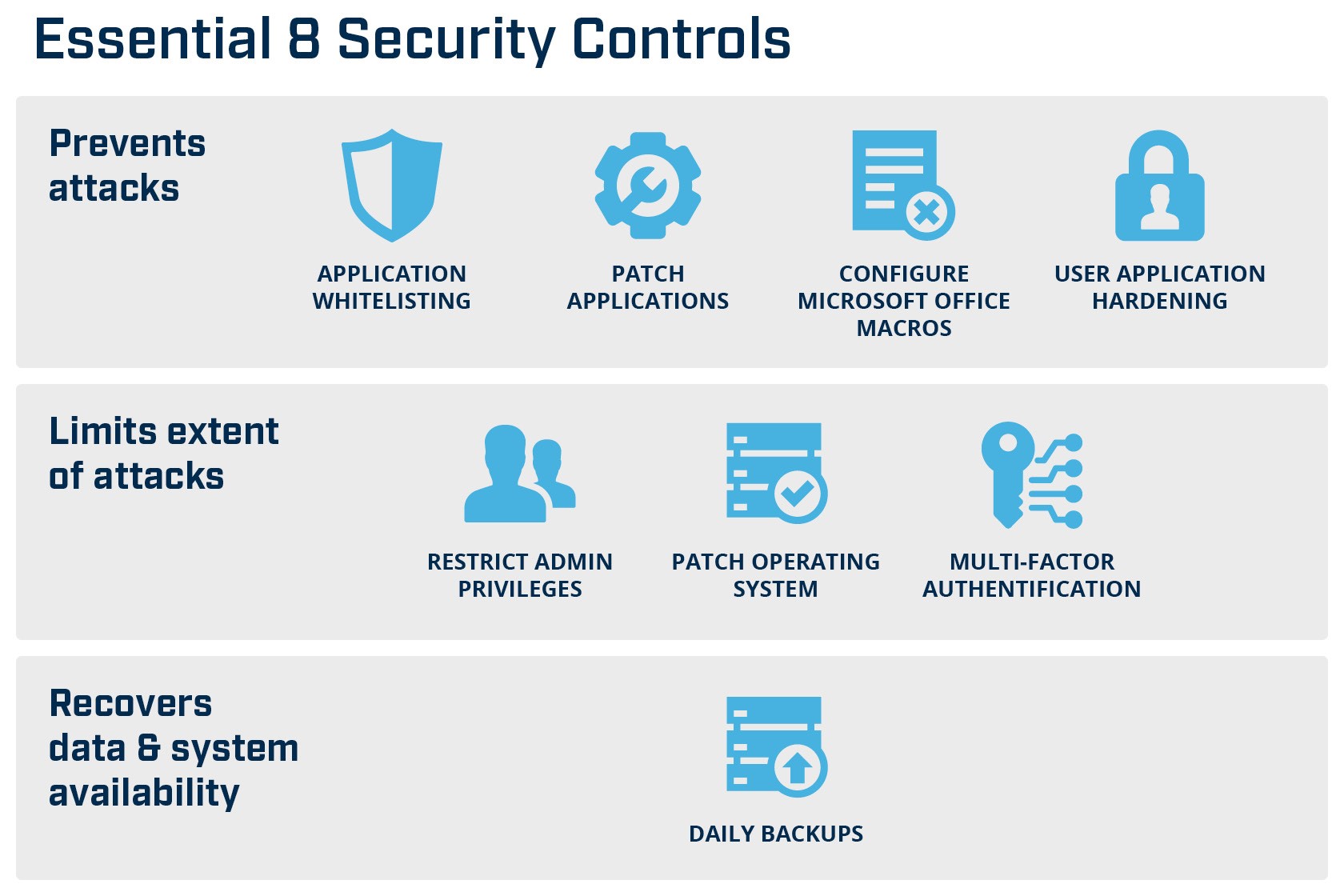
ACSC Essential Eight Framework
Implementing the Essential Eight security control framework should be a priority, so that project should take precedence over other security management activities that are in production. However, ACSC acknowledges that organisations need to determine how well they have implemented the controls, hence they released their maturity model aligned with the Essential Eight. This model has three maturity levels, where controls can improve from partly aligned with the intent of the mitigation strategy, through to fully aligned.

Fully aligned means the control is implemented everywhere and is fully protecting the whole organisation using the best configurations and settings. For example, with Application Whitelisting, to be fully aligned, it needs to be on all servers to restrict the execution of executables, software libraries, scripts and installers to an approved set. Microsoft’s built-in Application Whitelisting solution is called AppLocker and works on all versions of Windows as far back as Windows 2000, so there is no excuse for organisations not looking at this as an option if they use Microsoft technology.
Once the implementation project is finished and your eight security controls are rolled out across the business, you’re in a good spot. The issue you now face, though, is that enterprises doesn’t stop changing their ICT systems, security researchers don’t stop finding vulnerabilities, and cybercriminals never give up.
Financial services organisations understand the concept of assurance better than most, and assurance is what needs to be applied to their security posture. Assurance is often provided through audits and reports, with organisations expected to address negative audit findings within a fixed period. Audits are usually conducted on an annual basis, which for businesses processes is fine, however, ICT audits have adopted a similar schedule, and in the case of security this is much too little.
The issue is that the information security environment is dynamic, what is robust one day may not be the next. Businesses need to know as soon as a weakness appears, since the bad guys are almost certainly prowling the Internet looking for susceptible targets.
Patching – the puncture repair kit of cyber security
Patch compliance for example is crucial, so instead of concerning yourself with long patch assessment, integration, testing and roll out phases, where critical security patches can take months to roll out, organisations should be aiming to get these patches into production in a matter of hours. Within a few days of a vulnerability going public, exploits are already being tested by cybercriminals, so waiting until the next monthly patching cycle leaves the business open to attack. These attacks will come in the form of phishing, and circling back to the beginning of this article, phishing attacks have skyrocketed as the COVID-19 crisis worsens across the world.
How to measure cyber security posture
Having the answer to “what is my organisation’s cyber posture?” is more important than ever for financial services organisations. A mixture of technology, auditing expertise and consulting usually help organisations navigate their way through. However, a solution that could gather and present security metrics automatically, for review and formulation of action, would be hugely advantageous.
Identify gaps in security control effectiveness
Huntsman Security’s Essential 8 Auditor is a tool that enables organisations to quickly assess their security controls’ effectiveness.

Essential 8 Auditor – executes a cyber risk audit
The tool does not need to be engineered in, it can be managed by your IT department or risk audit team. Developed to measure an organisation’s compliance to the Australian Government’s Essential Eight framework, the tool supports APRA CPS 234 requirements to:
- Have information security controls in place to protect the criticality and sensitivity of your assets, including those managed by third party suppliers;
- Test the effectiveness of your security controls, and;
- Conduct internal audit activities that include reviews of the design and operating effectiveness of information security controls.
To find out more about the Essential 8 Auditor, please visit our website page:
https://www.huntsmansecurity.com/solutions/cyber-security-solutions/identify-gaps-in-your-cyber-defences/
 About Huntsman
About Huntsman




