One thing that Huntsman (and all B2B companies) consider when creating marketing material is what terms people use to search for solutions within the orbit of the capabilities we provide (in our case cyber security). For those that aren’t aware, the terms used can have different popularities, determined by search volumes, some of which will have a cost to buy if their ranking is near the top. These prices vary enormously and can stretch your marketing budget or pose a barrier if you are competing with someone with deeper pockets who is prepared to pay more to finish higher up the search engine page.
There are all sorts of tools available, including Google’s own Adwords/keyword planners, to help decide what search terms are going to be most useful. These normally take a search string and tell you the value and costs, as well as the various alternatives that are close in content or structure that people are searching for.
Cyber security
As we, Huntsman Security, are a software solution vendor in a certain sector – the term ‘cyber security’ is an obvious place to start. Cyber security is an industry in its own right and security analytics and risk measurement sub-topics within it.
Using such a tool (Wordtracker) we can see that the top ten terms related to cyber security are as follows:
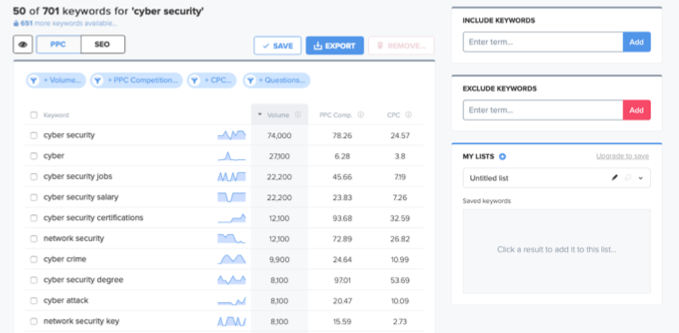
Top cyber security search terms
‘Cyber Security’ itself has the highest volume (average searches per month) and a high advertising cost (CPC or cost-per-click) as one would expect, with ‘cyber’ in second place (but considerably lower in volume and cost terms). Interestingly in that top ten, 4 of the related search words are job or career related: ‘cyber security jobs’, ‘cyber security salary’, ‘cyber security certifications’ and ‘cyber security degree’.
This might not be surprising given the scarcity of resources in this industry and the opportunities it presents for people that want to work in it. However, people looking to get jobs in a field don’t make good customers for software vendors (more so for recruiters and training/qualification providers). The cost per click for some of these (cyber security degree at $53) indicates that capturing potential course applicants (or graduates) is a big target.
If one takes out the generic and training related terms the top ten search words by volume reduces to four:
- Network security
- Cyber crime
- Cyber attack
- Network security key
If we’re comparing these four terms, ‘Network security’ has a fairly high cost per click (it’s a general term so to be expected) at $26.82 and ‘Network security key’ has a low cost per click (a tenth the amount at $2.73) but is quite a bit more specific (and obscure).
So, can we conclude that the best things for software vendors to talk about is how their solutions can be used to prevent ‘cyber attacks’ and as a way to combat ‘cyber crime’ ?
Page 2
Search engine optimisation is all about hitting the top ten / page 1 of the google search results. This can mean looking for phrases that get searched for but with lower competition. As such, lower search volume terms might be a good way to attract more specific search queries.
If we look at the next page of responses from the above query the range of search volumes is from 6,600 a month (for ‘information security analyst’ – there’s those job searches again) down to only 1,600 for ‘computer security software’.
In between there are several general search terms again (‘information security’, ‘computer security’, ‘internet security’ and ‘IT security’ etc).
Also the same pattern of job/career related searches (‘cyber security training’, ‘cyber security internships’, ‘cyber security analyst’, ‘masters in cyber security’, ‘cyber security course’ and ‘cyber security career’ etc…).
The other variant that seems popular is ‘news’ as ever. There are 3 separate (but similar) variants of this in the search records:
- Cyber security news
- Cybersecurity news
- Security news
This implies that making the news or appearing in it has a degree of usefulness unless, one suspects, you have suffered a data breach or attack of some description – that’s the sort of cyber security news nobody wants. There are no shortage of news sites covering this space of course so the trick would be to be found within as many of these as possible if it’s the hot search engine term it appears to be.
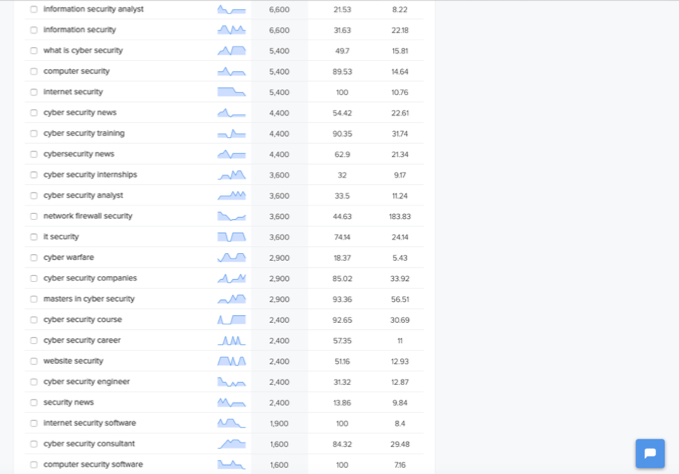
Cyber Security searches – page 2 results
Low volumes
Below this, the search volumes drop off further, which means that fewer and fewer people are looking for information and solutions pertaining to that topic. There is advertising money to be made for Google of course. ‘Cyber security schools’ only attracts 1,300 searches, but it is as expensive to buy as ‘cyber security degree’.
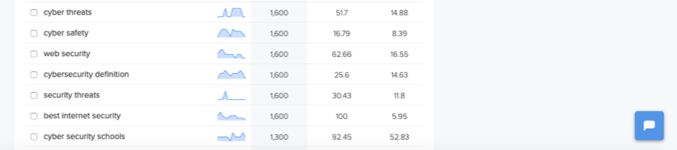
Lower rated cyber security search terms
What does this Internet activity mean?
It’s hard to second guess the desires of users typing text into search engines. Those searching for ‘cyber security analyst’ might be hiring managers trying to find them, as easily as people looking for companies advertising those roles.
This quick bit of research does seem to indicate that the skills shortage is real and reflected in what the industry (collectively) is hunting for – People and Skills.
Secondly it appears that ‘cyber crime’ and ‘cyber attack’ are concerns. It is unlikely that people wanting to carry out a cyber crime would search for that, so we’d have to conclude it’s businesses that are either worried about it or suspect they have been a victim already.
Search engine optimisation (SEO) definitely appears to be more art than science. For cyber security vendors like Huntsman Security who operate in the security analytics, SIEM, scorecard and integrated risk management space; we have to navigate it as best we can.
 About Huntsman
About Huntsman





