Our CEO, Peter Woollacott, recently attended the 2019 RSA Conference in San Francisco. As the primary cyber security trade show in America, RSA is an enormous cyber security showcase, comprising product wares from a multitude of cyber technology vendors. A key theme throughout the conference was that of cyber trust and organisational trustworthiness.
Cyber Trust in the Supply Chain

In our workplace, who can we trust? How can we possibly trust the democratic processes (e-voting), given the revelations of nation state rigging going on all over the world? Can organisations trust their supply chain, and how can anyone trust cloud services and technologies, given they have little to no control over the underlying systems or people who have access to your data?
Back in Australia, this got us thinking about Huntsman Security’s products and the underpinning reason for a SIEM’s existence, which is to assure security and trust within your organisation. Of course, trust isn’t just about trusting your staff, customers or suppliers, but also demonstrating trustworthiness in your own company to those same staff members, customers, suppliers and regulators.
Auditing – The Retrospective Trust Model

Auditing has traditionally been a retrospective trust model, since it allows organisations to look back at what happened over a period and determine whether things are on track. Just like financial auditing, when forensic accountants trawl through tax returns and sales ledgers checking everything matches what was reported, auditing in the digital world allows security professionals or regulators to retrospectively look at what’s been happening over a period of time.
The auditor might look at how certain security controls are implemented, such as your facility’s alarms and door entry systems, or they might check the changes applied to your technology systems, such as how well they are patched against the latest vulnerabilities. Auditing also helps organisations ensure processes are being followed accurately, for example, your access policy – if that isn’t followed strictly, the wrong people may have access to systems and information they are not permitted to see, which can easily lead to a security breach.
Auditing therefore helps security teams correct the course if things are veering off mission, and the auditing function will likely remain an important tool in the arsenal of business assurance managers for years to come. Yet in our highly connected world, where attackers move fast and steal information in real-time, retrospective auditing rarely works. After an organisation has been hacked and data is stolen, audit records help forensic investigators piece together what happened – so this is still needed to review what happened after the incident and determine how things could be improved to prevent this in the future.
Developing Proactive Cyber Security Auditing
A more proactive solution is required, one that works within the same decision cycles as the attackers, so that security teams can stops hackers in their tracks before they do any damage. This is where the SIEM comes in.
A well-designed SOC service will look to deliver both audit modes: retrospective and proactive. As a long term storage and search system, the SIEM can store months (or years) of data so that an auditor can follow the trail of a breach or incident and see which users accessed which systems and touched which aspects of company property. However, the nature of a SIEM permits the security team to also profile event log data as it comes into the system and raise alerts when certain patterns of behaviour or correlations occur.
Building an organisational trust model is vitally important for all businesses, since customers will only buy products or services from vendors they believe in. If trust is betrayed, then customers will likely walk away and seek alternative suppliers.
Operational Risk Monitoring
The power of this operational risk monitoring approach is its relevance to the organisation’s risk context. Huntsman Security’s Essential 8 Scorecard takes indicators from log sources across the business, such as logs from Active Directory servers, backup systems and vulnerability management systems, then aggregates it into a business intelligence dashboard and reports on compliance to each control.
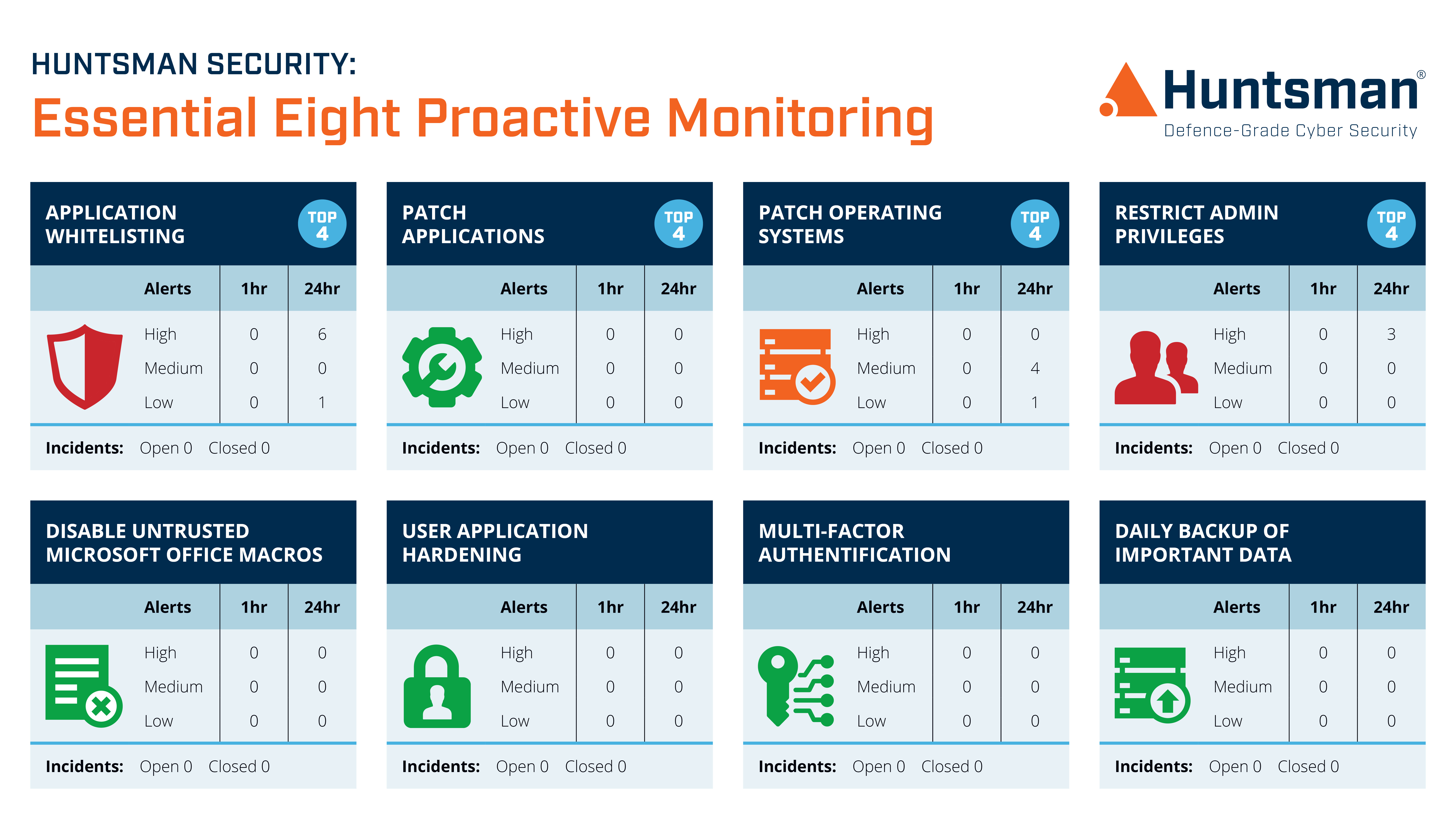
Essential 8 Scorecard dashboard
Furthermore, the design of the Essential 8 Scorecard matches the compliance framework the organisation must abide by so it’s a quick dashboard to shows where operational teams should focus. For example, if your need to demonstrate compliance with ACSC’s Essential Eight, the scorecard can show exactly how you are tracking with your patching programme, how your backups are performing and how your MS Office policies are configured. And all of this works in real-time, so you don’t need to wait until the next audit to find out you are not compliant.
5 Key Steps to Building SOC Resilience
When you build your SOC, think of it as the centre of your digital trust model, so that the activities your security team perform are aligned with protecting your organisation’s trustworthiness. This puts the value proposition for your team back into the real world, rather than being all about complex technology outcomes, which also helps the SOC team report meaningfully to your executives.
Since attacks originate from any number of sources (both external and internal) and the underlying motivation for a breach isn’t always theft, it’s as likely a breach is caused by a member of staff accidentally clicking on a phishing attachment or leaving a portable hard drive on the train. If your architecture accounts for all these use cases, where breaches of your most important data are reversed engineered into patterns of behaviour, you’ll have a better chance of detecting them as they happen.
By understanding the chain of events leading up to a breach, you can monitor each system or user in that chain and watch potential breaches develop in real-time. This is what a SIEM helps you do. However, you need to do some of the hard yards of tuning it to your business context, which is what many organisations struggle with. There are five stages of maturing your SIEM installation that ensure you are getting the best value from your investment while continually maturing your security team’s organisational oversight:
- Training the SIEM (along with any behavioural anomaly detection systems included in the service) so that you have a baseline of what normal looks like for your organisation. This can take between three and six months depending on the way your organisation works, but within the first four weeks you should begin to see patterns that can help you detect anomalies.
- Determine which business assets are most valuable to your organisation and focus the SOC’s attention on monitoring access to those assets. Collect as many security event logs as you can from these systems and check the event log configuration to see if you can improve the reporting coverage. Many event logging subsystems have a default configuration that sees them report just some of the event information they are capable of reporting. You should tune these to report everything then scale back when you know for sure you don’t need specific event types.
- Use pen testing methods to tune your attack profiling. When you know how an attacker might attempt to gain access to data, you can then develop SIEM rules that detect them as they move through your infrastructure. This is a particularly effective way of detecting the attack before it reaches your organisation’s crown jewels, and you can proactively implement measures to then protect the target.
- Monitor and report on unusual behaviour, where activity that isn’t necessarily an attack but is worth investigating is discovered by continually profiling network and system activity. A next-generation SIEM will incorporate Behavioural Anomaly Detection (BAD) technology, which once it’s learned what normal looks like, will alert you to anomalous activity.
- Perform real testing of the SOC’s ability to detect attacks. Rather than looking at it from an attacker’s perspective, test it. If a pen tester uses different techniques than you initially thought, or they pivot to another approach that you haven’t considered, then your SOC being aware of that approach allows them to look for indicators they could use for this technique.
Protect your Organisation’s Trust
Trust is one of the most important things an organisation develops with its customers and supply chain, but when lost it’s one of the hardest to restore. By focusing security efforts on protecting your organisation’s trustworthiness, you’ll make the work the SOC does more meaningful to a wider range of stakeholders.
 About Huntsman
About Huntsman




