The changes to the Australian Privacy Act (22 Feb 2018) requires businesses report eligible data breaches. Consequently, executives are asking how they can determine their preparedness and ensure they reduce the risk of potential fines. The Australian Signals Directorate’s (ASD) Essential Eight has received considerable airtime, and for good reason, as it provides a no-nonsense approach for organisations to improve their security posture by focusing on eight cyber security controls.
6 Steps to Reporting on the Essential Eight Model
The Essential Eight is an excellent benchmark for Australian organisations of all sizes to achieve, but IT security controls implementation varies in efficacy from one place to another. Let’s look at how the ACSC Essential Eight Maturity Model can be used to test the ability of each control to see if the implementation is truly effective.
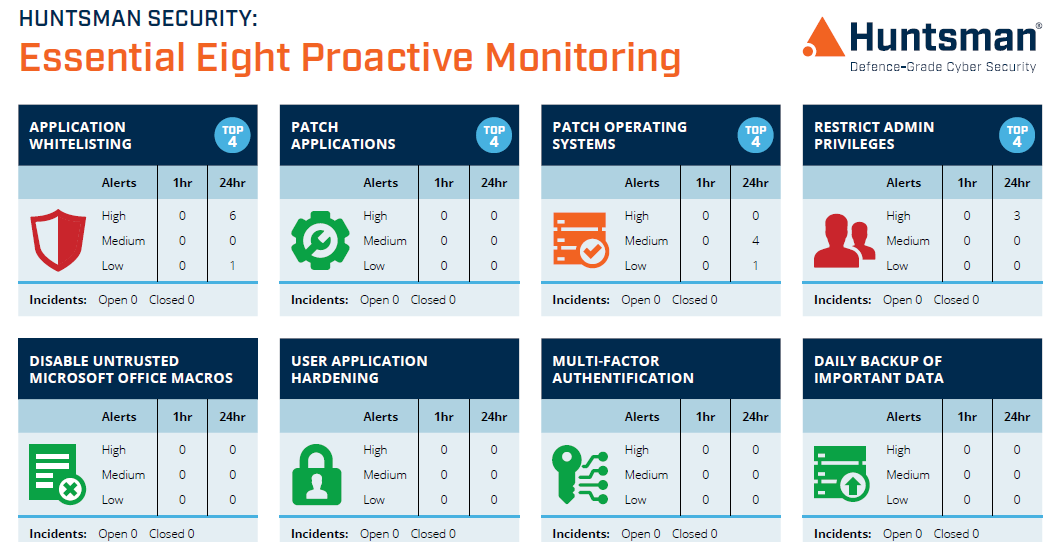
Essential Eight Scorecard – Monitoring Dashboard
Cyber Security Controls – Reporting
Cyber security reporting is a discipline that is often badly implemented and security managers need to improve. The reason for failure is that selection of the most appropriate metrics and capturing the raw, untainted data is hard. Many reports landing on executive desks contain nothing more than guesswork, leaving executives blind to the risks and, hence, unwilling to invest money to improve their cybersecurity posture.
As a security manager, it’s your responsibility to demonstrate investment value to the executive. But most security managers don’t know where to start, since demonstrating value for an intangible like security isn’t an easy outcome to achieve. To effectively communicate security posture and subsequent improvements, one option is to use a maturity model to show where you are today and how you will progress to the desired state in the future.
Cyber Security Controls – Meaningful Reporting
There are many styles of security reporting, oftentimes driven by an expectation set by the executive responsible for security (CIO, CISO or CFO). Each executive understands organisational health in a different way, so security managers elect to build reports as simple representations of the operational security posture, mostly from an infrastructure perspective. This means that metrics relating to number of patches, number of incidents, number of events collected in the SIEM, etc. are all they get, but in most cases these metrics provide no value at all to strategically minded executives. This is why reporting on the Essential Eight, showing a synoptic picture of where the organisation is today and where you need to get to tomorrow will resonate better with executives.
Cyber Security Controls – Essential Eight Maturity Reporting
The trouble with reporting on the Essential Eight is that for some of the controls, there may not be an easy way to represent it – i.e. there is no tool from which to extract operations data from. Take patching as an example; these controls are largely procedural and while tools can be used to deploy system updates, the message you need to report to stakeholders is that the maturity of the process has improved, not the number of additional patches pushed out this month. Patch compliance is important at an operational and tactical level, but executives need to know how the organisational process deals with all kinds of patches, from network device, operating systems and applications, and how you handle critical updates as exceptions out of the normal patching cycle, after undertaking a risk assessment that properly identifies the threat to your business.
Reporting against maturity is not a nascent approach, but it is difficult, which is why it still isn’t as commonplace as you might think. The strength of maturity reporting is that stakeholders can quickly understand the message you are trying to deliver without needing to understand the underpinning technology.
In its most basic form, reporting on maturity breaks each control out into a five-level scale, where the bottom ranking shows disarray and a misalignment with strategic security management outcomes, while a grading of five shows established processes that ensure security controls are consistently applied across the entire organisation. Level five also shows a commitment to continual monitoring and improving of processes.
The Essential Eight maturity model take the basic premise of a generic maturity model and build on it to include specific outcomes for each control against each of the five levels. Let’s explore this in a bit more details.
Cyber Security Controls – Benchmarking
Let’s use Application Whitelisting as our worked example, where the context is its ability to protect every workstation and server in the business. As we said before, the Essential Eight Maturity Model follows the recognisable and familiar approach taken by other maturity models. It has five levels, running from zero to four, which makes sense when you consider that the first rung of that ladder states that there is no process at all.
This model allows the security manager to quickly represent the organisation’s overall commitment to Application Whitelisting through colour coding and easy to understand language, shown in Figure 1. Without knowing the detail, executives can quickly see that anything graded green is good, while down at the other end of the scale, red is bad. The language used in the headings describes the alignment with the mitigation strategy itself, which will resonate well with executives, board members and other stakeholders. The rankings from zero to four are tailored specifically for the mitigation, making this approach prescriptive and easy to follow. Finally, where a mitigation applies to multiple areas of the environment, such as with Application Whitelisting, they are broken into sections, such as servers and workstations.

Figure 1 – Essential Eight Maturity Model – https://www.asd.gov.au/publications/protect/essential-eight-maturity-model.htm
Cyber Security Controls – Tips for Reporting on Maturity
Now it’s time to write the report and present it to stakeholders. Yet the question remains of where to start and how information should be conveyed. Should you just use a traffic light system or do you still need to provide details of all the patch states across every device?
The following five steps can be used to assist reporting on maturity:
- Define your mitigation strategy: Before baselining your environment, consider and document the reasons for the control’s applicability and specific mitigations you plan to implement. Introduce the Essential Eight as the model you are basing the report on and describe why it is valuable;
- Baseline your environment: For each control, provide a brief overview of its intent. Baseline your environment using the guidelines provided by ASD in the Essential Eight Maturity Model as you need a place to start;
- Define the target state: Define your target maturity rating and explain why. This is important since you are aiming to move from red to amber to green. However, if you show that you have not progressed by the scale, you may have had higher risk controls taking priority, which is also an important message to convey;
- Timelines: Set dates for meeting objectives. Try not to use specific dates since operational imperatives might cause to you miss the goal, so consider a month or a quarter within which you expect to achieve an improvement. Provide a commentary on any challenges you face and utilise the complexity ratings included in the Essential Eight, since they offer context and support your targets;
- Trending: This demonstrates your value to the organisation, as a security team. Trends help you articulate the journey the organisation is on and show executives how you have improved over time. If the executive sees red followed by amber, with today’s report showing green, they will have confidence that you are doing a good job.
Demonstrate the value of investment in Cyber Security
Cyber Security Controls maturity reporting is a well-known and well-documented approach to conveying value and security posture improvement to organisation leaders. The ASD’s Essential Eight Maturity Model leverages known attributes of maturity reporting. By following this five-step guide to maturity model reporting, wrapping it up with trending against each of your controls, you’ll demonstrate the value of investment in security over time and show your ability to keep the business safe from cyber-intruders.
 About Huntsman
About Huntsman




