Managed service providers (MSPs) have a massive revenue opportunity in security services they are not taking advantage of yet. Allied Market Research projects managed security services to be a $40 billion marketplace by 2022 and over 60% of that revenue will come from the small to medium sized business (SMB) market demographic.
Taking your First Steps into Security Services

Cybercrime isn’t going away and with the proliferation of operational technology and Internet of Things devices taking our lives online, threats from hacking and online extortion are only increasing.
Interestingly, the provision of security services is still seen as the purview of a few multinational service providers who specialise in the more esoteric aspects of security research. Capabilities such as reverse engineering malware and researching zero-day vulnerabilities stand these companies out from the rest, yet few customers (and none in the SMB market) require these services.
As a managed service provider, your role is to help the onsite IT team, who are typically IT generalists, do all those tasks needed to keep systems operating, while simultaneously planning system upgrades and rollouts, and provide incident management services when things go wrong. Those same IT generalists onsite will be very interested when you tell them you can also monitor their systems for cyber attacks and threats from malware, quarantine infected systems and assist in recovering from an infection or an attack. And many of these SMBs are in the market for this kind of assistance.
You are likely already doing some of the standard operational security services that MSSPs offer, such as system patching, hardening of desktops and services and access management for both internal systems and cloud systems. You are also likely providing incident response that covers virus outbreaks and cyber-attacks, even if it’s not an explicit service named in your contract. The SMB will still expect you to help if they get attacked.
Building a Security Operations Centre
Orienting your service provider company to provide managed security services isn’t as hard as you might think. In fact, most MSSPs have just one special technology toolset, known as a Security Information and Event Management (SIEM) system that sits at the heart of all your operational security services. The SIEM allows you to monitor all your customers’ systems from one location, which becomes your Security Operations Centre (SOC). The SOC team is responsible for running the SIEM, programming the logic it uses to detect attacks across your customers, while tuning it to remove false positives and coordinating incident response activities.

Figure 1 Simple process flow to setting up MSSP services
Figure 1 shows a simplistic view of the approach you need to take to get started as an MSSP. The core service is security monitoring, which requires you to consume security information and event logs from relevant data sources within the customer’s ICT environment. Let’s look at each of those steps (shown in Figure 1) in a bit more detail.
The importance of defined Security Service processes
Having well-defined and tested processes, like everything you do in managed services provision, underpins your success as an MSSP. Look at the core services you are providing and break them down into their constituent parts, then down into their most fundamental procedures, so that the way you provide your service is based on a repeatable “best practice” approach.
For example, incident management may be one of your high-level services. Within incident management, you will have several processes, such as incident identification, triage and incident notification, then you’ll consider your options for ongoing support. If you plan to have a team that deploys to site to help your customers, you need to look at how they do that. Is it on a 24×7 basis? Does your customer pay a retainer, or do they pay costs as they are incurred? All of this, as much as possible, should be defined up front, since the first time you ask these questions shouldn’t be the first time you are called out.
With your process model, you will likely stop defining it when you get to the lowest level of workflows definition – these are the working instructions or standard operating procedures used to run the tools, which show your security technicians and analysts how to do things using the tools they have at their disposal. Now you need to build your SOC toolset.
Building your SIEM and developing Workflows
SIEM technology can have a variety of deployment models, first you need to decide whether you want to run the technology onsite or in the cloud. A future article will look at these deployment models in more detail, but for now we’ll consider the simplest option, where we deploy it in the cloud and all the storage and operating system integration is all done for you by your SIEM provider.
Now comes the fun part. All the processes you defined in the previous step need to be translated into the technology implementation, so the analysts using the SIEM have repeatable steps they can walk through when undertaking their duties; these are often referred to as workflows by the security industry.
Continuing the story with incident response, within the SIEM you can define the procedures the analyst uses to identify threats, how they open a service ticket to track the job, how they report the incident to the customer and how they continue to track the incident as it progresses.
The most important thing to remember here is that you should be as thorough as possible when defining your workflows, since you need your analysts to undertake the same activities consistently, no matter how much pressure they are under.
Now you are ready to go live.
Launching your service
It’s now time to launch your service.

Integration of the service into the customer environment is relatively straightforward, all they need is to establish the connection between their network and your SIEM tool and ensure security events are flowing. Once that happens, your analysts will start to see things happening in the console. If you have a SIEM with lots of out-of-the-box rules and correlations preinstalled, they provide the perfect place to start from with regards to running the tool, since the job of your analysts, now the SIEM is running and ingesting events, is to program rules to detect attacks.
Tuning your Security Monitoring
As attacks are always evolving, it’s a continual job of getting threat intelligence from reputable sources and using that to construct new rules that work in your customers’ environments. Threat categories, such as insider attacks, require knowledge of how the customer environment works, so these are the kinds of threats your analysts will develop over time, using baseline activity models (what normal looks like) to determine when someone looks abnormal, which could be indicative of a breach.
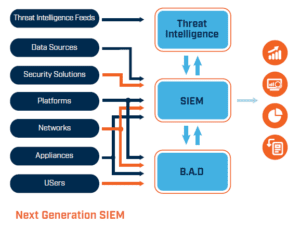
Should you be using a next-generation SIEM that has built-in Behavioural Anomaly Detection (BAD) it will start to baseline traffic and event patterns as soon as it is connected to the customer environment.
Building on your Security Service experience
Providing security services is a rich and rewarding addition to your managed services portfolio, services that are very much in demand.
Once you have established yourself as an MSSP and set up your SOC, you can further develop your pedigree and add on additional services such as consulting and training when you are ready. You don’t need to do everything all at once. As long as you can provide the fundamental threat detection and response services we’ve outlined above you’ll be in demand.
 About Huntsman
About Huntsman





