Cyber security compliance is a growing obligation for businesses across every industry. In some cases, this is a mandatory requirement. Whilst this is a challenge for all organisations, for many it’s overwhelming since they don’t have the expertise to decipher the standard and apply it to their own IT infrastructure.
This blog post takes a look a how to get started with security compliance.
Establish a security policy
First things first, you need to establish a security policy. In cybersecurity, governance is about ensuring the processes that drive the right security outcomes for the business are in place.
A security policy shouldn’t be a weighty tome of technical detail or a list of punishments the business will enact if staff break the rules. The security policy should be a nothing more than a simple statement of intent, covering people, processes, technology and information. It states the goals the organisation intends to be compliant with, aligned with the purpose and listing whatever imposed standards affect the business.
By publishing a security policy, employees have a reference they can use when deciding what to do about protecting the information for which they are responsible.
In the picture below, you can see how the security policy dictates the direction for the rest of the business. By linking to the standards and guidelines, along with the systems providing governance, it flows down to the people, processes, technology and information responsible for security through the business.
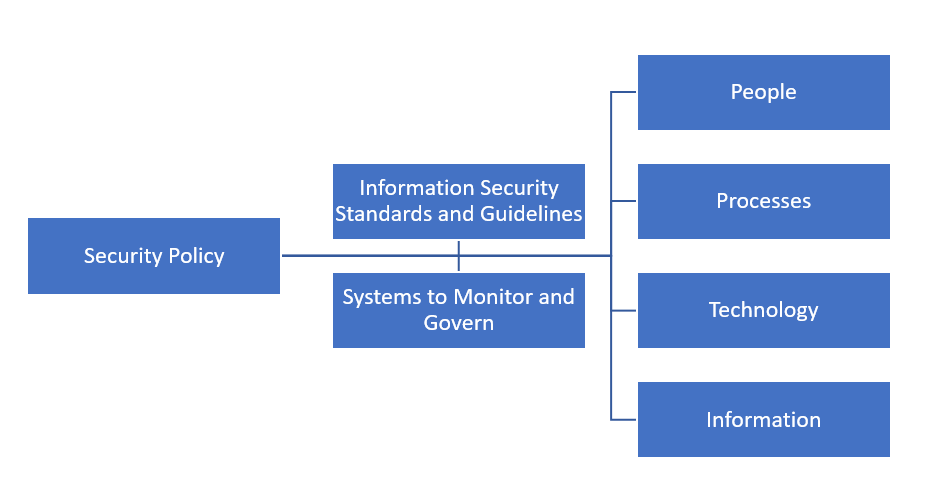
How a security policy can impact an organisation
Create a realistic security target
When you first see security standards and guidelines, especially mature ones like ISO 27001 and PCI-DSS, they seem complex, detailed and in many cases unachievable. Yet, most security standards have commonalities aligned with the model referenced above. However, achieving compliance can still be hard, so to help improve an organisation’s chances of success, the Australian Cyber Security Centre (ACSC) developed a set of technical controls to boost defenses without being overly complex or burdensome on businesses who are setting out on a security journey.
ACSC’s guidelines, known as the Essential Eight, comprises just eight technical security controls that it is said help protect business systems against 85% of targeted cyber attacks. Each strategy can be customised based on how the business operates and what the risk profile looks like, and the maturity of their implementation can be assessed against ACSC’s accompanying framework, the Essential Eight Maturity Model.
By taking the Essential Eight as an initial security target, the business sets an achievable goal irrespective of whether it will be assessed against ISO 27001 or PCI-DSS, since the threats the business faces now have significant blockers to prevent them from being successful. A full implementation of ISO 27001 could take 18 months to complete, even for medium complexity organisations, whereas, an uplift to eight technical security controls to meet the requirements of the Essential Eight could be undertaken in a matter of weeks.
Benchmark your cyber resilience against a recognised framework
Understanding the current maturity of the Essential Eight controls is a good place to start, then the C-levels in the business can decide how the security program should proceed. The easiest way to gain an understanding of the current state is to conduct an audit against the requirements of each of the Essential Eight controls, which can be done manually or using a technical solution that measures it across the whole business. Manual audits are labour intensive, but entirely possible and feasible in the smallest of organisations, but to do a manual audit in a medium sized organisation or even a technically complex small business, will take a very long time and details may be missed, leaving an unmeasured amount of residual risk that could result in a hacker getting in through the cracks in defences.
By using an auditing tool that checks your organisation’s technical infrastructure and reports on compliance against the ACSC’s Essential Eight, you will gain a detailed understanding of how your business is faring. You can then decide, based on business risk, how you want to focus efforts on improving the score.
Huntsman Security’s tool, the Essential 8 Auditor (The Auditor), audits your environment to measure maturity. Even in businesses with thousands of endpoints, all of which are managed from Microsoft’s Active Directory, The Auditor reports on which systems are compliant and where improvements should be made.
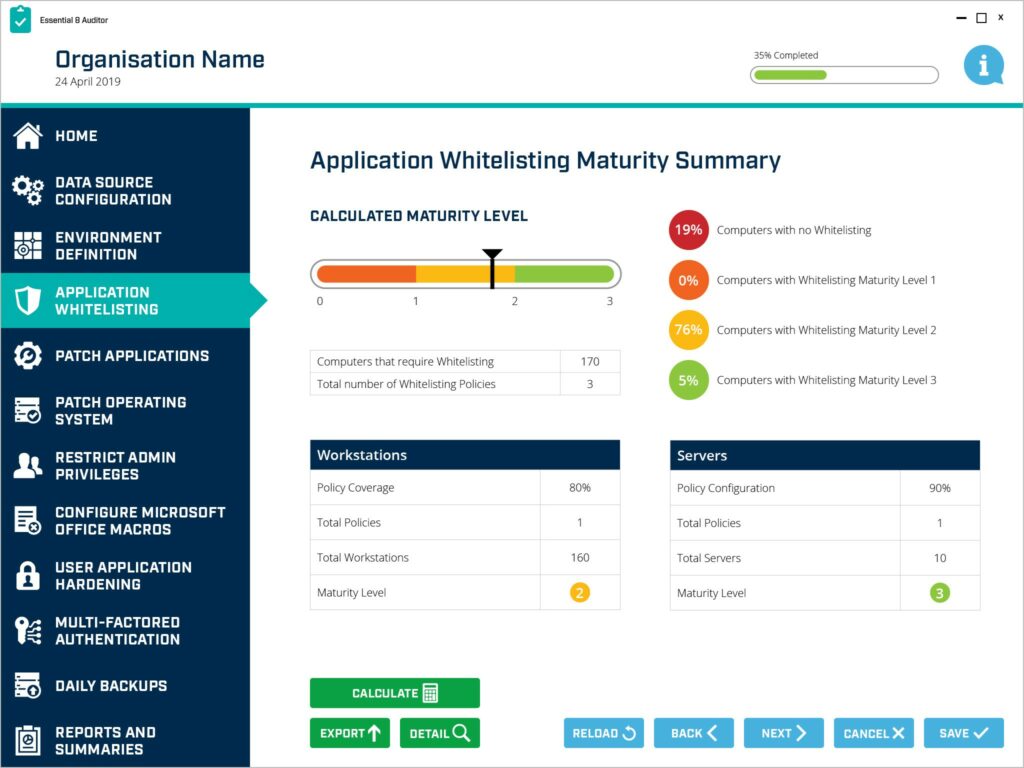
Essential 8 Auditor – Application Whitelisting Summary Report
The Essential 8 Auditor provides an instant view of maturity against each of ACSC’s strategies to mitigate targeted attacks.
Use cases for self-assessment
There are a couple of interesting use-cases where The Auditor helps. Firstly, the business could conduct a self-assessment against the Essential Eight and use that to direct internal IT teams as to how to improve their score and bring maturity up to the desired target state – in most cases the target should be maturity level 3.
The second approach is to use The Auditor to measure the efficacy of an IT outsourcer, where the audit checks how well they have implemented these controls. Executives or contract managers can then use this objective, impartial audit report to direct remediation activities and ensure the outsourcer is focusing on the right security outcomes.
In both cases, the desired outcome is the same – an improvement in the organisation’s security posture and a step towards compliance with a more strategic security standard or legislative framework.
Ongoing cyber maturity measurement
One final thought, once your business has achieved a position of acceptable maturity with each Essential Eight control, how will you maintain its cyber resilience?
It’s well known that IT systems frequently change as new patches and updates are downloaded from vendors, and new technology systems and upgrades make the previous audit report obsolete. To address this problem, you need to find a way to monitor your security posture in a more continuous fashion. You can read blog posts on this subject here and here.
 About Huntsman
About Huntsman




