The perfect cyber security storm that COVID-19 created has ushered in new cyber security operating models for many businesses. Many organisations are now switching focus from network security risk to endpoint security as a result of the move to working from home.
Australian organisations are under an increased strain from cyber adversaries as attackers have upped the ante to take advantage of the current chaos. In May, the Australian Cyber Security Centre (ACSC) published guidance to critical infrastructure providers as widespread targeted cyber-attacks continued against private sector and government entities alike, and this pressure continues today. For these reasons, we are seeing a remodelling of cyber defences through most businesses with a greater focus on security in cloud services and protecting the endpoint where users are most at risk. Despite the continually shifting threat environment, ACSC’s advice on how organisations can keep themselves safe remains steadfast and unchanged.
The importance of the Essential Eight
The Essential Eight, Strategies to Mitigate Cyber Security Incidents, is a prioritised list of security controls that organisations can use to protect their systems (and subsequently their information) against cyberattacks.
Security controls that relate to endpoint security
Five of the Essential Eight controls are directly related to endpoint security, and will assist organisations in protecting their remote users, even when the networking environment is largely untrusted. These five security controls are:
- Application Control: Application Control (Whitelisting) is a powerful feature of desktop operating systems whereby all non-approved applications (including malicious code) cannot execute. Every application has a unique fingerprint based on the underlying digital code that it comprises, thus any changes to known files mean the operating system doesn’t recognise its unique fingerprint, thus blocking infected files from executing.
- Patching Applications: Security vulnerabilities in applications are increasingly targeted by attackers since they are less likely to be patched than operating systems. ACSC prioritises application patching over operating system patching for this reason, but both are equally as important to prevent exploitable vulnerabilities being targeted by attackers.
- Patching Operating Systems: As with application patching, security vulnerabilities in operating systems can provide attackers with the means to affect serious compromises, and once one system has been overrun, it becomes easier for adversaries to laterally move through networks to their target.
- Microsoft Office Macro Security Settings: Microsoft Office applications have a unique code execution environment built in for automation and custom application development, however, it’s also possible to use this powerful platform to create malicious functions that are hidden inside seemingly safe Office files. Locking down Microsoft Office security makes it much harder for attackers to exploit these weaknesses.
- User Application Hardening: Application security is a big deal. To fully protect third party (non-operating system) applications, such as Flash and Java, and stop attackers using these to deliver malicious code, organisations should lock down their applications by using configuration parameters that limit the harm a compromise can cause.
By implementing these five security controls, organisations promote a robust security posture for their end users and make their computer systems more defensible given the changing nature of the current threat environment.
Security controls that protect enterprise resources
Further protection can be overlayed onto your security architecture using two additional Essential Eight controls to bolster user access to enterprise resources.
- Restrict Administrative Privileges: Administrative accounts are identified in the Essential Eight as the ‘keys to the kingdom’. Attackers seek to capture these accounts since they provide full access to a target’s systems, thus achieving their goals becomes much easier. No one should have a full set of administrative privileges, unless for a very specific task. Accounts for normal users should be limited to only the privileges they need, so having users with administrative rights giving them more control over endpoints should be avoided. Administrators should have role accounts, so that a person on the service desk that resets passwords doesn’t have the rights to take ownership of users’ file stores or accessing backup systems.
- Multi-Factor Authentication (MFA): Perfect security is impossible, but MFA, with an additional measure added to the username/password combination – such as fingerprints or tokens (RSA, DUO, etc.) – makes it much harder for attackers to compromise user accounts. Brute force hacking, for example, using traditional password cracking techniques are no longer viable.
If all else fails – backup your data
There is one additional control in the Essential Eight, a fail-safe strategy, that simply makes good sense – backup your data. Recovering from an attack is straightforward if you have a robust and reliable backup and recovery solution; so for resilient security, make sure that your backup system works, recovery functions as expected and the solution is protected so that an attacker cannot also compromise your backup environment.
Continual security assurance
While there are numerous security frameworks and best practice guides that organisations can align themselves to in order to meet these new levels of security threat, the Essential Eight is the perfect place to start. It’s recommended by ACSC as a very cost-effective way of mitigating against cyber risk. There is no magic bullet but a short implementation program will deliver a simple set of 8 key cyber security metrics to inform stakeholders of their cyber risks and enable them to be managed down to an acceptable level. There is the added benefit of freeing up your security team’s time, enabling them to start focusing on threat hunting and strategic outcomes rather than fighting operating fires.
Sustainable cyber resilience
Once the Essential Eight controls are working effectively and risks are being mitigated, how can your security team maintain this improved security posture? The framework comprises a maturity model to enable organisations to initially base line their security posture and then progress their security resilience performance through higher levels of maturity. Setting up security controls to improve your cyber defences is not a set and forget exercise. Using the Essential Eight framework, an organisation can quickly identify emerging risks to tweak their defences and systematically maintain an ongoing and effective security strategy; even as our ways of working change.
How to measure and manage your cyber security posture
In 2020, your organisation’s cyber resilience relies on robust network security and endpoint security – maintaining effective implementation of the Essential Eight security controls supports both. Huntsman Security offers two products that can assist with ongoing security against the Essential Eight maturity model: Essential 8 Scorecard and Essential 8 Auditor. Both provide a meaningful measure of the state of the ACSC Essential Eight controls and give the security team confidence that their efforts will continue to support their cyber resilience ambitions and address any change in the business operating model.
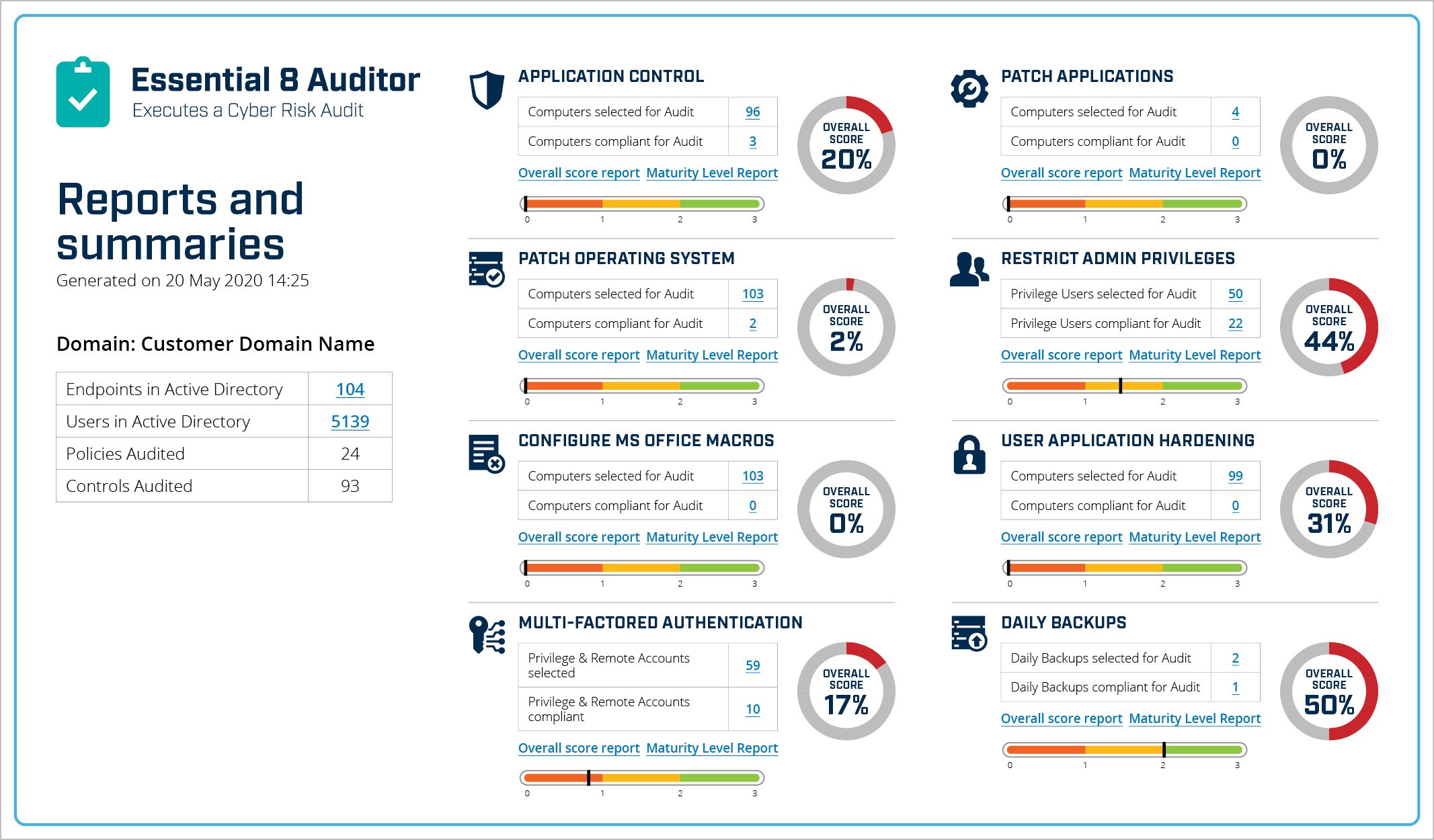
Essential 8 Auditor – Security Control Performance Dashboard
The Essential 8 Scorecard continuously measures the effectiveness of your implementation of the Essential Eight Framework. It provides ongoing, quantitative measurement and trend lines of all eight controls to immediately notify the remediation team when something goes wrong or drifts out of compliance. The Essential 8 Auditor is a cyber risk audit tool that delivers a point-in-time view of security control effectiveness against the Essential Eight Framework. The tool does not need to be engineered in and results can be exported for analysis by auditors, consultants and security or IT teams.
To discover how Huntsman Security’s Essential Eight monitoring solutions can help the management of your cyber security posture, get in touch with our team today.
 About Huntsman
About Huntsman



