Traditionally, security audits have been imposed on organisations by third party assessors, either for regulatory or compliance purposes and may result in significant findings that indicate security vulnerabilities, issues or deficiencies that require attention. For many, audits are activities on their annual compliance roadmap, often causing frenetic activity before the assessment start date, then bated breath while the assessor scrutinises systems and controls. For external compliance, and based on where this approach originated, annual financial auditing is suitable; however, applying this approach to cybersecurity leaves businesses exposed to unnecessary information risk.
Auditing security controls
Security controls, much like financial controls, are in place to maintain a suitable level of assurance over critical aspects of your business. However, unlike financial controls, the effectiveness of security controls can change quickly. For example, a new vulnerability discovered in the model of firewall you use in your network perimeter changes your overall security posture from a low-risk rating to a high or critical rating. It would be best to patch the firewall vulnerability as soon as possible since the time it remains unpatched is the time the business is exposed to attack.
This example shows how quickly a security situation can deteriorate – based on external factors entirely out of your control. The business would need to know the vulnerability exists, have the skills and capacity to assess it and remediate it, and within a timeframe that ensures adversaries don’t get there first.
Another example might be that your backup system has had a hardware failure, but your support team has not noticed it has stopped working. Backups is a critical security control, since restoring lost data and systems is one of the best ways to recover from a hack or malware infection. If your annual security audit comprehensively assesses your systems it will pick this up, but what if the hardware failure occurs just a few days after the inspection? Your business may be blind to the backup not working, yet it is wholly reliant on its efficacy for recovering after a ransomware attack.
Security control auditing needs to be dynamic, working in real-time and based on desired state management. If a control drops out of compliance, the security manager needs to know immediately so they can have it fixed before an incident occurs that requires the control to be effective.
Security targets
A variety of security-related compliance and regulatory frameworks exist that organisations can adopt based on their industry requirements. In financial services, the Australian Prudential Regulatory Authority Prudential Standard APRA CPS 234 came into effect 1 July 2019 to set expectations for APRA-regulated entities as to how they should be cyber resilient. The Australian Energy Sector Cyber Security Framework (AESCSF), based on the US Department of Energy’s ES-C2M2 cybersecurity capability model, helps energy sector organisations assess, evaluate and improve their cybersecurity capability and maturity. For Australian government departments, the Australian Signals Directorate’s ASD Essential 8 proposes eight technical security controls that, when appropriately implemented, can protect systems and information against 85% of targeted cyber attacks. All these frameworks have emerged as benchmarks or compliance targets for organisations in those industries. Each of them proposes a set of technical security controls and governance processes that must be in place to assure information and protect systems from compromise.
Assessing compliance might be undertaken by an external assessor once a year, and passing this audit is a great achievement for today. However, it must be bourne in mind that the primary purpose of investing in these controls is to protect the business all year round.
Each of these security targets has controls that can be monitored in real-time using technology, alerting when things change or degrade. From a cyber risk management perspective, finding ways to measure and monitor the state of security control configurations, their overall effectiveness and operational coverage across the business is paramount.
Making sense of the noise
The information collected from security controls may appear abundant. Still, a lot is spurious and should be taken in the context of other things going on in the network to determine if an attack is underway or whether it’s regular operation. To meet APRA’s requirement, for example, you need an effective way to detect and respond to cyber incidents, so you need real-time monitoring, alerting and a baseline of normal behaviour (to spot anomalies). To achieve this, you need to collect logs from every system and application on your network, monitor these logs over time, build models of behaviour, and report on anything that appears suspicious and breaches model thresholds.
Technology helps us achieve this goal in an otherwise impossible way. Next generation Security Information and Event Management (SIEM) platforms can capture logs and match them against rules (called correlation rules) that depict patterns of attack. Their behavioural analytics capabilities use machine learning and artificial intelligence algorithms to baseline normal activity and spot hard to detect attacks, such as those from malicious insiders.
Next generation SIEM platforms sit at the core of a SOC (Security Operations Centre). They are used the world over to detect and respond to cyber threats. However, they require a lot of additional rule development to meet the goals of next-generation security auditing. Senior security managers and C-level executives don’t want to see individual alerts from a SIEM, they want an easily digestible summary report on how well their organisation is tracking against its security targets. For this reason, dashboards and scorecards are a better approach for gaining visibility of current performance.
Security audit tools
Huntsman Security has created two unique products for measuring and reporting on security control effectiveness, based on the technical controls of the ASD Essential 8.
The Essential 8 Auditor provides point-in-time auditing of security controls. Outputs include identification of areas of non-compliance, performance metrics and cyber maturity scores. Results are exportable, for inclusion in audit reports or for sharing with security team colleagues and wider business stakeholders locally and remotely.
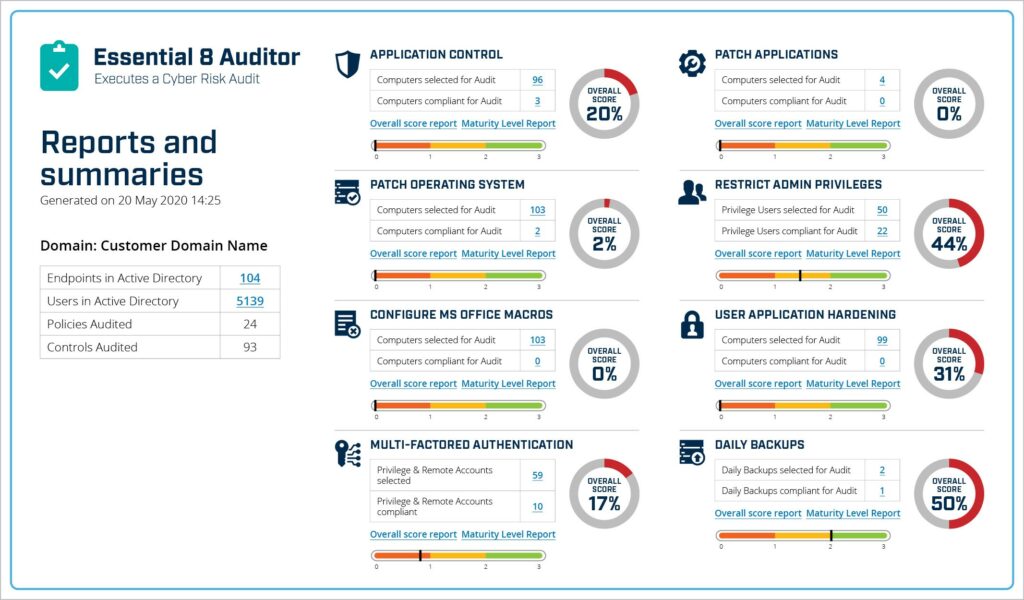
The Essential 8 Scorecard continuously monitors an environment to identify areas of non-compliance (using alerts) and delivers security control performance metrics and cyber maturity scores. The outputs enable fast, accurate decision making and provide on-going visibility of security posture to operational staff and executive stakeholders.
For more information on how Huntsman Security can help your organisation adopt a proactive, next-generation approach to security audits, get in touch with us today.
 About Huntsman
About Huntsman



