The updated Australian Government Information Security Manual (ISM) was released by the Australian Cyber Security Centre (ACSC) in December 2019. The manual represents the ACSC and ASD’s knowledge of best practice cyber security measures based on their experience in responding to cyber security incidents within Australia.
Originally designed for government agencies, the ISM also helps private sector organisations protect information and systems from cyber threats.

Figure 1 Australian Government Information Security Manual
The latest release supports a move towards a risk-based approach that gives you greater flexibility to manage your cyber security based on your own circumstances. The ISM also complements the Australian Government’s Protective Security Policy Framework (PSPF).
Download the latest, December 2019, ISM Compliance Guide
Key steps of the ASD ISM risk framework
The risk management framework used by the ISM draws from National Institute of Standards and Technology (NIST) Special Publication (SP) 800-37 Rev. 2. Broadly, the risk management framework used by the ISM has six steps:
Step 1 – Define the system
Determine the value of the system, and the information it processes, stores
and communicates, based on an assessment of the impact if it were to be
compromised.
Step 2 – Select security controls
Using a risk assessment, select security controls for the system and tailor
them to achieve an acceptable residual risk.
Step 3 – Implement security controls
Implement security controls and document how they are implemented within
the system and its operational environment.
Step 4 – Assess security controls
Assess security controls for the system and its environment to determine if
they have been implemented correctly and are operating as intended.
Step 5 – Authorise the system
Authorise the system to operate based on the acceptance of the security risks
associated with it operation.
Step 6 – Monitor the system
Monitor the system, and associated cyber threats, security risks and security
controls, on an ongoing basis.
How to comply with ASD ISM Guidelines
The Huntsman Security ASD ISM Compliance Guide has been created to summarise the security controls recommended within the ISM Guidelines and explains how Huntsman Security’s Next Gen SIEM and the Essential 8 Scorecard technologies supports them. You can download a copy of the guide here:

Figure 2 Huntsman Security ASD ISM Compliance Guide
Monitoring your environment against the Essential Eight
The Essential Eight security controls now recommended in the ISM are eight key controls that have been assessed by the ASD to defend against 85% of targeted attacks.
The Essential 8 Scorecard benchmarks your controls against the Essential Eight framework’s maturity levels and delivers clear, objective metrics of your cyber posture. Whether you have one or eight of the controls in place you can assess your risk exposure at any one point in time.
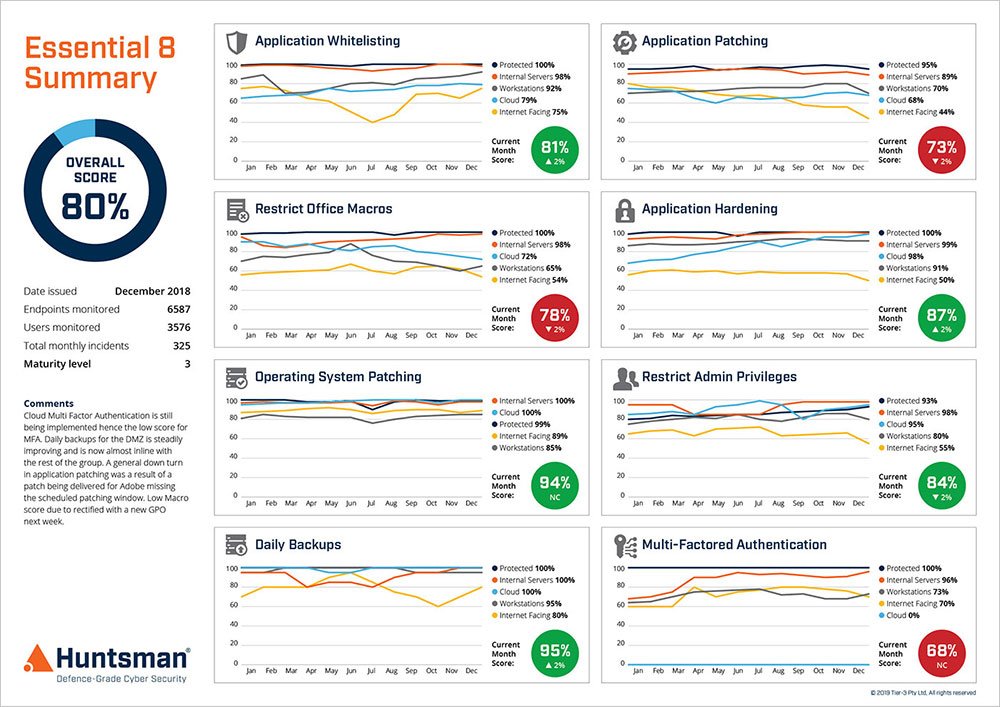
Figure 3 Essential 8 Scorecard – Performance Trend Report
Download Essential 8 Scorecard Product Brochure
Make 2020 the year to build your organisation’s cyber resilience
The first step to developing your cyber resilience is to understand your current position. Contact us to learn how to benchmark your organisation’s cyber posture against the key government recommendations and start your journey today.
 About Huntsman
About Huntsman





