The area of cyber security is one that is inundated with research and statistics – every year there are various “state of information security” surveys or “breach reports” including from organisations such as Verizon (The breaches), PwC (The cyber threats) and CIISec (The security industry survey).
These provide a wealth of information and intelligence that can be used to drive business cases, refocus activities with security teams or steer a wider organisation strategy in managing cyber risk. As with everything though, ultimate decision making happens at the top level of management and in the, so called, C-suite. It is here that budgets, risk appetites and cultures are shaped.
Quantifying risk at the C-Suite
What is often the case though is that the statistics used to talk security to the upper levels of management may not resonate with their view of the business – the strategy and the financial performance.
A recent article by Deloitte has highlighted the importance of getting the message across:
“The true cost of a cyberattack is often much greater than business executives expect.”
SEC guidance in 2018 required companies to be able to understand and report on material risks associated with cyber threats, however Deloitte found that only half have any quantitative risk measures, with the rest relying on the judgement of their experts or simple maturity assessments. It seems that Red/Amber/Green ratings and subjectivity abound rather than any objective, useful metrics and statistics at this level.
The need to improve defences
The advice from those tasked with protecting nations and organisations from cyber attacks remains unequivocal. In a recent speech the Director General of the Australian Signals Directorate (ASD) said this:
“Organisations must make data security a top priority, and develop a deeper understanding of cyber threats and defences.”
And she continued:
“Organisations must give cyber security similar close management attention as financial performance, audits and risk.”
The growing threat of cyber-attack was further reinforced with the release of a report by the Office of the Australian Information Commissioner detailing the number of notifiable data breaches at Australian organisations during the period from last July to December.
There was a 19% increase in the number of data breaches compared to the first six months of the year – broken down as follows:
- 64% malicious or criminal attack
- 32% human error
- 4% system faults.
Time is of the essence
In contractual terms, this clause means that the promised time of delivery or deadline matters. In cyber security too there are many statistics that support this being the way to think about cyber security risk. If you have a contract where “time is of the essence” and you fail to meet a delivery date, there is trouble ahead. Likewise, when you have a security intrusion.
It has been reported that, according to cyber security industry estimates, it takes around 19 minutes for a well-funded, advanced and skilled attacker to find further points of access in a network they have breached. This is a worrying statistic.
So, the C-suite really needs to take this timescale and ask the IT, security and compliance functions how their business would cope with the need to detect, understand and contain an attack this quickly. Time is of the essence in cyber security and the risk is very real.
(No) safety in numbers
Whether your risk ratings are hard facts or statistics and based on direct observations of your environment or highly subjective opinions, the need to deal with cyber security risks in a business-like way is clear. If real, systematic data that you can trust is not available, the first step has to be to correct this.
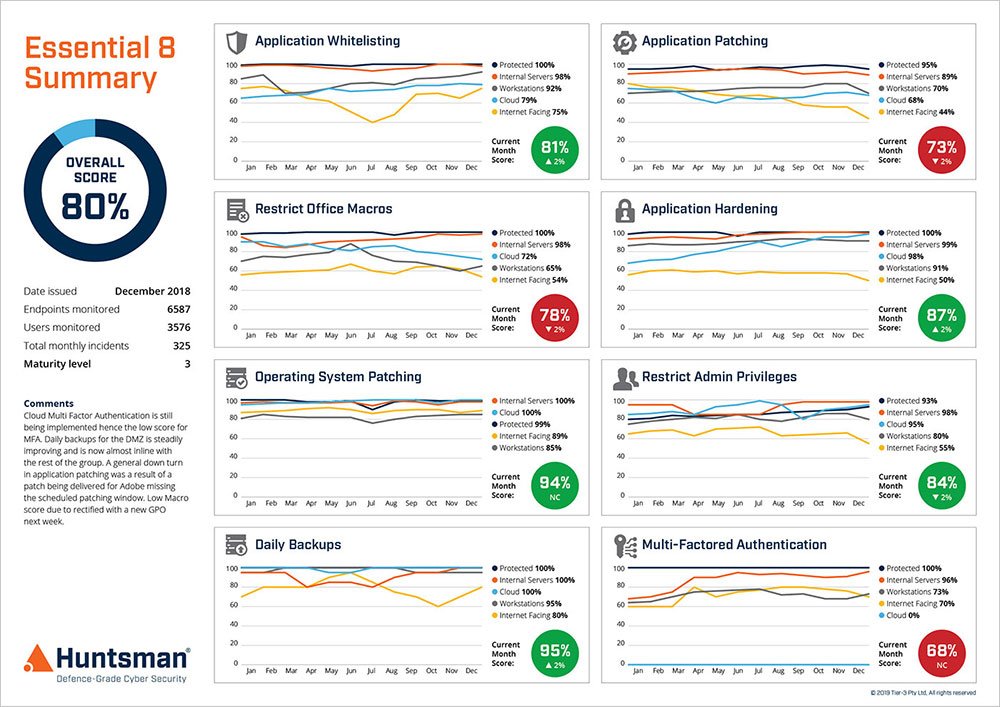
Essential 8 Scorecard – Performance Trend Report
Once you have a decent understanding of the scale, scope, severity and locations of the problems then you can prioritise effort and investment. Otherwise, you risk putting too many security controls (eggs) in the wrong basket and missing a weakness that leads to a catastrophic breach.
The SEC guidance around having clear understanding of the numerical risks faced is clearly valid when the wider context is taken into account. How many actual security issues do you have? Which ones affect the most critical systems? Which could be exploited to cause an impact or material loss?
 About Huntsman
About Huntsman



