Managed service providers not yet offering managed security should certainly consider the pros and cons of a security monitoring service prior to investing in the tools and people. However, the small to mid-sized market is crying out for cost-effective managed security, since getting it right with their own people can lead to unexpected costs and technology investments that are underutilised.
Provide the Security Services SMBs Need
Most businesses, aside from those in start-up mode and the very small (less than 10 staff), have questioned, at some point, whether they are secure. This can range from a fleeting thought when a data breach or hack is being covered by the media, through to investing in technology and people to help them achieve the elusive goal of being cyber secure.
At first, the business might be tempted to do it using their internal IT resources, who will likely take a stab at addressing these requirements from an operating system and network perspective. They might even come to realisation themselves that centralised log management is a good idea, so the team charged with taking them on the security journey have all those juicy security logs in one place.

Security logs are the goldmine of threat indicators
This is a sound approach and something we’d encourage, since security logs are the goldmine of threat indicators, sitting inside an historical record of everything that’s happened on their systems. Yet, oftentimes it’s here that someone says, there’s way too much data to sift through ourselves – we need help – thus triggering the Security Information and Event Management (SIEM) discussion.
At this stage, the business has reached a level of security maturity where they understand how little they can do with the tools they have and while they need some more investment, there is a definite trade-off between buying equipment and outsourcing.
As an MSP (and of course those already acting as Managed Security Service Providers) you are best placed to assist businesses when they get to this stage, since you already manage the technology, have the expertise in your support team to implement the software they need and the capacity to add one more monitoring solution to an arsenal of systems and network management tools already being used for similar purposes.
There are several factors you can consider as a value proposition that customers can latch onto:
- You have done the product evaluation work and have selected the best product for the service – there are so many options out there, and it’s become very difficult for organisations to decide on where to spend their money;
- You have the staff to provide the security operations centre (SOC) view of their environment, especially if you already run a 24×7 service;
- The customer has both cyber security (operational) security risks and compliance risks they are trying to mitigate – and your service can help address both;
- Threat verification (as opposed to acting on false positives) isn’t easy – too many false alarms offside security with management, as security gains a reputation of scaremongering and crying wolf;
- Security incident response is complicated and if a real threat is discovered, the business may not have the expertise to deal with it themselves.
Which Services Do You Provide First?

Start with the simplest service, since this is the best way to add value to your customers without having to invest too much in additional technology, expensive personnel or developing processes that are outside of the normal operational remit you are used to working in.
Security Monitoring
The easiest way to get started in security is to offer a basic security monitoring capability, where a managed SIEM takes feeds of logs from customer systems (computers, network devices and applications) and sifts through them looking for indicators of compromise. All SIEMs do this, as it’s the fundamental defining requirement of the category of technology, but to get the most value from a SIEM, it’s essential that you know your customer environment.
As an MSP you are in a great place to fulfil this service, as the big security services providers who specialise in this offering are often not the same team who provide the desktop, server and network support. Having this inside knowledge is the unique selling point over your competition, since context is everything.
A multi-tenant SIEM can be used for this purpose, as its architecture allows you to provide SIEM services to many customers at once, ensuring the customer separation within the platform keeps every customer secure and partitioned from every other one.
Threat Intelligence
The SIEM continually ingests data from security vendors and intelligence providers that help it identify attacks on your customers’ systems. This special data, known as threat intelligence, consists mainly of indicators of compromise (IoC) which the SIEM continually cross checks against to see if those indicators can be found on your customers’ systems.
Other categories of threat, such as those attributed to malicious insiders, are much harder for businesses to deal with, since they often want to trust their employees and by considering them a threat they feel they are doing them a disservice.
Next generation SIEM technology can help here, since it has Behavioural Anomaly Detection (BAD) built in.
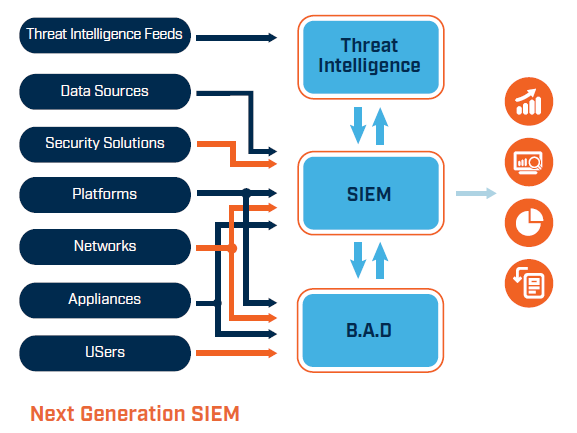
The SIEM profiles what the users are doing over time and then looks for interesting changes in the normal patterns of behaviour. The customer can still maintain a position of trusting their staff but can act on a threat notification from you that something looks unusual. These alerts might relate to heightened web traffic, an excess of emails, systematic assessing of corporate systems that they don’t usually access, etc.
No one is saying any one of these alerts is a threat, rather it’s something someone should investigate to see what’s changed. If it turns out to be normal and just an irregular thing that person does, then the anomaly detection service will be updated with that less-frequent, but still expected, behaviour.
Incident Response
Finally, helping customers with those all-important incident response activities should the inevitable happen, will bolster the service offering you now provide to those customers. However, this is where it starts to get harder for you as the MSSP as well.

You need the people on your team who have the skills to take charge of a large-scale cyber incident that could have far reaching and damaging impact on the business. It may require liaison with external parties, such as law enforcement and the government (for example, in the event of a privacy breach), and you need to ensure you understand your own legal requirements and contracts.
However, all that said, incident response, as a retainer service in a security services contract, can be very valuable to your customers, who typically don’t have the money to invest in having that kind of talent on the bench just in case something goes wrong.
Security is an excellent extension of any MSP’s service portfolio, so stepping into cyber in as low-risk a manner as you can will reap many rewards. You’ll extend your own company’s reach, compete for new work in new markets and now that you are an MSSP, you’ll be developing your own pool of cyber talent in a world where there is a deficit of these skilled professionals.
 About Huntsman
About Huntsman





