Forrester Research’s report: Top 13 Technology Trends S&R Pros Should Watch 2016 opened with a troubling statement:
“Selecting security solutions has never been more difficult.”
https://www.forrester.com/report/Top+13+Technology+Trends+SR+Pros+Should+Watch+2016/-/E-RES123921
Why is this the case? Are security vendors’ marketing messages too complex? Are threats being overstated? Or is it that the cyber security problem is just too hard to solve? Understanding your organisation and its security requirements is fundamental to success. Let’s take a look at the issue and suggest a better way of analysing the problem, hopefully making life easier for cyber risk owners.
One of the biggest cyber security problems businesses face today is understanding which vendor solutions, products and services will best serve their needs. Marketing material relating risks and threats to the feature-set of specific products serves no-one’s best interests and leaves executives wondering where to invest. Interpreting the plethora of vendor products and features into anything that resembles a comprehensive defensive security strategy is practically impossible and, while executives know they require something to keep their businesses safe, they become overwhelmed and often close ranks. Furthermore, it seems that no year goes by without a new buzz-term slipping into the vendor lexicon – such as machine learning or security analytics.
The Forrester report suggested that, “With 147 vendors claiming security analytics capabilities as part of their solutions at RSA,” it is little wonder it is so difficult for security and risk professionals to cut through the marketing collateral and get past the sales discussions to get to the truth.
The constraints of limited skilled resources
Advanced security analytics technologies use machine learning systems and algorithms to build a baseline of normal behaviour so they can then detect behavioural changes that could indicate an attack or misuse. Practically every security vendor in the threat hunting and anti-malware market is proclaiming security analytics at the heart of their technology, with special machine learning systems that detect malware, external attacks and rogue insiders.
However, the issue is that the majority of these technologies still rely on signatures or thresholds; augmenting detection capabilities with nothing more than simple recommendation algorithms, in much the same way that Amazon will recommend another crime thriller if you’ve recently read Tom Clancy’s Rainbow Six. These tools can provide focused potential indicators of compromise, but they still require an analyst to recognise, react and remediate. Although this is a step in the right direction, it depends on businesses having a large a pool of skilled security analyst resources.
Most Security Operations Centre (SOC) analysts are already inundated with alerts and false positives from threat detection technologies.
It is typically a team of security analysts reviewing ingested data and events to determine if threats are real or benign. There is rarely time for pro-active threat hunting. So, generating or collecting more events means hiring and training more analytical staff. Similarly, more false positives means even more wasted time and money. So how should Security Managers devising and operating their Information Security Management System (ISMS) and cyber security risk owners looking to reduce the likelihood of attack, approach these technology decisions?
Process-driven cyber security intelligence capabilities
The process designers go through for new systems, even in the modern age of DevOps and Agile Sprints, is to start with the basic requirements to which they then align various components or modules of the solution. But how should they derive the right security requirements from the business? This step is essential if you plan to build a Cyber Security Operations function that actually reduces the information security risk.

Start with an ISMS and a threat assessment: Ask yourself who you are worried about when it comes to the confidentiality, availability and integrity of your business, information and services. If you are protecting national secrets or have the secret plans for a new military aircraft, then you are likely a bigger target than a small travel agent in the local shopping mall. A small travel agent is still a target, but likely threat actors are different. The travel agent is most susceptible to financial fraud, so needs to consider threats from ransomware, social engineering scams and whaling attacks. At the other end of the scale, the defence contractor has those threats to consider, but is more concerned with attacks from nation states, who often have unlimited resources and skills, so the threat is real and significant.

Assess your current cyber security defences: This is not a matter of assessing your firewall and IPS solution. Look at people, processes and technology, and look for configuration changes that facilitate your business in preparing to defend itself. Visibility is a massive issue for most SOCs, so look to see where you can improve your logging capabilities and add intelligence and context, so that you have all the most relevant information available to aid the detection and diagnosis process.

Devise a robust security architecture: Security architecture is the discipline of matching security requirements against security controls in a structured way and covering people, process and technology controls. This allows your security team to maximise the effectiveness of the security controls through a comprehensive and strategic view of where each control sits in the overall security picture.

Buy the right technology: Once you know what controls, functions and outcomes you need, you can start matching the features of products and product families with your requirements, based on the architectural principles that meet the business objectives.
Executives need assurance that their investments are reducing their cyber risk exposure, which a holistic, architectural approach can provide. However, the task does not end there, if no one is operating the machinery, there is a risk that indicators of compromise never surface. This is where a properly defined SOC technology stack helps.
At the heart of any good SOC sits a requirement to identify, collect and process the vast quantity of log information pouring out of network devices, end user devices, servers and applications, with any one data item (or a combination of items) capable of indicating an attack is underway. This is how the majority of Security Information and Event Management (SIEM) solutions historically worked, collecting, normalising and correlating security events in an attempt to find that elusive needle in the haystack of needles.
Click here to investigate Huntsman Enterprise SIEM
Some solution approaches go a stage further. With a deeper understanding of the market and business drivers and customer needs it is possible to overcome the growing and significant issue of false positives by verifying threats and alerts in real-time, eliminating the queue of benign alerts for investigation, leaving only those that have been confirmed as being real cyber security threats to your enterprise.
Click here to see the Huntsman Analyst Portal solution
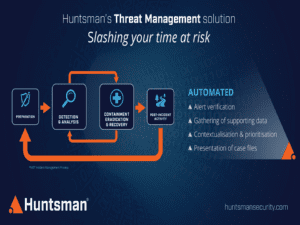
The outcome of good cyber security isn’t a larger number of alerts – it is a process and tool-set that delivers resolutions for verified issues as they arise as part of an overall ISMS. Automating threat verification profiles the behaviours on networks and provides a more complete picture of what is going on within the networks, systems and applications. Furthermore, looking at behavioural indicators means analysts gain an enhanced threat context, which can, for example, detect a sudden surge in traffic to an external IP address or a strange pattern of user behaviour. As soon as the normal bounds are exceeded, technology can then use threat intelligence and analytics to determine if that destination IP address is malicious or if the user is accessing sensitive material in a suspicious way as part of an insider attack.
Build your future cyber security capability today
If you start with requirements and build your architecture to meet those requirements, your security operations team will finally have a chance to deliver an effective security defence posture and deal with the threat overload problem.
 About Huntsman
About Huntsman







