In the UK, the National Cyber Security Centre (NCSC) runs an information assurance scheme called Cyber Essentials. It encourages organisations to adopt good practice in information security that will improve cyber resilience. It is an integral part of government and defence supply chain requirements that involve handling information – so anyone who wants to work with the public sector will find it is a requirement of those contracts. For other industries, Cyber Essentials provides tangible benefits if organisations choose to use it.
This is the first in a series of blog posts where we look at the Cyber Essentials information assurance scheme, explore how it works and discuss how it can operate as a baseline to develop cyber resilience.
Cyber Essentials overview
The Cyber Essentials framework provides an accessible, plain-speaking method to improve an organisation’s security posture without having to hire a workforce of experts. The framework consists of five baseline technical controls:
- Secure your Internet connection
- Secure your devices and software
- Control access to your data and services
- Protect from viruses and other malware
- Keep your devices and software up to date
Cyber Essentials operates with two levels of certification, both allowing organisations to use an assurance kitemark on their website or marketing material to show they have a reasonable level of cyber security within their enterprise.
The first level of certification, called ‘Cyber Essentials’, involves a simple three step process:
- Select a Certification Body via the Accreditation Body.
- Verify that your IT is suitably secure and meets the Cyber Essentials standards.
- Complete the Cyber Essentials self assessment questionnaire – the Certification Body will provide this and verify your answers. Once you have passed, you will be awarded your Cyber Essentials certificate.
The higher level of certification, called ‘Cyber Essentials Plus’, requires an independent certification body to verify that the controls are in place. There are various advantages to be gained by having external validation of security controls being in place, for example, possibly reducing cyber insurance premiums or providing a competitive advantage in winning new business.
The problem Cyber Essentials helps solve
An issue organisations face when looking to elevate cyber security to the boardroom is they get asked which standard or framework is appropriate for their use.
When there is no clearly defined option or regulatory choice, the array of standards, frameworks and control lists can leave even the savviest IT managers scratching their heads. Furthermore, once they decide which to use, such as the American standard from NIST (their Cybersecurity Framework) or the international standard, ISO 27001, there is a long road ahead before they can say confidently, they are protecting the business. Adding to this issue is that the choice of controls is up to the organisation since standards set goals but don’t say how to achieve them. The problem isn’t which framework to use, it’s how you operationalise it.
A mature organisation will drive continuous security improvement from the top, with a well-maintained security policy, the delegation of authority ensuring clear communication of responsibilities and accountabilities and a means of assessing control effectiveness. Yet this level of maturity is far from where most businesses are.
Beyond Cyber Essentials certification
Like all frameworks, standards and control sets, Cyber Essentials provides the security target organisations need to achieve; along with a key differentiator, it provides the practical aspects of how to do it. Once your security controls are established and independently verified, you can step back and take a breath, proud that you have achieved this milestone in your organisation’s security defences. Thereafter, Cyber Essentials requires an annual assessment.
If, like many organisations, you are concerned with cyber risk exposure in the intervening period throughout the year there are a few points worth noting which are outlined below.
Regularly check your security controls effectiveness
Between each annual assessment day there are 364 days where your security controls could drift off course and expose the organisation to a cyber attack or serious data breach; your operating environment is dynamic which means your cyber security posture can be strong one day and compromised the next.
Building on the implementation of the Cyber Essentials controls, your next step up the cyber resilience ladder is to regularly assess that the controls you have in place are still working – preferably continuously. If you track performance over time, you can quickly see and have the opportunity to remediate security exposures that arise.
Like any operational monitoring system, such as engine management systems in cars, or even the waring beep on a fridge, continuous security control assessment is better than finding out your security systems have failed after a breach occurs or when the assessor next conducts your certification audit.
The good thing is that operational cyber security technology, such as the elements proposed by Cyber Essentials, can provide alarms when things change, much in the way the car or fridge tells the owner when something needs attention.
Gain a consolidated view of security control status
The ideal scenario is to collect the operational event logs from each of the Cyber Essentials technology systems – firewalls, software and patch management systems, configuration control systems and anti-malware technology, and present them in a ‘single pane of glass’ dashboard. This means that technical teams can instantly see when any of the controls stray away from their compliance target.
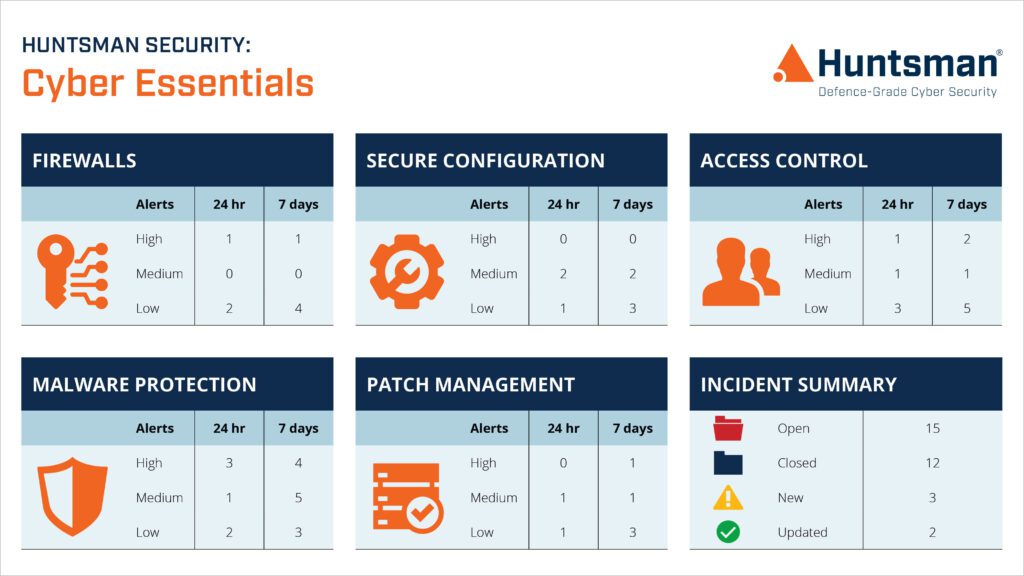
Huntsman Security’s Cyber Essentials solution dashboard
Communicate security control status to key stakeholders
The business relies on a number of teams to manage risk; this goes way beyond the security operations team. Following on with the engine management system analogy, the high level non-technical expert (the car driver) is the first to receive an alert. Likewise, in cyber risk management, senior business risk owners are at the wheel, responsible for steering the direction of the company. They need to understand current exposure. Finding a way to automatically update all stakeholders will go a long way to raising awareness and building cyber resilience.
Next Steps
In this post we’ve given an overview of the Cyber Essentials scheme, explained how it provides a practical first step towards cyber resilience and then shared some insights into some future considerations – beyond the annual certification process.
In future posts we will look at the five baseline technical controls and how each one plays a vital role in an organisation’s security posture.
 About Huntsman
About Huntsman



