Cyber maturity assessments provide vital insights into an organisation’s ability to protect its information assets and defend itself against cyber threats. However, they are time consuming, labour intensive and often difficult to execute – particularly when most staff are working from home and site visits are restricted. This blog post explores the elements of the process that present the biggest challenges and how security audit technology can help you overcome them.
Cyber Maturity Assessments
A full cyber maturity assessment involves a security audit, a comprehensive review of people, processes, technology and culture – a deep dive into how an organisation operates in its endeavours for cyber resilience. This includes interviews, questionnaires and a reliance on face-to-face time with staff on the ground. The security audit process itself involves a number of key stages:
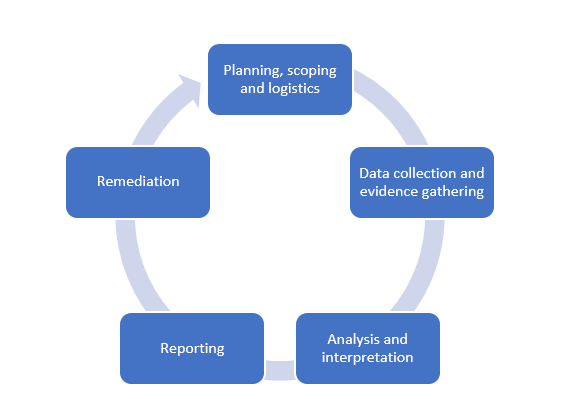
The Audit process
In ‘normal’ operating times this is standard operating procedure, but here and now in 2020, how do you manage the technical elements of an assessment, the data collection and evidence gathering and collation of information for analysis and interpretation and then report writing. This is hard if you have one environment, but if you have multiple business units or clients to service then it becomes a logistical nightmare.
Data collection and evidence gathering
Using internal security audit technology that can systematically gather data from across the organisation provides you with the ability to either manage the data collection and evidence gathering stage of the audit process without attending a site, or manage the process on site without relying on expert staff; the outputs can then be gathered for central (or remote) analysis.
This works perfectly for large diverse networks, for any situation where there are scarce expert resources, and for all situations where there are a large number of audit targets – be that suppliers or business units. Separating the data gathering from the interpretation is a logical division of labour and expertise, especially if people are in different locations.
Discover How Security Audit Tools Work

Analysis and interpretation
Internal security audit technology supports meaningful analysis and interpretation of data; collecting data in an automated way means that a whole environment can be used making the data comprehensive and representative. Where an auditor might inspect a subset/sample of systems and extrapolate the findings, a software tool can gather control metrics from the management systems and audit targets in their entirety.
Security audit technology also avoids subjectivity. In manual audits data subjects are often chosen (or excluded) to meet the needs or the assessor, for example, reporting on platforms that are known to be well maintained. An audit tool will look at all areas – good, bad or otherwise.
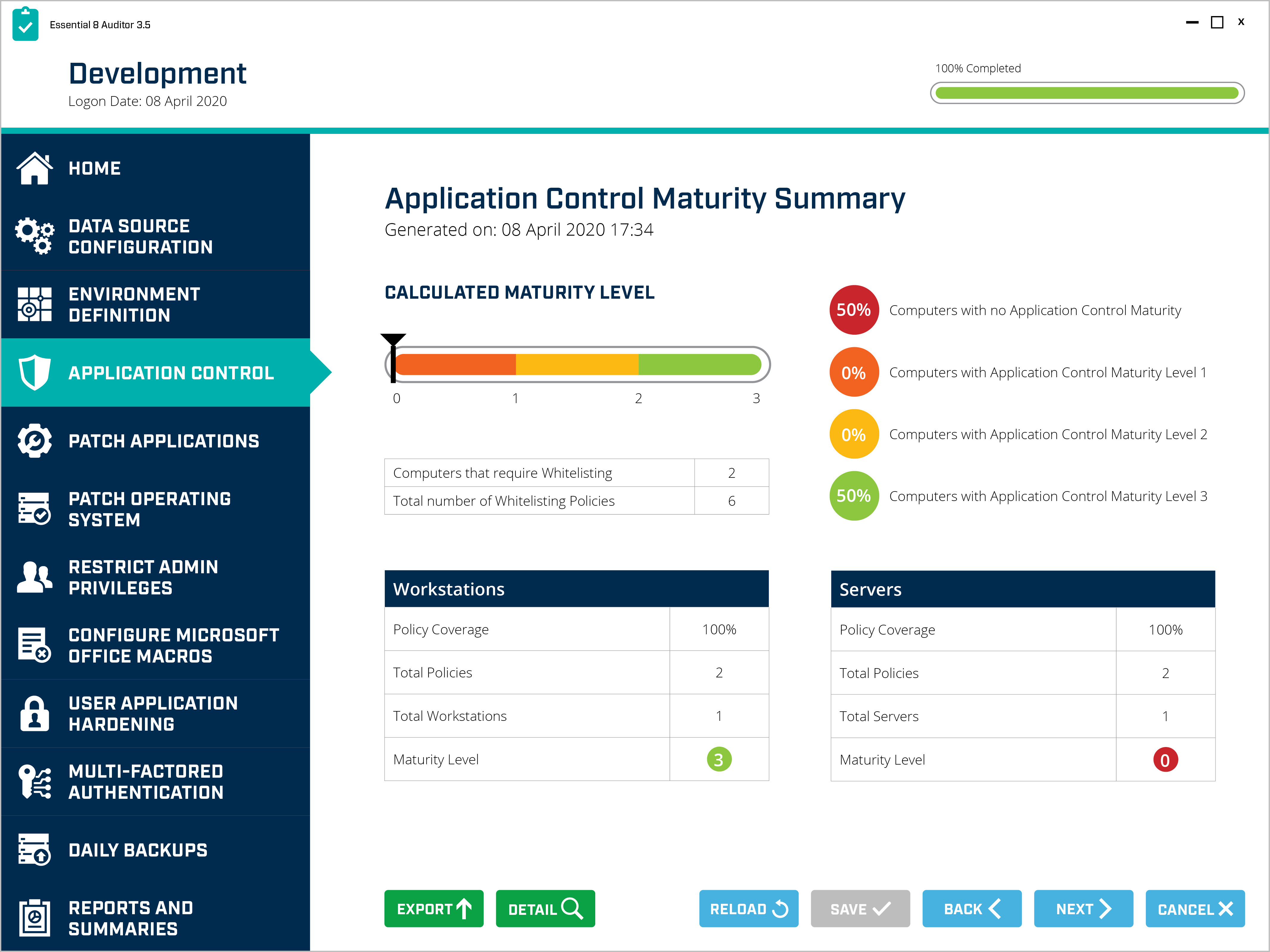
Essential 8 Auditor – Application Control Maturity Dashboard
The new normal in cyber maturity assessments
The challenges in conducting cyber maturity assessments persist, whether it’s conducting a review of your own business or your client’s portfolio of business units.
By streamlining the most cumbersome elements of the security audit process, you can free up your time to focus on remediation activity and development of a road map for improving cyber maturity. Security audit technology can help with your cyber maturity assessments today. However, they can also be part of your improvement plan that involves checking progress next year, next quarter or continuously.
 About Huntsman
About Huntsman





