Organisations are being asked by regulators, partners, and other stakeholders to improve their cyber security risk management process. As cyber risk becomes recognised as a business risk both senior executives and operations security managers are seeking greater visibility of those risks and access to tools that will help mitigate them.
Executives charged with ultimate responsibility for the cyber resilience of their businesses are vitally interested in the nature of those risks; and a regular summary of the latest cyber security posture. Cyber security scorecards and ratings can provide a summary measure of that security posture.
Operations and security managers need cyber risk management tools
For operations and security managers, summary anecdotal security ratings are only the starting point; it’s the verification of the nature and extent of these risks that is key to the security management process. Diagnostic investigation and empirical measurement are important in identifying and prioritising such risks. Evidencing changes in security outcomes as a result of adjustments to risk settings is fundamental to a successful and ongoing cyber risk management strategy.
Security scorecard solutions typically provide a clear and concise cyber risk summary and rating report for senior executives. However, there is another very important function of security scorecard metrics; that is to provide quantitative and detailed IT systems risk information for the purposes of operational risk diagnostics, investigation and remediation by the SOC team.
The importance of quantitative measurement
Information provided by a security scorecard should ideally be based on empirical measurement and systematic analysis of a framework of cyber security KPIs across the organisation.
Quantitative measurement of risk information is a must for cyber security diagnostics, risk management and ongoing security operations management. By measuring the operational state of multiple security vectors (or KPIs) within an organisation, for example, patching, administrator privileges and multi-factor authentication, the residual levels of risk can be measured and a highly accurate security rating calculated.
The days of arbitrary cyber security risk assessment have gone. Standardised assessment processes and reliable measurement methods are critical elements of an effective cyber security risk management regime.
Why you need continuous risk reporting
The timeliness of information and the currency of the risk rating is vital in managing risk; a cyber security environment is notoriously volatile so point-in-time risk ratings can quickly become obsolete. This is an important consideration as cyber security risks can emerge quickly and unexpectedly, and with potentially damaging results, so security risks need to be continuously measured and risk ratings updated accordingly.
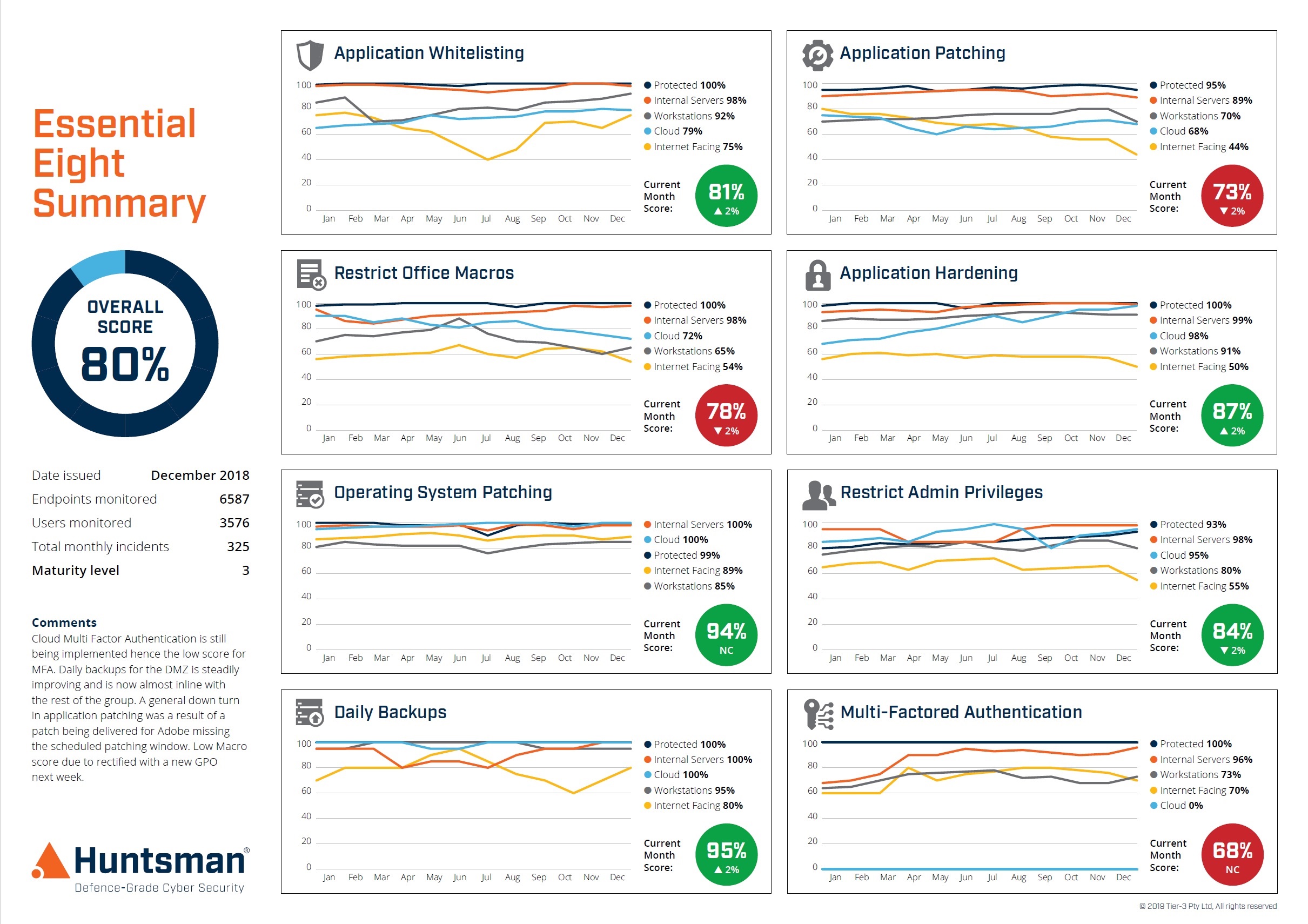
Essential 8 Scorecard – Trend Report
Seeing the outputs and effects of security controls on a continuous, automated basis is not only essential to ensure accuracy but is also the only way to generate reliable trend data that enable cyber security performance measurement and improvement over time. The more systematic, the more metrics, the more reliable.
Granular risk measurement
Qualitative risk measurement methodologies are sufficient for indicative security ratings. Whereas ongoing risk monitoring and measurement needs to be part of a risk management process. Subjective methodologies and the absence of a systematic and repeatable process limits its usefulness in determining small changes.
Being able to measure even small deviations in cyber security risk is important for making timely business-based risk responses. It is also how risks can be compared and prioritised so mitigation efforts can be ordered on the basis of the sound business criteria of cost benefit analysis.
It’s all about analytics
In modern business data scientists, analysts and senior executives, whether at the board or operational levels, demand evidence-based management information based on quantitative data.
Management algorithms and business decisions are increasingly determined by the analysis of relevant and verifiable data; security risk management included. Performance management and risk diagnostics, too, rely on empirical measurement to quickly determine risk differentials and make relevant security-based business decisions.
Cyber risk reporting – understanding the how and why?
What many auditing, scanning or survey solutions cannot answer is “How and Why”. Only quantitative measurement can provide that information. As we have discussed, diagnostics and investigation are key functions for many operations and risk managers; so being able to identify and mitigate particular risks relies very much on verifying the connection between an adverse digital intelligence observation and that risk. Without being able to establish and quantify a causal link between a sensitive artefact found on the dark web and an internal cyber security risk that lead to it being there, a security rating system is of limited utility.
This is the distinction between a reporting solution that compiles outputs and a diagnostic solution that understands them. One tells you the status while the other helps contextualise it in business terms.
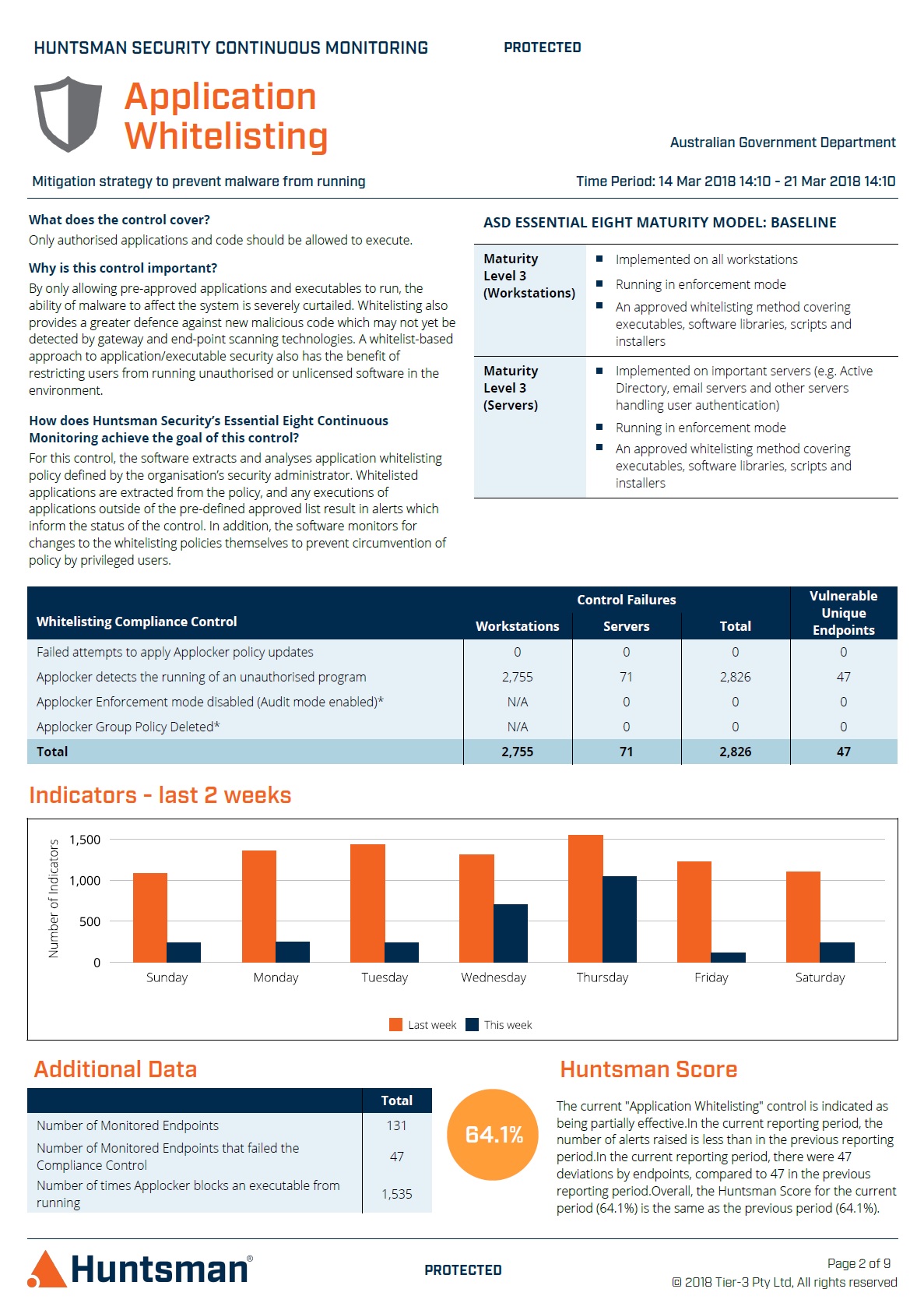
Essential 8 Scorecard – Application Whitelisting Report
The link between “how” and ”why” is therefore crucial as it drives the focus of corrective actions to manage risk and improve cyber posture in a way that is based on current, actual problems; rather than acting on the “what” of a high level traffic light display of status or a written report from the last audit.
Providing the “what” state of something for a report to management is only a part of the answer; being able to support this with “how and why” gives far greater insight and value for decision making;
- How and why is a risk present?
- How and why is the risk rating what it is?
- Why is the information that is in the public domain accessible?
- Why did a risk management initiative or control fail and how?
What does good look like?
Measuring and reporting on cyber risk in this way enables a better, and automated, translation of raw information to support the decision-making needs of the business:
- Measurement of resilience or posture in a clear and easy to understand format for senior executives;
- Continuous assessment to enable risk based performance management, trending and timely remediation at an operational level;
- The ability to match and systematically verify observed security outcomes with their cause and remediate those causal risks to meet operational and business security frameworks and objectives;
- Quantitative rather than qualitative measures to allow objective and accurate calculations;
- Comprehensive assessments of the state of security defences and controls to enable verification of security standards compliance;
- Measured level of baseline security defences against which a remediation program can be defined and tracked.
Meeting these objectives gives consistent measures of actual and residual cyber risk and objectively tracks the performance of controls to identify the quantitative state of that risk.
Support your SOC team with a continuous view of Security Control Effectiveness
The emergence of cyber security scorecards and security performance measurement has already significantly enhanced the availability of security risk information for security and business managers. Whether for senior executives or operational security managers, security scorecards now provide an assessment of the security posture. Quantitative risk information enables operations and security managers to take the next step of identifying the nature of cyber risks facing the organisation; measuring and ultimately prioritising those risks for investigation and remediation.
By using a security scorecard in your SOC you could see the current and prioritised vulnerabilities that lie within your security controls; imagine having a continuous view of your cyber security posture and having the ability to mitigate any new or changing vulnerabilities as they arise.
 About Huntsman
About Huntsman




