An increasing number of regulations and standards across many different industries are stipulating the cyber security controls that should be implemented by businesses and governments to protect their information. A recent collaboration between the Monetary Authority of Singapore (MAS) and the Bank of England (BofE) has seen them develop best practices for supervising cyber risk in banks and financial organisations. Standards are a great way to consistently explain the security target organisations should strive for, where they have a requirement to protect sensitive information like credit card numbers and personally identifying information. However, the issues relating to achieving cyber security compliance almost put the targets out of reach.
Let’s look at what’s holding back most businesses from achieving cyber security compliance and how straightforward technology solutions can bridge the skills gap that hinders many of these organisations.
The cyber security skills gap
Globally, there is a skills shortage in cyber security, causing many of the organisations who need to meet requirements like those stipulated by MAS and BofE to stumble at the first hurdle. They simply don’t have the skills and understanding of how to implement the controls or check they are remaining compliant. The cyber security skills shortage is often identified as one of the key reasons why cyber security incidents, globally, are on the rise. If organisations don’t have the skills to implement controls and assess whether they are complaint, then chinks in their cyber armour will always be discovered and exploited by the bad guys.
Today, there are literally millions of unfilled security roles across businesses of all shapes and sizes. This skills shortage is a mounting problem for big business, where most existing security teams are under an enormous amount of pressure to manage large volumes of data and meet the demands of senior management. However, the issues are significantly worse in small to medium businesses, where that cyber security ‘team’ could consist of only one or two members of staff, with little contingency for illness or the management of a major cyber incident.
How can modern businesses quickly build a security control baseline, understand the maturity of those security controls and rapidly assess their position each time they need to audit their systems without having that cyber security expert on the payroll?
The audit delusion in a dynamic world
Audits have been around in most industries for as long as history records. The main purpose of audits is to prove to external regulators that the organisation is properly operating within the guidelines set by the authority. Often these audits are self-serving, since their purpose is to protect the business or the industry from legal action by third-parties, such as governments or end customers. Cyber security audits have become a common way to assure an organisation’s security posture and are often conducted as a formal review each year by a third-party reviewer. In the static world of compliance against engineering or scientific standards, or processes relating to finance and accounting, annual reviews are still relevant. However, cyber security operates in a dynamic world, where the elements within the environment are constantly changing.
Applying the same approach to cyber security audits that accounting firms do to ensure finance compliance breeds a false sense of security that all is well for the next 12 months, until the next review reveals a deficit. The reality is, a deficiency could creep in 24-hours after the audit review has been completed, so the business is exposed to 364 days of risk, in the belief that all is well. Audits in the world of ICT and cyber security need to be conducted in real-time and they need to look at the detail of the systems being assessed and not just the high-level goals or aspirations.
Huntsman Security has developed technology to help organisations of all shapes and sizes adopt a proactive auditing and compliance approach. A key consideration was to make sure the skills gap is not what is holding up the adoption of cyber security good practice, since most of the security requirements organisations need to comply with relate to common ICT systems within the business, such as how you deploy patches, monitor your backups and use operating systems security controls, such as application whitelisting.
The Australian Cyber Security Centre (ACSC) has developed a list of eight crucial security controls that all organisations (anywhere in the world) should adopt. By implementing these controls and ensuring they remain intact, businesses could ward off 85% of targeted cyber-attacks. This guide is known as the Essential 8 and even for small businesses trying to comply with MAS or BofE requirements, the Essential 8 (and the ability to report on it) will significantly raise maturity and expose risks that otherwise would not be exposed.
Introducing real-time cyber security auditing
Huntsman Security reviewed the ACSC guidelines for the Essential 8 Framework and considered how the information relating to each control could be gathered from the business without the need for a cyber security expert doing the work. By taking a systematic approach to collecting control information across the organisation’s infrastructure, nothing would be missed, and the results would be objective.
The Essential 8 Auditor gives businesses an immediate view of their security control effectiveness. Shown in the diagram below, a relatively complex control, such as application whitelisting, can be quickly assessed across the entire organisation and the results marked against a known maturity model.
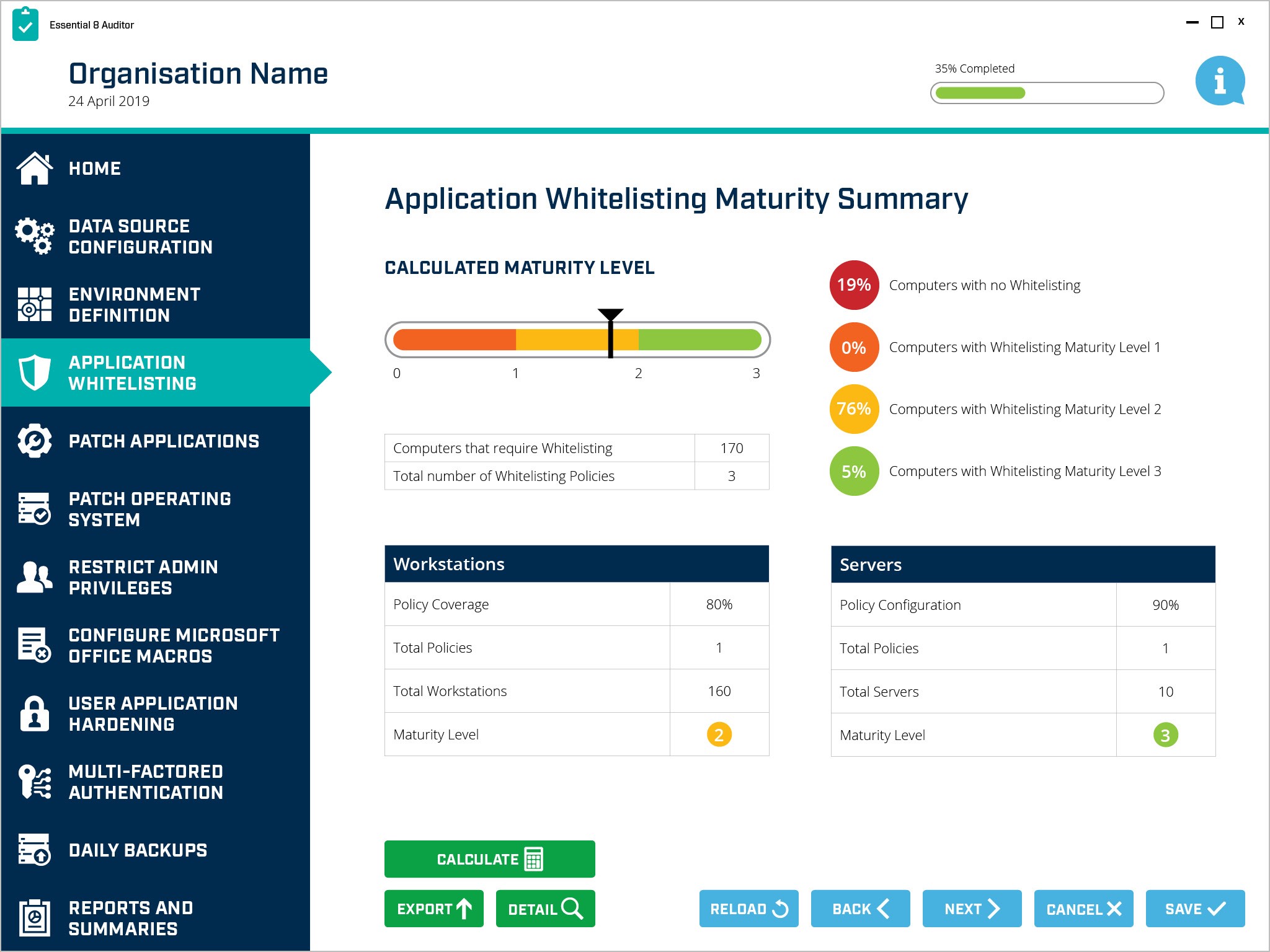
Essential 8 Auditor – Application Whitelisting Control Summary
The business now knows its exact position in regard to cyber security compliance and can decide what aspects of security remediation work need to be done to raise the security posture to an acceptable level. The reports produced by the Essential 8 Auditor also provide the best evidence to external auditors to validate the position the business is in, in terms of ongoing compliance.
Continuous assessment, planning, and remediation
Cyber security auditing should not be limited to an annual review. Using a technology tool, like the Essential 8 Auditor, organisations can review their compliance position within one day rather than taking a few weeks of digging through systems, processes and interviewing people (systems administrators, IT managers and end users).
The reality is, with the Essential 8 Auditor, you can review your position as often as you like. If it makes sense to review your compliance each month, then a few hours of maintenance work can be done to look at the gaps and see what might have changed. A small gap may have opened, for example where some systems are no longer being locked down with application whitelisting, so the Essential 8 Auditor immediately highlights them and helps you plan the remediation work to gain back your position of compliance.
Fundamentally, continuous auditing should be the foundational approach that all organisations adopt to achieve cyber security compliance, whether they are under the compliance oversight of MAS and BofE in Singapore and the UK, APRA in Australia, GDPR in Europe or the Securities and Exchange Commission (SEC) in the US.
 About Huntsman
About Huntsman



