The Australian Cyber Security Centre (ACSC) has created several publications aimed at helping critical infrastructure providers protect ICT systems from the escalating threat of nation state cyber-attack. The Australian Government has recently stated that organisations in both the public and private sectors are continually being targeted by adversarial nation states, and ACSC’s incident response activities over the past years show that water and power distribution networks, transport and communications grids are all at risk. The Australian Energy Market Operator (AEMO) has taken ACSC’s guidance and developed its own set of standards for uplifting the Australian energy sector, helping entities to become more cyber resilient. In this blog post we look at AEMO’s guidelines and how they relate to both IT and OT security.
AEMO Guidelines
As the peak body regulating the Australian energy sector, AEMO has collaborated with the ACSC, the Critical Infrastructure Centre (CIC), and the Cyber Security Industry Working Group (CSIWG), to develop a standard for cyber security that energy organisations can employ to improve their security posture. This framework, known as the Australian Energy Sector Cyber Security Framework (AESCSF), combines industry best practices from a range of trusted sources, such as the US Department of Energy’s Cybersecurity Capability Maturity Model (ES-C2M2) and the NIST Cyber Security Framework (CSF), and controls from ISO 27001, NIST SP 800-53 and COBIT. Furthermore, to ensure adherence to ACSC’s published advice, the AESCSF builds on the ACSC Essential Eight Strategies to Mitigate Cyber Security Incidents, and the Australian privacy principles.
Explore How Huntsman Security Technology supports the AESCSF
How the AESCSF works
First published back in 2018, the AESCSF applies to all energy suppliers. Unlike other cybersecurity frameworks, AESCSF combines control standards and advice with a capability maturity model tailored for the needs of the energy sector. AESCSF also allows organisations to assess their cyber security controls against the capabilities in its control list, with two main components helping organisations conduct a gap analysis: a criticality assessment along with a cyber security capability and maturity assessment. The criticality assessment rates an organisation’s criticality relative to its peers so that all sector members use the same methodology for reporting and benchmarking.
The AESCSF capability maturity rating allows organisations to quickly assess security control deficits against the Australian Cyber Security Centre’s (ACSC) core guidelines, while tailoring implementation details to the specific needs of electricity production: generation, transmission, distribution, and retail.
Specifically looking at how the AESCSF model works, the capability and maturity model contains two measures of preparedness: Security Profiles (SPs) and Maturity Indication Levels (MILs). The image below shows how these measures relate to each other.
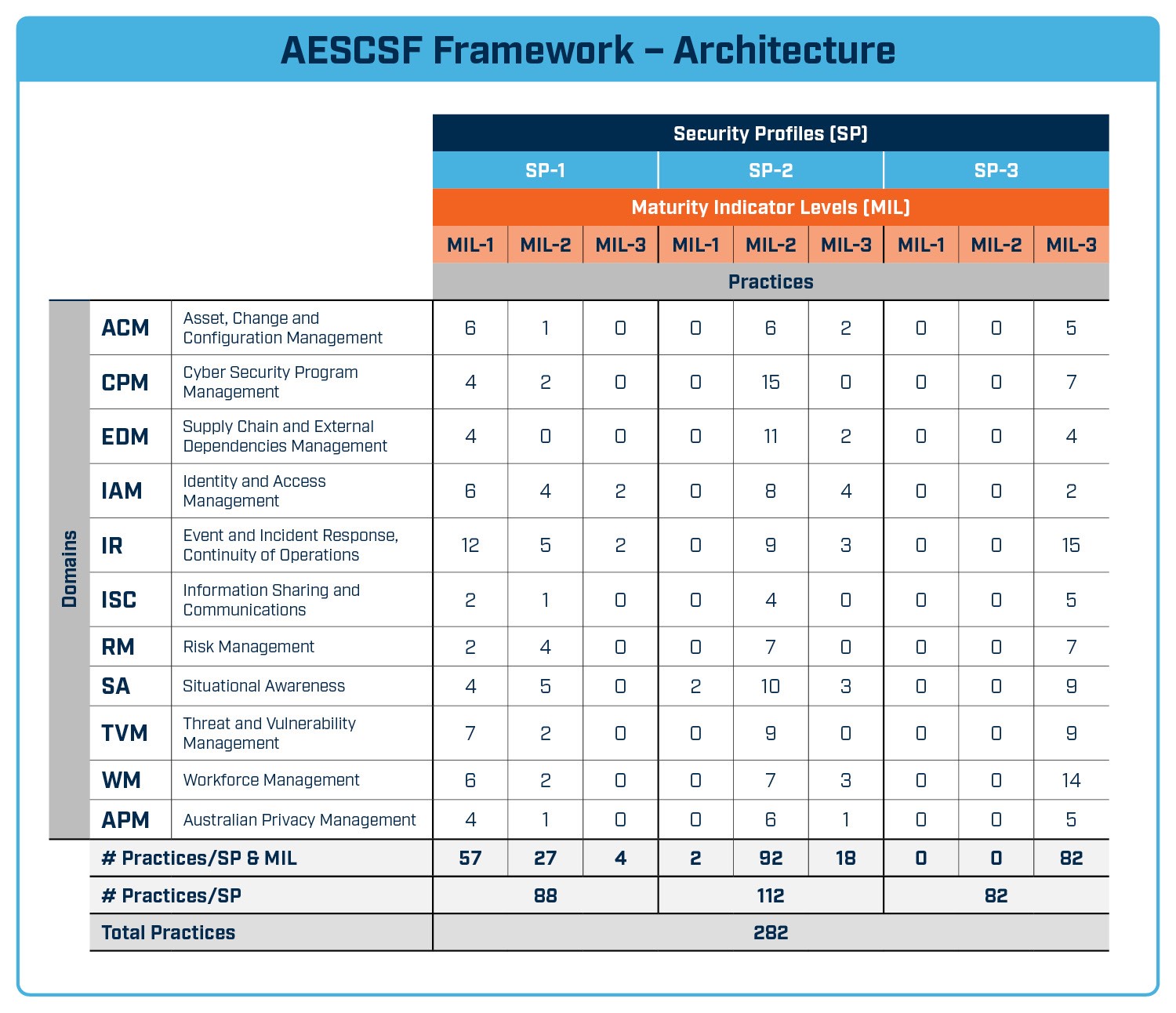
Australian Energy Sector Cyber Security Framework – Architecture
In total, the AESCSF maps 282 practices and controls across technical security and governance security domains to Maturity Indicator Levels (MILs) to assess compliance. The gap is easily determined from the results and can be used to validate the organisation’s security improvement plans or serve as the evidence backing up an investment plan.
Once an organisation meets the requirements of all necessary practices and controls, and achieves the appropriate maturity level rating, the next stage is to look at how you continuously monitor and feedback on compliance; this ensures the work done in the uplift doesn’t get undone. Organisations should seek to employ a protective monitoring solution to boost situational awareness, gaining reporting, process workflow, alert management and investigative tools for managing cyber security incidents.
Protective Monitoring for the AESCSF
Three key areas of the AESCSF require a solution for continuous monitoring and assessment. This helps organisations remain compliant once they have reached their target maturity level.
Cyber Risk Management
Continuous measurement and feedback on security controls, system configuration and operational effectiveness, along with mapping of performance metrics against the Essential Eight helps manage information and cyber risk across the whole of the OT network. Huntsman Security recommends using a live dashboard to provide visibility of compliance and where remedial action is required, as well as real-time alerting to support a rapid response to incidents and emergencies. Reporting on these issues should also be carried out quickly and on demand; business risk leaders and executives are obligated to know how their security environment is tracking against their regulatory targets. This also ensures there are no nasty surprises when an external security audit occurs.
Situational Awareness
Security logging in the information security world, is an important consideration and something that a well-prepared and competent security team should engage in with appropriate tools, such as a Security Incident and Event Management (SIEM) platform. The SIEM can detect indicators of attack and compromise and verify detections against known cyber threat databases, while coordinating management activities and helping provide input to compliance audits.
Incident Response and Business Continuity of Operations
Preparedness for cyber security incidents and emergencies is vital. Coordinating activities through your security operations centre, where detections can be verified and escalated, and the response teams can manage incidents effectively, allows the business to plan properly for business continuity situations.
Continuous monitoring and alerting solutions
Huntsman Security has solutions that provide continuous monitoring and alerting across several key areas of the AESCSF, including Asset, Change and Configuration Management (ACM), Cyber Security Program Management (CPM), Supply Chain and External Dependencies Management (EDM), Identity and Access Management (IAM), and Event and Incident Response, Continuity of Operations (IR). Compliance dashboards provide instant alerts to security operations managers when controls degrade or fail, thus obviating the need for (and the risks related to) annual assessments to discover issues.
 Download the Guide
Download the Guide
With the portfolio of Huntsman Security solutions, you can: assure your critical infrastructure against the most sophisticated attacks, and protect it as digital transformation sweeps through this sector.
For more information regarding the AESCSF Framework check out our website.
 About Huntsman
About Huntsman




