The MITRE ATT&CK framework is a resource that security operations centre (SOC) teams can use to refine their detection rules against known attack profiles. Using ATT&CK allows them to build specific targeted defences against advanced persistent threats (APTs) that are tuned to their organisation’s context, while covering a broad range of different tactics, techniques and procedures (TTPs) used by sophisticated adversaries.
MITRE ATTACK – a structured approach to cyber defence
Australia’s Prime Minister’s recent announcement about the massive cyber offensive targeting a broad range of government, critical infrastructure and private sector organisations across Australia came as no surprise to SOC teams; the activity has been escalating for many months.
Since January, when the world began to react to COVID-19, cyber activity has accelerated, with adversaries taking advantage of our distracted state and a mass migration to home working. The most recent cyber-attacks targeting government and critical infrastructure have purportedly originated from a hostile nation state, so SOC teams understand they are dealing with highly motivated and talented hackers. A structured approach to cyber defence is necessary.
Enter the MITRE ATT&CK Framework. ATT&CK is a comprehensive knowledge base containing an array of offensive tactics and techniques used by hacker groups tracked by The MITRE Corporation. The observations detailed within ATT&CK are based on real-world data, gathered over several years. ATT&CK is the perfect reference from which SOC teams can develop threat detection rules, since each entry is based on real-world adversary TTPs.
There is a total of 12 tactic categories, mapping loosely to the different stages of the kill chain[1]. The kill chain is used to model each of the steps a cyber adversary completes before they can achieve their goals. By detecting attacks in the earlier stages, means there is less likelihood that the adversary will achieve their objectives and the overall harm they cause can be reduced. As shown in Figure 1, the first three ATT&CK tactic categories relate to gaining initial access and establishing a foothold in the target’s network.
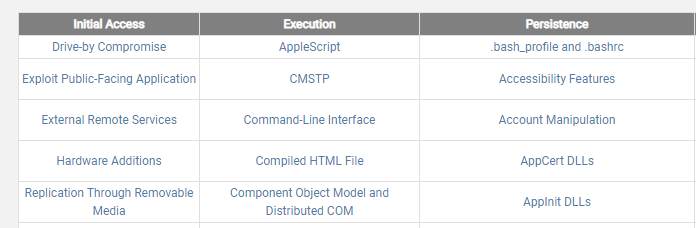
Figure 1 First three tactics of the MITRE ATT&CK matrix reflect the early stages of a cyber attack
Looking at the techniques listed under initial access, the topmost one is drive-by compromise. If the SOC team is concerned about their organisation’s susceptibility to drive-by compromise, they can drill into the ATT&CK knowledge base and see what details relate to this aspect of the attack. Here is what ATT&CK says about drive-by compromises:
A drive-by compromise is when an adversary gains access to a system through a user visiting a website over the normal course of browsing. With this technique, the user’s web browser is typically targeted for exploitation, but adversaries may also use compromised websites for non-exploitation behavior such as acquiring application access tokens.
There are various ways an attacker could initiate a drive-by compromise against your organisation, such as by compromising a website your organisation’s staff are known to use. It may be a supplier’s website, or a news site relating to your industry, or it may be a non-work-related site, but one that is very popular, such as for ordering takeaway food or online shopping.
The adversary will launch their initial attack against that unrelated website, installing malware and then subsequently infecting any of your organisation’s staff who use that site. Other methods used for drive-by compromises are paying for malicious ads to be published through legitimate ad providers such as Google, or your own web application interfaces are targeted for the insertion of malware that can be used to display web content or scripts that execute on the visiting client, such as forum posts and comments. The high-level process for drive-by compromises is shown in Figure 2.
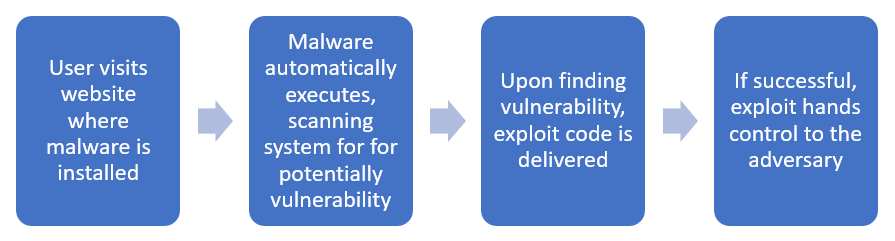
Figure 2 Drive-by compromise process flow
By using ATT&CK, the SOC now understands how this kind of compromise works and can start building rules and defences to protect against it. Within the entry for drive-by compromises (as with all the techniques listed in ATT&CK), MITRE provides a list of examples of successful procedures used by adversaries (and lists known adversaries who have used this attack in the past). For example, the APT known as Darkhotel has been known to embed iframes on hotel login portals, redirecting victims to download their exploits.
Each technique comes with a list of mitigations and detections SOC teams can employ to detect and defend against this kind of attack. Mitigations such as application sandboxing and restricting web-based content will both introduce reasonable defences against drive-by compromises, while SOC teams can monitor firewalls and proxies, inspecting URLs for potentially known-bad domains (taken from their threat intelligence feeds). The SOC can also use reputation-based analytics such as how old a domain is and who registered it to determine whether it’s risky or not and use that to inform the security manager or IT operations team about these risks.
Work from Threat Intelligence
At the time the Prime Minister announced the recent and ongoing cyber campaign, the Australian Cyber Security Centre (ACSC) published a detailed threat advisory listing many of the TTPs used during recent attacks. These so-called Copy-paste compromises take their name from the adversary’s use of tools copied from open source repositories. Since many of these exploits are widely used, SOC teams can turn to the intelligence in ATT&CK’s knowledge base to find details of how the tool might be detected and neutralised. Furthermore, the ACSC has aligned each observed technique within its advisory to the TTPs in ATT&CK, so SOC teams can align their defences against real-world immediate concerns and build rules and alerts to spot these attacks in their own environment.
Be ATT&CK ready
Cyber-attacks conducted by hostile nation states are a major issue for both the public and private sectors. Their objectives include stealing intellectual property, money and destroying economic stability and national security. SOC teams need to play their part in defending their organisations, whether it’s in a critical infrastructure provider or in a building company, since every business plays its part in maintaining its country’s economic health.
The MITRE ATTACK Framework has been designed to provide all the details of adversarial TTPs to reveal the motivations and intent behind active APTs. By understanding your own organisation’s context and who the threat actors are, you can quickly prioritise which TTPs are important and ensure your organisation does everything it can to prevent, detect and respond to cyber-attacks.
[1] https://lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
 About Huntsman
About Huntsman




