In light of recent world events, many governments are strongly advising organisations to monitor for cyber-threats and take steps to enhance their cyber security posture. In Australia, this advice has come in the form of the latest ACSC advisory dated March 4th 2022. It outlines the increasingly hostile malware attacks, ransomware environment and the state-sponsored targeted attacks on network devices.
Links are also provided to CISA and NSA publications for guidance on securing networks, other ACSC and Partner reports as well as a comprehensive Appendix that details common cyber attack and mitigation techniques in a handy threat taxonomy aligned to the MITRE ATT&CK® matrix.
The advice is intended for entities to take the appropriate action to protect their systems and networks. It is drawn from observations in the field and the approaches and techniques currently being used by attackers. In summary the Tactics are:
- Initial access – Chiefly this relates to phishing/spear phishing attacks with malicious attachments, brute forcing cloud-based email accounts, spear phishing emails with links to malicious domains and the use of harvested credentials.
- Persistence – Keeping access to networks for up to 6 months by moving laterally, compromising user and admin accounts and going from host to host, downloading additional malware and setting up scheduled scripts to maintain access.
- Privilege Escalation – Raising levels of access by compromising cloud administrator accounts and creating users with high levels of privilege.
- Credential Access – Using distributed and extensive password spray and guessing attacks.
- Lateral Movement – Moving from account to account as credentials are reset/updated.
- Collection – Gaining access to files and resources including emails, Sharepoint pages, user profiles.
The advisory reminds readers to review their detection, mitigation and response measures in the current threat environment.
Helpfully, it also contains a lengthy Appendix that identifies particularly concerning MITRE ATT&CK® Tactics and their corresponding Techniques categorised by industry sector and malware type. Readers will note that this is a significant and lengthy list of considerations, particularly as each technique may have several alternate or complementary mitigation procedures, that a defender might institute.
An important consideration is, irrespective of the level of defence in place, how do you incorporate the monitoring of these threats and visualise attacks, as they are happening, as part of your Security Operations?
Tracking attacks
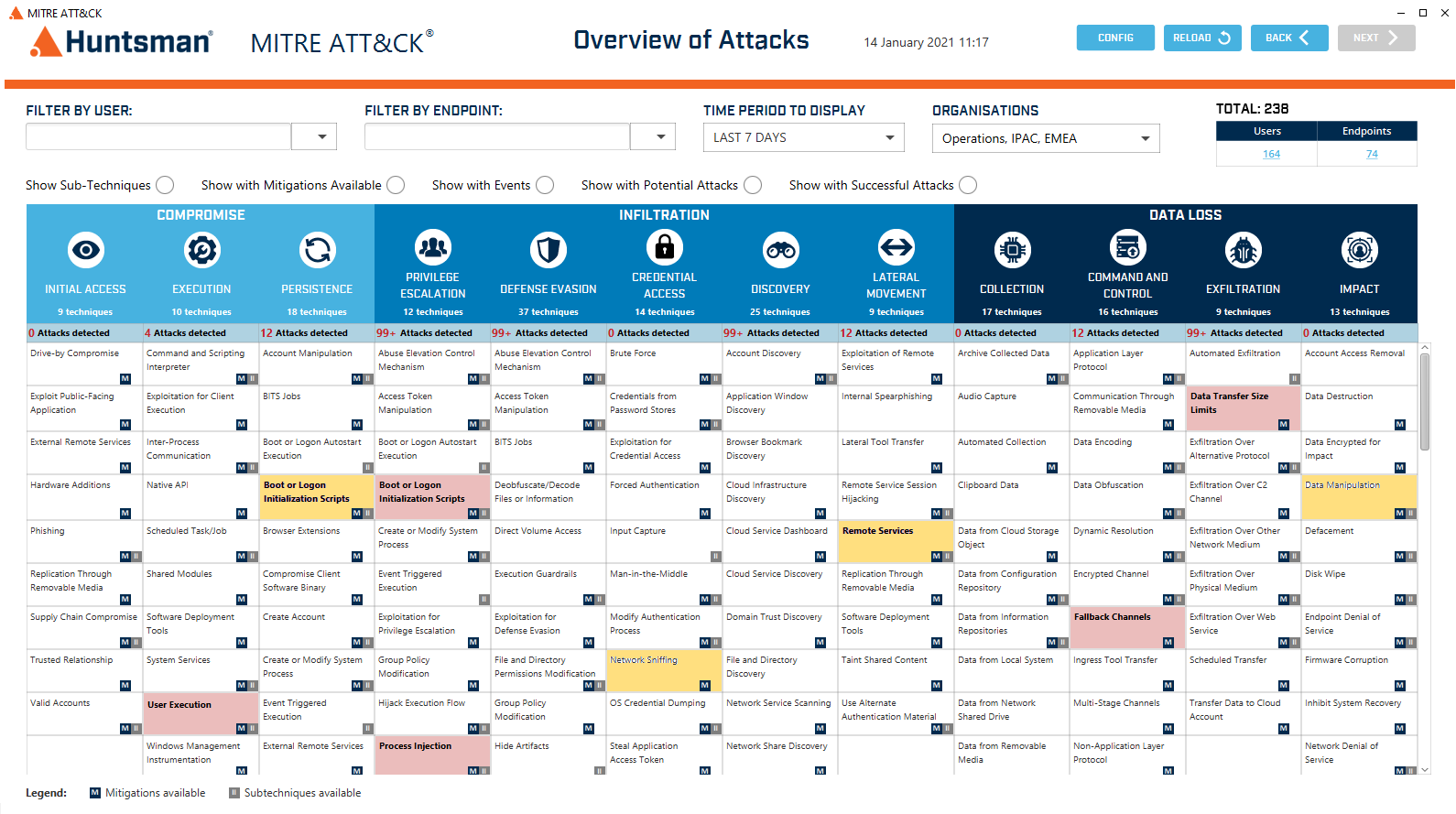
Some SIEM technologies have moved to quickly integrate the significant benefits of the MITRE ATT&CK® knowledge base into their detection, mitigation and response capabilities. For example, in the latest Huntsman Enterprise SIEM (V7) the associated detections of events and alerts are automatically visualised on MITRE ATT&CK® heatmap displays to show the tactics and techniques currently detected across the monitored environment and their progress towards their malicious objective.
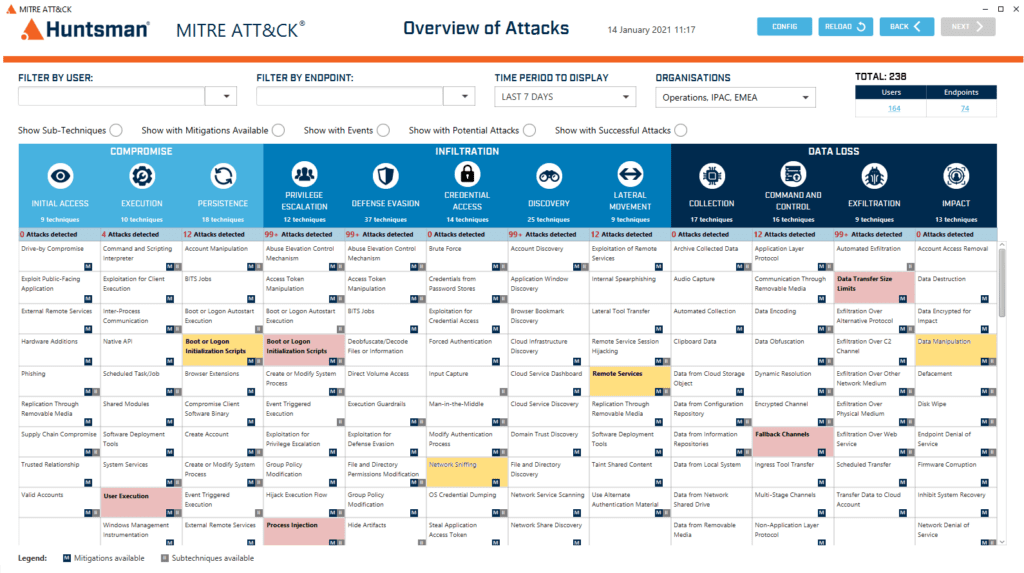
Huntsman MITRE ATT&CK® Heatmap
Each cell is colour coded, to highlight the scale, number or volume of observations. With this sort of information at hand, it can quickly be used to gain an understanding of what attacks are being experienced, how far they are along the “kill chain” and importantly the relative importance of a specific response.
Monitoring isn’t everything
Of course, monitoring alone isn’t enough. Controls need to be in place and operating effectively to defend systems against attacks too. This means configuring in-built security settings as well as deploying prevention, containment and recovery controls to enhance your cyber security posture.
The ACSC advisory also reminds organisations to remain vigilant against ransomware attacks and the importance of good cyber hygiene in those efforts. Again, this has been a major focus of the new Huntsman Security SmartCheck for Ransomware solution which measures and reports on the effectiveness of 12 key security controls to enhance your cyber posture and combat ransomware, one of today’s most prevalent threats.
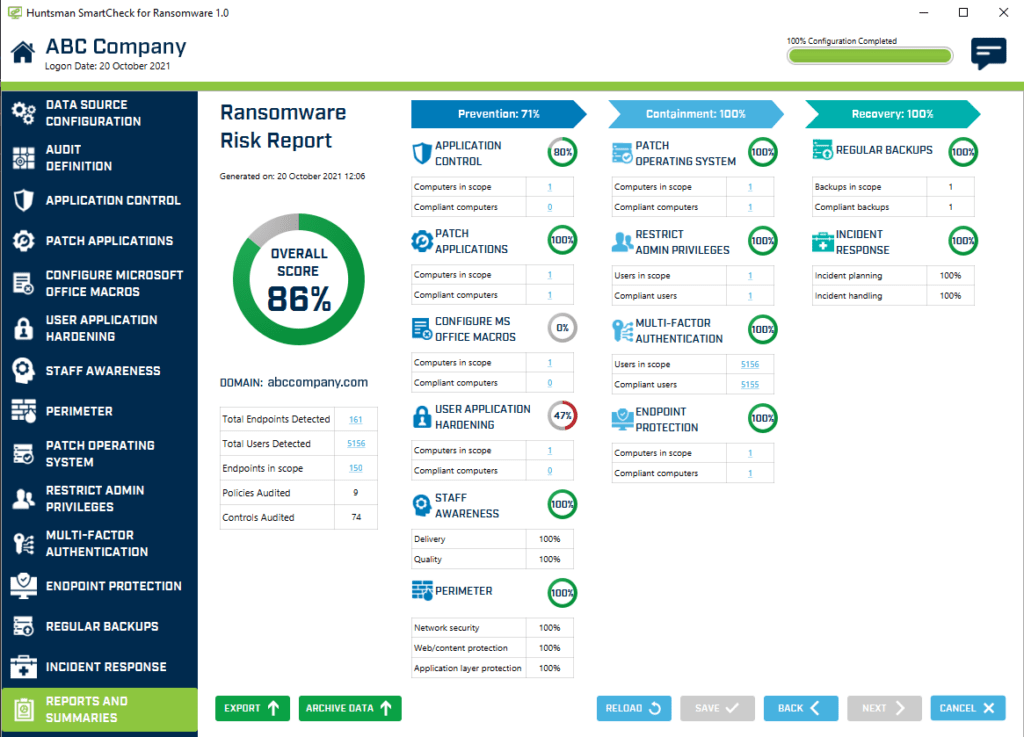
SmartCheck for Ransomware control report screen
Find out more about the MITRE ATT&CK® heatmap here and SmartCheck for Ransomware here.
 About Huntsman
About Huntsman