This blog post ‘Identification and Authentication – How to improve cyber hygiene’ is the fourth in a series on Cybersecurity Maturity Model Certification (CMMC) – a US Department of Defense (DoD) initiative that imposes requirements on contractors and subcontractors to help safeguard information within the US defense supply chain.
You can read the first three blog posts here, here and here. In this post, we take a look at the security disciplines of Identification and Authentication and how organisations can fulfil the CMMC requirement to achieve a more robust approach to securing this important aspect of their security architecture.
Unique Identifiers
If you want to develop the cyber hygiene of your organisation’s identification and authentication, every device, user and software product that interacts with your network should authenticate using strong credentials that cannot be easily brute forced. This is a very broad statement and one that may be hard to meet in its entirety, but as a goal for your enterprise architecture, it’s an excellent security target to aim for.
Unique device identifiers, like MAC addresses and IP addresses can be used to determine which devices are doing what on your network, while individual identifiers for users, usernames that are uniquely tied to specific users and are not shared, should tell you who is logged on and what assets (systems and information) they are interacting with. Administrators are no different, they also need unique names that tie to individual people, so you always know which administrator carried out a particular management action, and any service accounts used by software (operating system or specific to applications) also uniquely identify which application they are linked to.
The reason why this is so important is that organisations often start with the premise they can share accounts between users (shift workers or administrators), and applications often install using default computer accounts, such as local administrator, the user account that installs them or the local system account, all of which mean the application’s individual activity is impossible to trace though the event logs when something goes wrong.
Authentication
Authentication is the process of logging into a system and acting as the gatekeeper for granting access to resources for users, applications and devices. By tightly controlling the authentication architecture, you can confirm the identity of those accessing your organisation’s resources and guarantee those who gain access can only access the assets you intend.
Commonly, we rely on passwords to authenticate our users, but passwords are increasingly becoming an insecure means of proving a user is who they say they are, because passwords are easily guessed, brute forced or credentials are stolen in phishing attacks or compromises on other systems where passwords are reused. The issue with passwords is they cause the user problems, because the ease of guessing using dictionary attacks and brute force attacks means we’ve pushed the users into having to remember an ever increasing complex combination of unmemorable character strings, which often results in their reuse or being written down, both of which are also insecure practices.
Password managers can help with the complexity and length issues, of course, but they don’t stop our users being phished, which is the primary source of account compromises. Phishing is certainly the scourge of the Internet and is so common it’s cited in many places as being the number one way that organisations are hacked.
To make the authentication process more robust, the Australian Cyber Security Centre (ACSC) included a simple solution to the password problem in its list of eight critical security controls that all organisations should adopt to secure their business from targeted attacks (the Essential Eight). Multifactor authentication (MFA) is the use of two or more types of authentication, where additional means to prove the user is who they say they are combine with the password, such as a special code, token or biometric such as a fingerprint.
Authentication factors are cited as falling into three categories, as follows:
- Something you have (token, smartphone application)
- Something you know (password);
- Something you are (biometrics).
Choosing two or three of these mechanisms for the initial access request for users getting onto the network is today considered good practice, but organisations are increasingly using MFA inside the network too, ensuring that malicious insiders are also thwarted using this technology.
Getting started with MFA
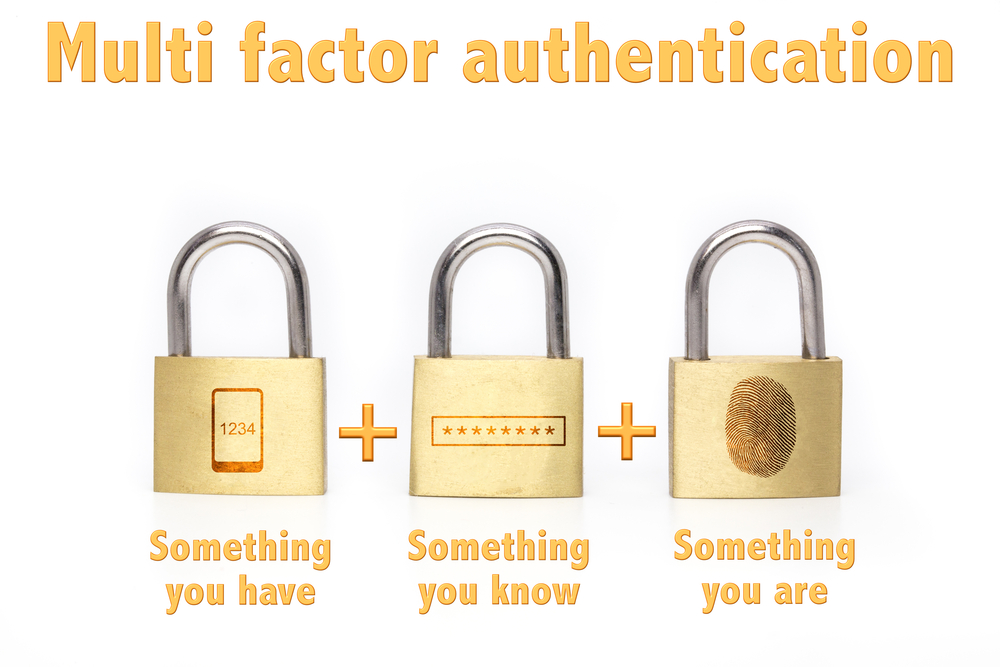
The elements of multi-factor authentication
A great place to start with multi-factor authentication is to enforce its use for remote access, that way every user attempting to log into your systems from outside the local area network must have the other factor of authentication available to them before the gatekeeper lets them in. For example, a user logging into your network from home might be challenged with a one-time pin code that’s sent to them via email, or they might be required to supply a special code obtained from a software application running on their smartphone. Even if the user is duped into divulging their username, password and a code through a phishing attack, the attacker cannot reuse the credentials to access the organisation since the code is one-time use only.
Audit and authentication
Being able to prove a user acted in a certain way and tying the user to their actions through multiple forms of authentication means you now have an audit trail of activities to investigate if something does go wrong. However, the ledger of audited activity based on a higher level of certainty that you know who did what and when they did it means your investigations are easier and getting to the bottom of what happened in a manner that may prove to be reliable evidence in court. The outcome of court sounds extreme, and in many cases, it never gets that far, but if your systems generate good quality, admissible evidence and preserve records in a secure manner, if you did have to provide records to a court, they have better chance of being considered strong proof of actions.
How SIEM supports Identification and Authentication
The CMMC suggests you use multi-factor authentication to protect users logging into your systems. Each identification and authentication action results in an event generated by your system, so you can trace who did what and when. By collecting these events into a SIEM, a central logging database that ensures those records are stored securely, your security team has a systematic cataloguing process that makes investigation of attacks and potential user missteps very quick and comprehensive.
Next generation SIEM technologies that incorporate threat intelligence and behavioural profiling also have the added bonus of being able to detect and verify threats as they happen – sending alerts to the security team to enable immediate investigation and remediation of incidents.
 About Huntsman
About Huntsman


