The Australian Cyber Security Centre (ACSC) maintains a guideline called ‘The Essential Eight: Strategies to Mitigate Cyber Security Incidents’. Government departments’ cyber resilience is measured against these controls. Research shows that successful implementation of the Essential Eight fends off 85% of targeted cyber-attacks, so it’s a very sound security strategy to follow.
Let’s explore the ACSC’s Cyber Maturity Model[1] for Essential Eight compliance to understand how it works, what to look out for and why you should apply it within your organisation.
What are Cyber Maturity Models?
Maturity models have been around for decades, coming from research carried out by the US military. In essence, maturity models measure process or implementation maturity, where five levels are used to report on the organisation’s approach to a given outcome.
With cyber security, ACSC’s Essential Eight cyber maturity model helps organisations determine compliance with those eight critical security controls:
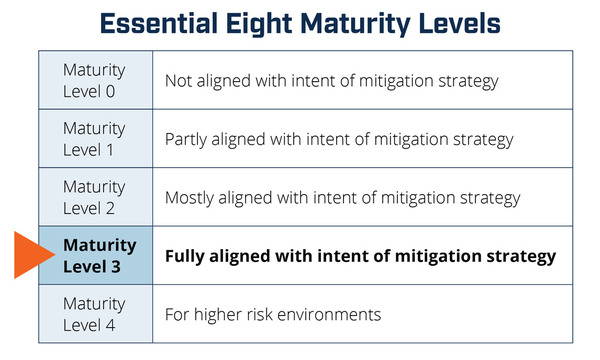
As a rule of thumb, organisations are encouraged to aim for a maturity level of three, since at level three controls are institutionalised and consistently implemented across the entire organisation.
ACSC advises that organisations, such as critical infrastructure providers, that are under continued and unrelenting attack by highly skilled adversaries – known as advanced persistent threats (APTs) – should strive for level four maturity (the highest level), as at this level, security controls are performing at their best.
Essential Eight Maturity in Practice
You and your security team should start by preparing an honest current state review. It’s easy to self-assess at maturity level three without looking at the underlying implementation detail. Yet, the detail is where the weaknesses can negate the value of the control. To achieve maturity level three against the Essential Eight’s Application Whitelisting control, for instance, the following conditions need to be met:
- Application whitelisting is implemented on all workstations;
- Whitelisting of executables, software libraries, scripts and installers is enforced;
- Application whitelisting is implemented on all important servers (e.g. Active Directory, email servers and other servers handling user authentication); and
- Whitelisting of executables, software libraries, scripts and installers is enforced.
If any of these conditions are not met, you can’t claim level three maturity for Application Whitelisting. At level three, the solution must extend to all important servers, whereas at level four, it has to extend to all servers. The reality of Application Whitelisting is that it is a powerful security control, preventing unknown software from running on your systems. Yet anyone who has implemented Application Whitelisting knows how hard it is to set up, with significant integration and software distribution overheads, leading to an increase in service desk calls and inflated costs.
If Application Whitelisting runs on workstations, it prevents so-called drive-by downloads running on your systems and stops viruses and malware launching from malicious email attachments.
The Devil in the Detail
Looking into the detail is when things get interesting. Take the control called, Configure Microsoft Office Macro Settings. At cyber maturity level three, the following requirements are specified:
- Only Microsoft Office macros in Trusted Locations with limited write access can execute;
- Microsoft Office macros from the Internet are blocked; and
- Microsoft Office macro settings can’t be changed by users.
By implementing these requirements throughout your organisation, many common macro viruses will be stopped. Most harmful macro code comes from malicious email attachments hidden within spreadsheets or documents. When you open these malware files, the Visual Basic for Applications (VBA) code hidden inside executes and the infection takes hold. With these macro controls, rogue code cannot run since it is identified as originating from the Internet. Users can continue to write their own macros and publish them inside the organisation within Trusted Locations, so no functionality is lost.
If you prefer to aim for cyber maturity level four (targeted at higher risk environments such as critical infrastructure), then the requirements change as follows:
- Microsoft Office macros are blocked from executing and Trusted Locations are disabled; and
- Microsoft Office macro settings can’t be changed by users.
At cyber maturity level four, all macro code is blocked. There is no doubt that this is a more secure configuration, but it renders VBA unusable by all users. If your users rely on macros then level four isn’t a tenable security target, since the loss of functionality won’t be tolerated by the business. In this case you could seek an alternative way to achieve the same level of risk reduction, such as through monitoring what macros do when they run and alerting your Security Operations Centre when something malicious occurs.
Monitoring and Essential Eight Maturity
The Essential Eight controls are the most fundamental security requirements you can implement to protect yourself from hackers. Monitoring compliance of your security controls allows you to ensure your defences remain effective as your systems change and threats evolve. Let’s look at one of the E8 controls ‘daily back up of important data’, as an example.
Without good backups, it’s hard to recover from a ransomware infection. Regular verified backups allow you to revert to a good copy of your data, eradicating the infection from your system. By monitoring your backup system using system management tools or by having your security team monitor them using your Security Information and Event Management (SIEM) system, you can monitor compliance and fix issues when they appear.
Cyber Maturity Common Sense
Your organisation’s cyber maturity may not be aligned to the Essential Eight security controls as there are many other recommended models, depending on the jurisdiction your business operates within; for example the UK NCSC’s 10 Steps to Cyber Security and North America’s C2M2 Model (originally established to measure maturity in the energy sector). However, there is no doubt the Essential Eight provides an excellent baseline for security.
Benchmark your organisation’s cyber posture against the Essential Eight with the
[1] ACSC’s Maturity Model https://acsc.gov.au/publications/protect/Essential_Eight_Maturity_Model.pdf
 About Huntsman
About Huntsman




