The need for assurance in supply chains and third parties is well-recognised in cyber security. It is common to exchange data – often sensitive – with third parties, and to rely on them for aspects of service delivery or the undertaking of key business functions.
As we saw recently in the Travelex ransomware case, the removal of services affected several banks that used the platform for their customer-facing foreign exchange services, even if it didn’t expose data.
Third party security assessments are not easy to undertake
There are a few approaches to conducting third party security assessments:
- Questionnaires
Questionnaires are possibly the easiest, and they scale well to large numbers of suppliers. But tracking the results across suppliers (and over time) is hard; and there is the perennial risk that people will over-report on the strength of their cyber security controls. They might identify areas of potential risk for follow up, but it would be difficult to rely on them in isolation. Hence the value of these is extremely low.
- Site visits
You can audit suppliers with site visits. This gets expensive, as each visit may take a day or more and consolidating the results takes effort. It is also a burden for the supplier if they have a large number of customers that wish to audit them.
- External scanning and intelligence services
Finally, there are external scanning/intelligence services. These are cheap and can scale, but the view of security risks they present are only those that are externally observable and very indirect, so they are more of a data point than a meaningful assessment.
Third party risk in the time of Coronavirus
So far so normal. But the pandemic we are currently experiencing, has made this already difficult task much, much harder to address and even harder to ignore. People may be confined to their homes and businesses may be shut, but they still hold personal data, they still need to operate online or critical services and they still need to protect information, as required by law.

The Coronavirus lockdown has had a number of impacts on the level of third-party risk:
1) Risks have increased in severity and uncertainty
Your own business is working in a constrained way; staff are working from home, possibly from less secure systems – with data being accessed and stored remotely. This is a risk that you can (have to) accept in the current circumstances. But it is also true of your suppliers – they will have data they need to access in similarly risky environments (which could include your data) and their provisions may be riskier than yours. Certainly, they will be less visible.
2) Site visits are impossible
At the moment in the UK, it is impossible to either travel to sites, or to meet people at them; this applies to your offices and data centres and those of third parties who may handle your information. If they are overseas this logistical challenge may persist for some time.
So traditional methods of conducting security audits need to be re-thought, and even the gathering of data as inputs to audit/assurance processes may need to be changed. For example, if a business has had to adopt home working then the state of patching and anti-virus on people’s normal office desktop PCs may be less important to data security than the way their home systems are configured.
3) Time is tighter than ever
Under normal circumstances security and wider audit programmes have a lot of ground to cover. Annual audit programmes will have been built around controls and risks and will occupy the time available to the audit teams, or the consultancy budget availability.
Likewise, for companies that are audited by their customers, there is an overhead in being on the receiving end of audits. Maybe a day or two per audit, maybe more, but when this is multiplied by the number of customers who wish to attend their sites to assess their controls – it becomes a significant undertaking.
With the virus disruption looking like it will occupy at least a three-month window, that means cramming the annual audit programme and a year’s worth of supplier/third party audits into three quarters (at best) of the normal amount of time. Time management –in terms of prioritising and maximising efficiency – is going to be key.
A higher assurance / lower effort approach
We’ve seen a renewed interest in the automation of the more time-consuming elements of the audit process – namely data gathering and analysis. Businesses seldom want to (or should) remove the expertise of the security/risk expert from their assurance process, but for a while (pre-coronavirus) there has been a need to support these experts better to avoid tying them up with unnecessary leg work and to make the audit process more consistent and objective.
Under the lockdown restrictions, the very features that enabled this have become more acutely in demand.
Remote data gathering
The ability to undertake data gathering activities without attending a site is crucial. Providing a software solution that can be used by a non-expert user to gather the control metrics and data means that the software can be installed and used to gather data remotely. Then the output can be gathered for central (or home based) analysis.
This works perfectly for large diverse networks, for any situation where there are scarce expert resources, and for all situations where there are a large number of audit targets – be that suppliers or business units. Separating the data gathering from the interpretation is a logical division of labour and expertise, especially if people are in different locations.
Better data and analysis
The other big gain is in the quality of data and data analysis.
Collecting data in an automated way means that a wider sample can be used. A human auditor might inspect a subset of systems and extrapolate the findings. A software tool can gather control metrics from the management systems and audit targets in their entirety, giving a better representation of the data, that is also analysed consistently using the same metrics and yardstick.
You avoid many of the biases that humans can introduce into the audit process. Selection bias is where data subjects are chosen to meet the needs or the assessor. An IT function wanting to show its best face might choose to report on/measure performance of the platforms that it knows are well managed and up to date. Whereas an auditor might want to choose those parts of a network where they are more likely to get interesting/notable outcomes.
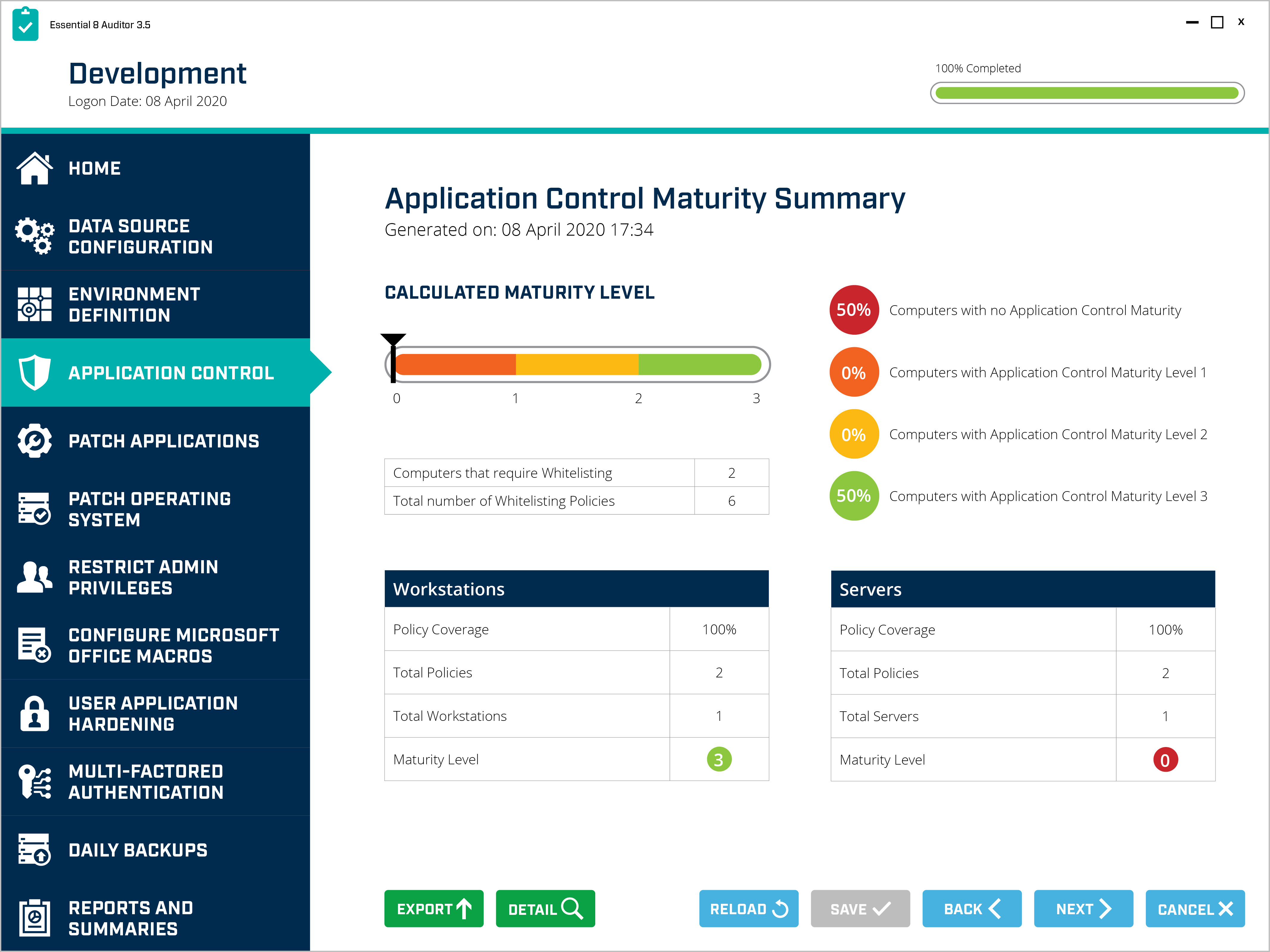 Essential 8 Auditor – Application Control Maturity Dashboard
Essential 8 Auditor – Application Control Maturity Dashboard
You also get the exclusion of “known issues” from reported data. Legacy application platforms that aren’t patched because they can’t be, or due to problems rebooting them without affecting services, can be excluded from the performance figures. But of course, they are still perfectly viable targets to an attacker.
The market demand
We’ve seen acknowledgement of these challenges in the increased demand for Audit solutions that reduce the need for site visits, optimise the time of the expert users and provide a consistent and comprehensive way to gather and analyse data across a broad environment. The impact of operating remotely, and in lockdown, on third-party cybersecurity risk is now becoming very evident.
During and post lockdown, when assurance processes need to work flexibly and efficiently, these cybersecurity audit technology features are key to the success of audit and compliance teams – especially those focused on third party or supplier assurance.
 About Huntsman
About Huntsman




