The MITRE Corporation released ATT&CK (Adversarial Tactics, Techniques and Common Knowledge) in 2013. It is a list of adversarial exploits and techniques that provide a knowledge base for security teams to defend themselves against the most complex and advanced persistent threats (APTs). This blog post gives an overview of the framework.
MITRE ATT&CK Matrices
There are a number of matrices, including: Enterprise, Mobile, PRE-ATT&CK and ICS for industrial control systems. Each one of these contains a structured list of known attacker behaviours that have been compiled into tactics and techniques; the tactics are ‘what’ attackers are seeking to achieve and the techniques are the ‘how’ (including mitigation and remediation strategies).
Tactic Categories
There are 11 tactic categories within the Mitre Attack Framework, each with a ‘current’ list of known techniques that have been observed to have been carried out by adversaries. The image below gives an indication of any attacker’s list of objectives and strategies to achieve them.
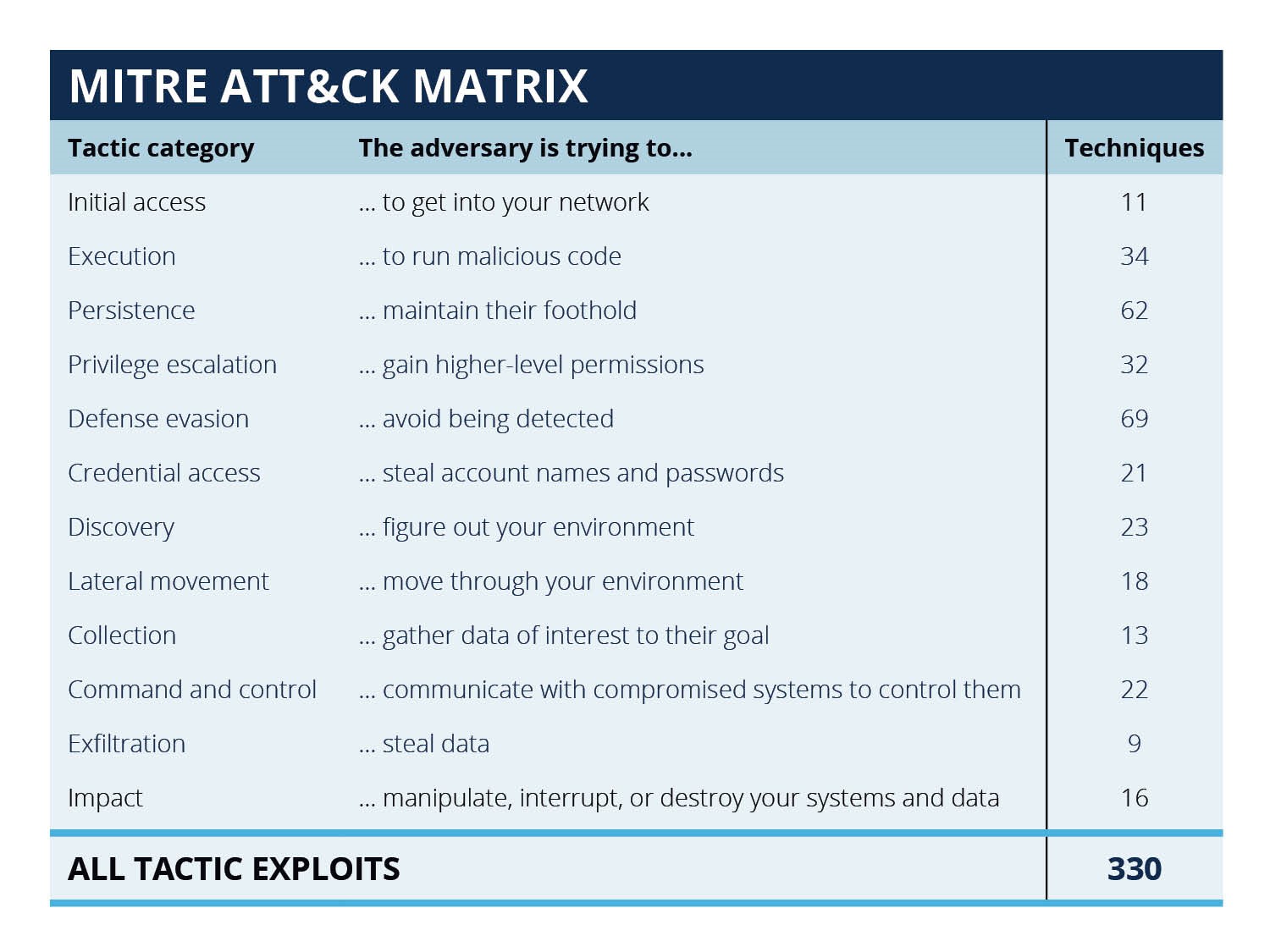
MITRE ATT&CK Matrix – tactics
The latest MITRE ATT&CK Enterprise Matrix can be found on The MITRE Corporation’s website here: https://attack.mitre.org/matrices/enterprise/
MITRE ATT&CK Mitigation Strategies
There is a large number of strategies that have been developed to mitigate the known adversarial tactics and techniques of APT attacks. The latest published list contains 41 enterprise level mitigation strategies, an excerpt of which is here:
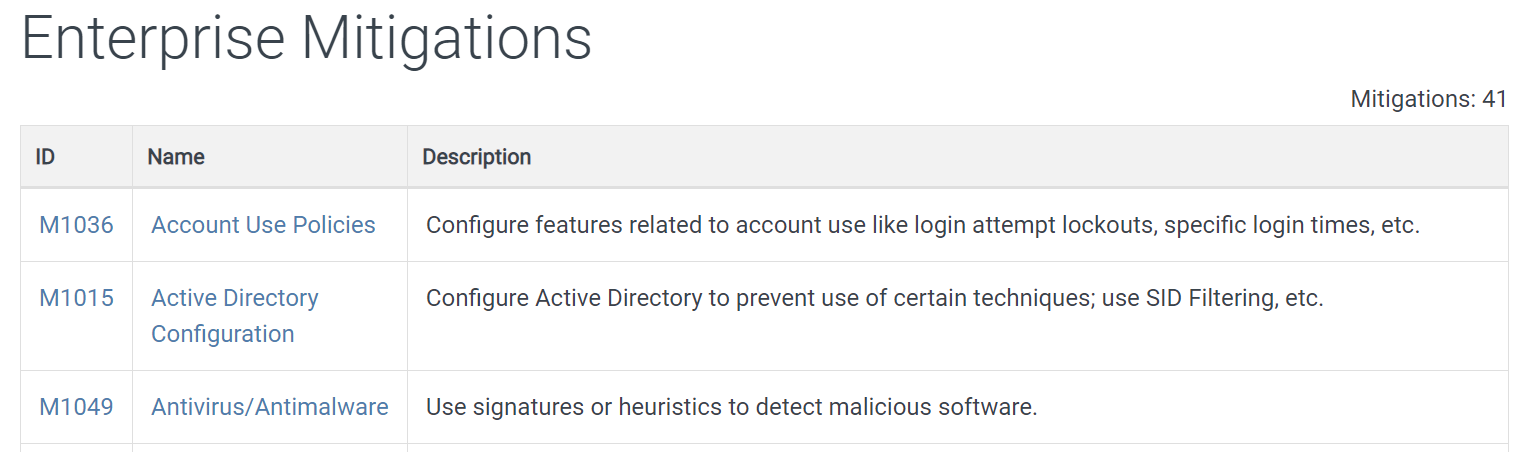
Excerpt from The MITRE Corporation’s list of enterprise mitigations
A full list of MITRE ATT&CK enterprise matrix mitigation strategies can be found on The MITRE Corporation’s website here: https://attack.mitre.org/mitigations/enterprise/
Will MITRE ATT&CK help your organisation?
If you are embarking on the implementation of MITRE ATT&CK mitigation strategies, you are most likely already functioning at the vanguard of defence grade cyber security, operating threat hunting and red team / penetration testing activities; the matrices require the commitment of significant resources and skill to establish and maintain the strategies. If you’d like to explore how Huntsman Security can support you with this, please don’t hesitate to contact us using the link below.
Cyber hygiene – a prerequisite to MITRE ATT&CK
Regardless of whether you are ready for one of the MITRE ATT&CK matrices or not, it’s worth checking to see if your operation has the fundamental security controls in place and operating effectively. If you have missing patches on systems, weak passwords on standard accounts, or users willing to click on links that point to malware – you are giving an attacker a choice of which point of failure to exploit. For organisations where cyber security is critical there is another dimension to consider – compromises in fundamental cyber hygiene are the entry point for more complex and advanced cyber-attacks.
Focusing on cyber hygiene doesn’t mean ignoring the bigger issues. Rather, it is about making sure you have the most common access points covered and maintained.
Where to start
Determining what the cyber hygiene fundamentals are varies according to the source of the advice. The Australian Government recognised this challenge and devised a security framework, the ACSC Essential Eight, that distils the wide range of published security controls down to the most critical and universally recognised; they deliver the biggest ‘bang for your buck’ in terms of defending networks from cyber threats and provide an excellent cyber resilience baseline for all organisations. In the UK, Cyber Essentials, the UK Government information assurance scheme, comprises a framework of five mitigation controls.
A key benefit of implementing and maintaining critical security controls is that the effective management of each of them will successfully simplify the number of MITRE ATT&CK Matrix techniques that require bespoke risk mitigation efforts.
Regardless of your organisation’s current cyber maturity level, benchmarking your performance against a small number of critical security controls is fundamental to establishing, developing and maintaining cyber resilience.
 About Huntsman
About Huntsman




