Our cyber security products span from our next gen SIEM used in the most secure government and critical infrastructure environments, to automated cyber risk reporting applications for commercial and government organisations of all sizes.
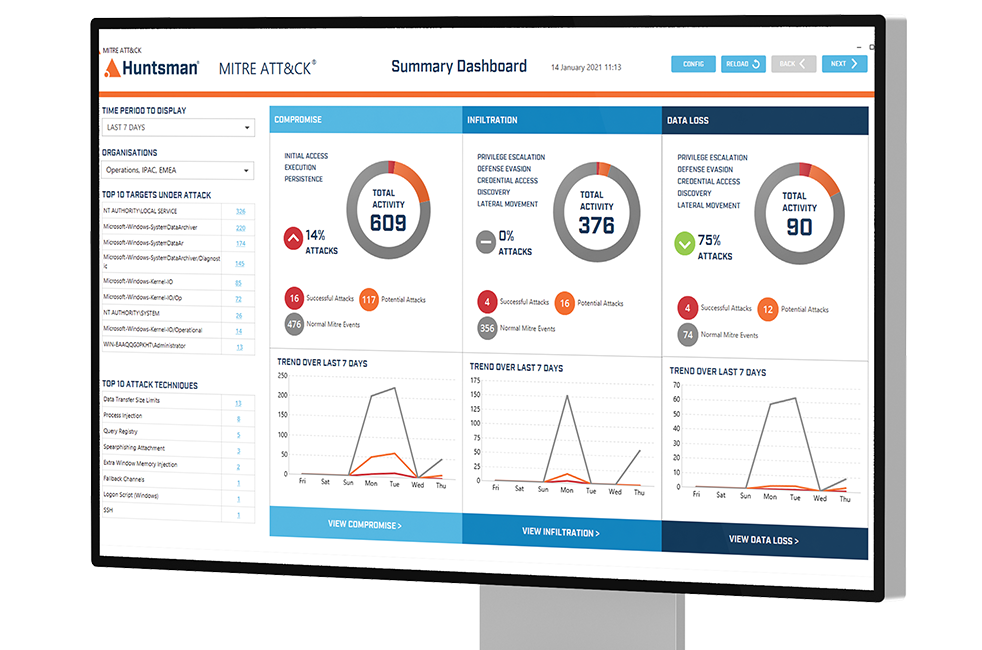
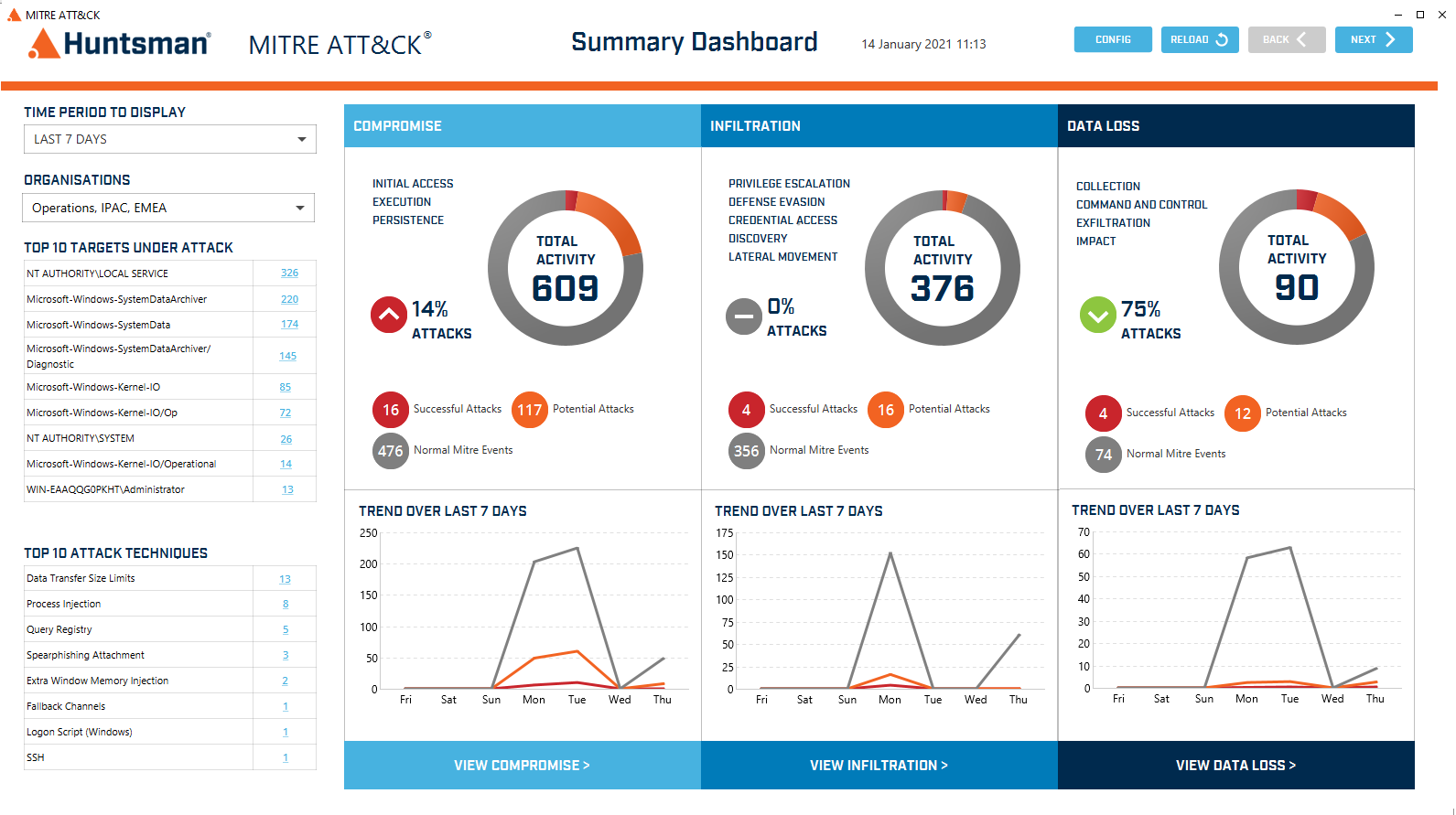
As cyber-attacks become more sophisticated, increasing numbers of threats are inevitable. To better support MSSPs, we have developed responsive in-stream processes that minimise hand-offs, for faster and more accurate threat detection and response management.
Huntsman Security’s MSSP SIEM analyses and prioritises alerts in real-time, for quick investigation, escalation and resolution, to deliver highly efficient automated workflows.
Regardless of the number of organisations you’re managing with our single instance MSSP SIEM, your team can pinpoint specific assets / users at risk, and quickly tailor an effective defence, by leveraging the attack information provided by multiple tenants, users or endpoint views.
By supporting the complete detection, analysis and response process, the Huntsman MSSP SIEM offers greater levels of efficiency and reliability to your team, by reducing analyst workload and increasing their ability to quickly manage threats. The Huntsman MSSP SIEM also features easy on-boarding of new customers by utilising standardised but flexible technology to support the ongoing development of new value-added services for your customers.
Learn the what, how and why of the MITRE ATT&CK® framework and its critical role in mitigation, detection and reporting on cyber security operations.
Download the guide
Huntsman Security’s SIEM sits at the core of your Security Operations Centre (SOC) as a single, comprehensive, yet flexible multi-functional threat monitoring and response platform
LIVE INTERFACE & VISUALISATION
Real-time MITRE ATT&CK® heatmaps and threat summary + GUI driven query interface to optimise investigation and save time
Configurable alert rules and behavioural models, allowing the detection of the widest range of threats – including APTs
Centralised management & coordination of alerting rules, event collection, queries and reports for reliable security governance
Lifecycle visibility of alerts, threats and incident information for all stakeholders
SPEED & PERFORMANCE
Advanced, high speed in-stream event processing, analytics and response decision making – with capacity in excess 100,000 events per second
Behavioural anomaly detection to extend discovery beyond predefined patterns and signatures with machine-learning
Automatic collection and integration of multiple sources of Threat Intelligence, for enrichment, threat verification and orchestration, to speed up resolution of incidents and reduce false positives
Accelerated capacity for cyber security decision making with multiple views of attack information by users or endpoints, to pinpoint an asset/user at risk and quickly tailor a defence
WORKFLOW & SCALABILITY
Simple, yet flexible, deployment options and scalable data storage architecture
Support for virtualisation and cloud/on-premise deployment
Optimised for detection, correlation and reporting OOTB – an extensive range of inbuilt alerts for attacks, technology types and compliance standards
Support for a wide range of data sources and technology platforms (hundreds of technologies supported natively + data stream or source can be configured)
Broad range of pricing and licensing models to suit organisations of all sizes and complexity (inc. Capex and OpEx subscription pricing)
Read by directors, executives, and security professionals globally, operating in the most complex of security environments.