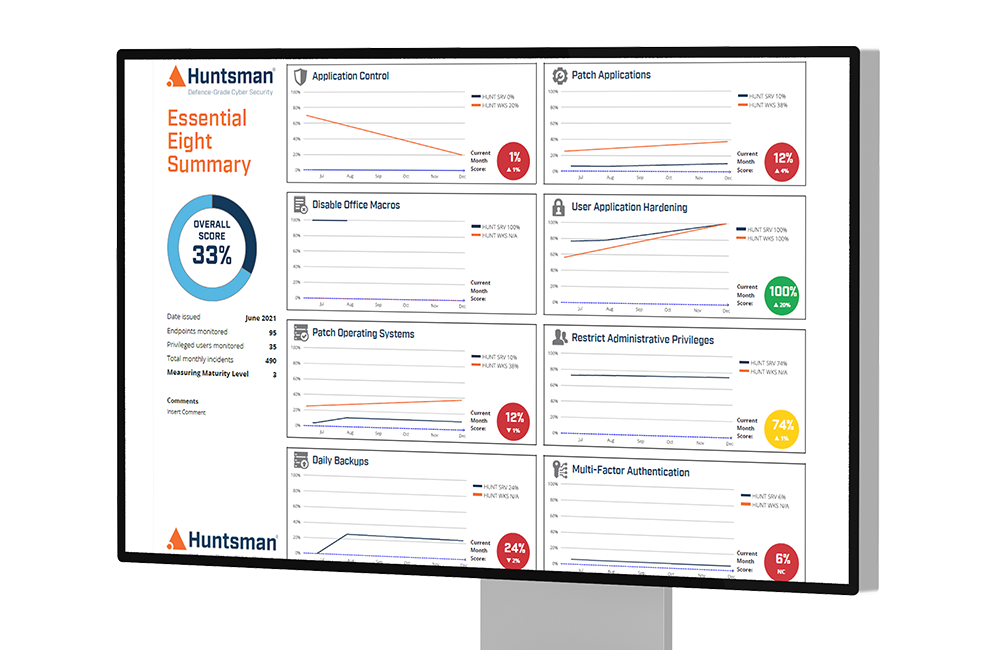
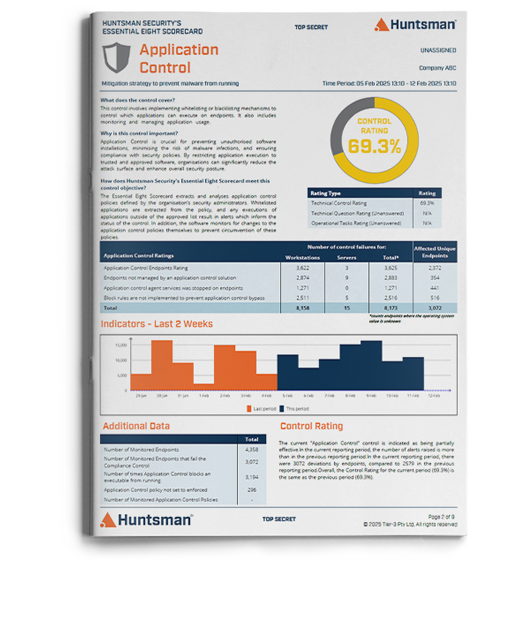
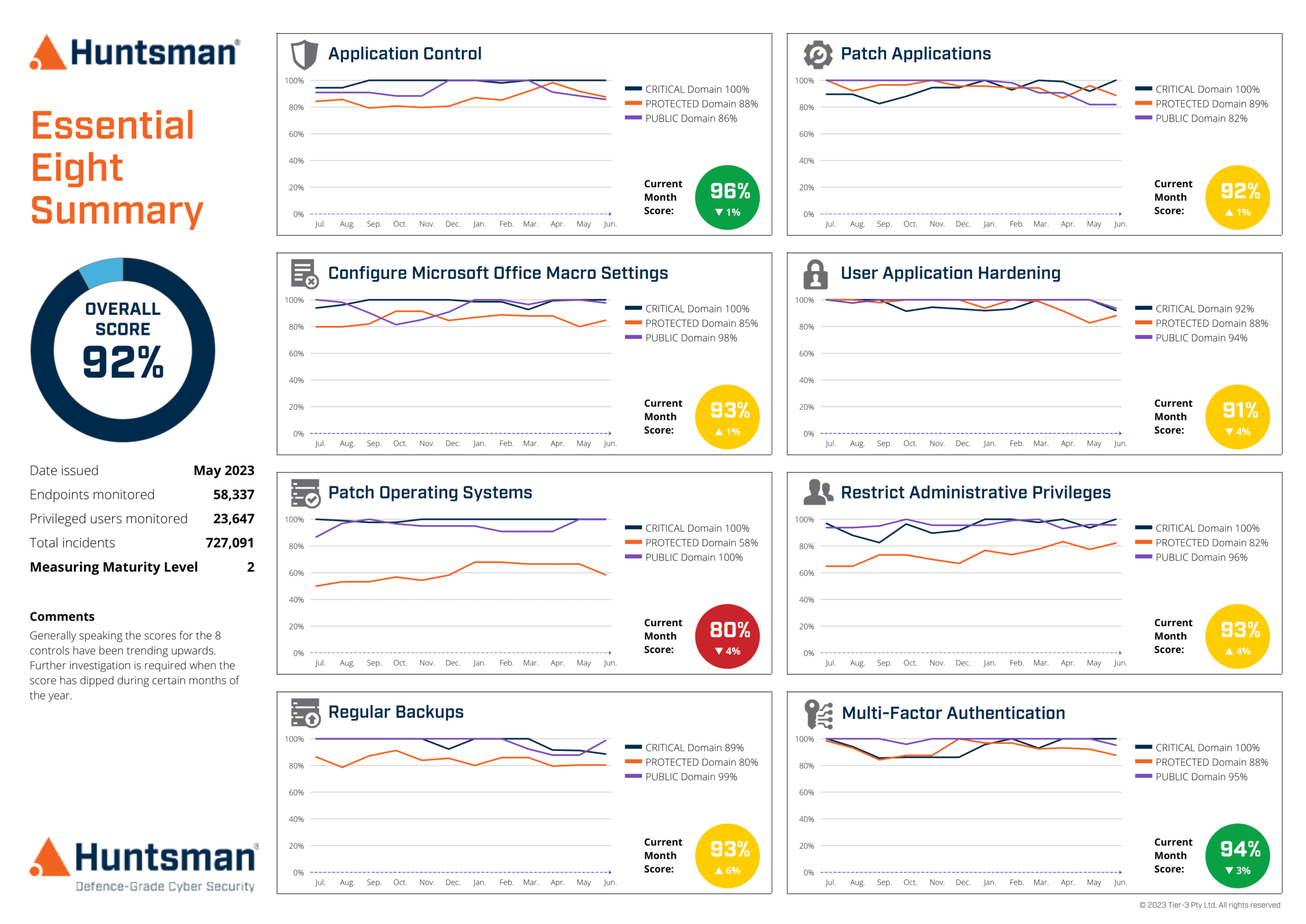
The Essential 8 Scorecard is an award-winning cyber risk management technology that continuously measures the effectiveness of your organisation’s security controls against the ACSC Essential Eight Maturity Model.
Unlike traditional surveys or one-off arbitrary assessments, the Essential 8 Scorecard delivers an objective, quantitative, and ongoing view of your organisation’s cyber posture. It enables you to dynamically manage your exposure to a changing threat environment— with the accuracy, timeliness, and the confidence that only systematic and continuous monitoring practices can provide.
With built-in Threat Exposure Management (TEM) capabilities, the Essential 8 Scorecard automatically verifies the security of your IT systems and assets, measures their vulnerability, and reports on any change in your cyber security controls necessary to keep your organisation protected.