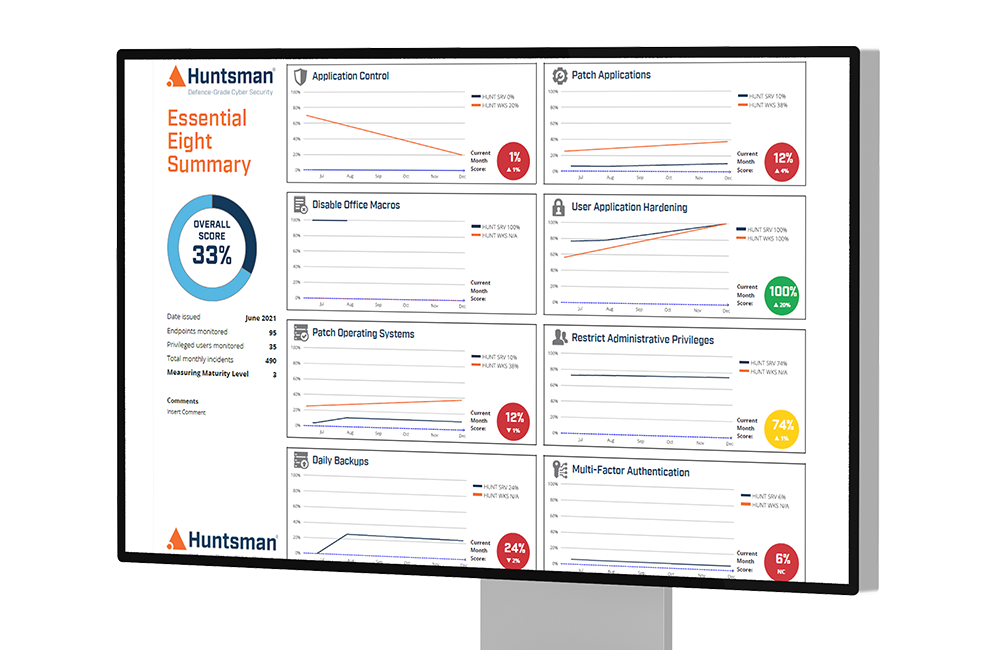
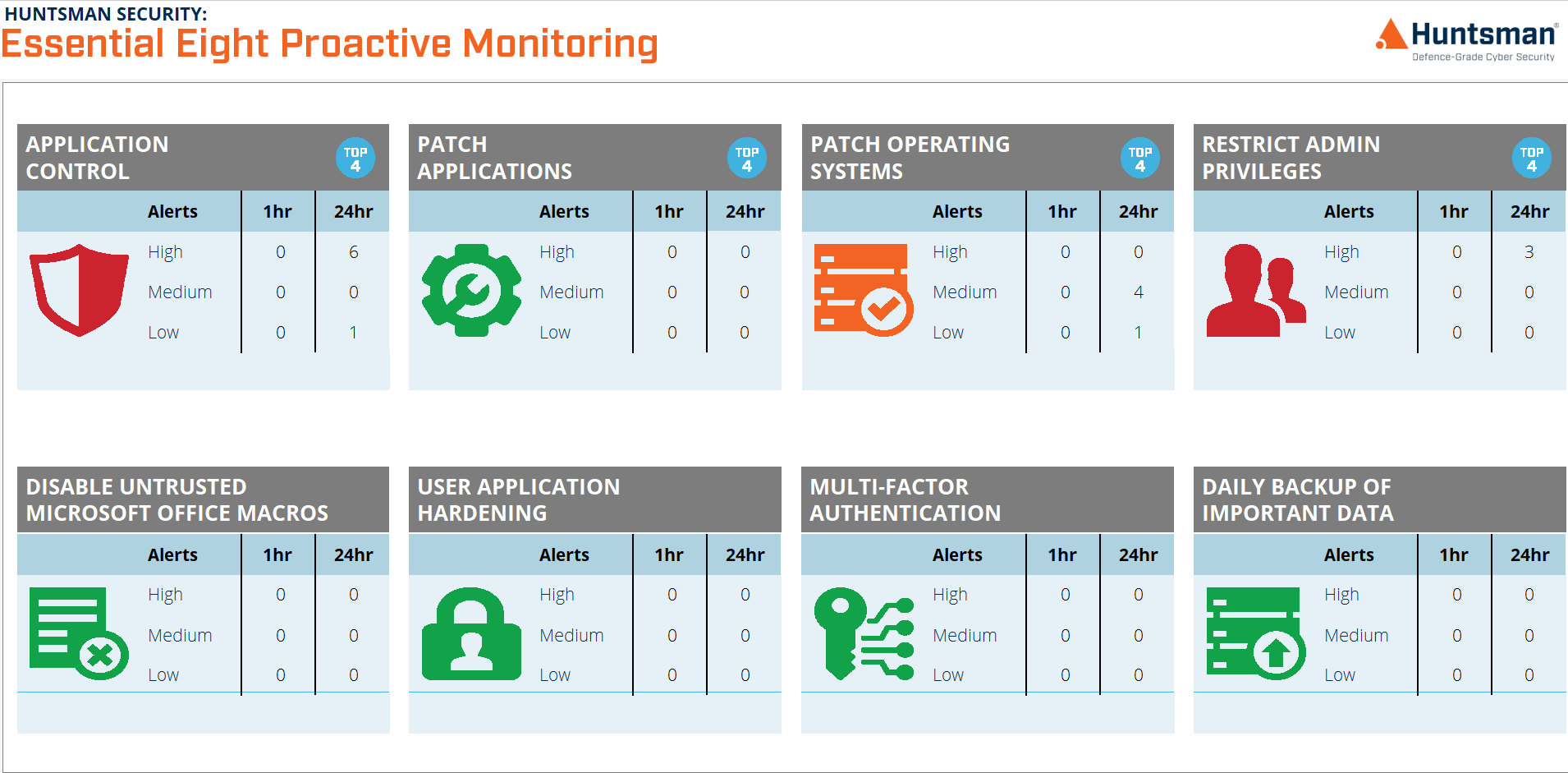
The Essential Eight security controls – what they are and why they are important
The Essential Eight Framework was developed by the Australian Cyber Security Centre (ACSC). It is a prioritised list of practical security controls that organisations can implement to make their information more secure.
No matter what jurisdiction you are in, or which framework your government recommends, the key eight security controls are recognised as critical to cyber resilience.
Meet regulatory requirements with the help of Essential 8 Scorecard
As cyber risk has evolved into a mainstream business risk we have seen a wide array of cyber risk maturity models appear in regulations and governments recommendations, including Australia’s APRA CPS 234 and ASD ISM , C2M2 through to the US CMMC model. The requirements that are common to almost all maturity models are: assessing that security controls have been implemented correctly, monitoring the ongoing efficacy of security controls and auditing of security controls (including those maintained by related parties and third parties). The Essential 8 Scorecard undertakes these activities systematically and continuously to help defend your organisation against cyber attacks.