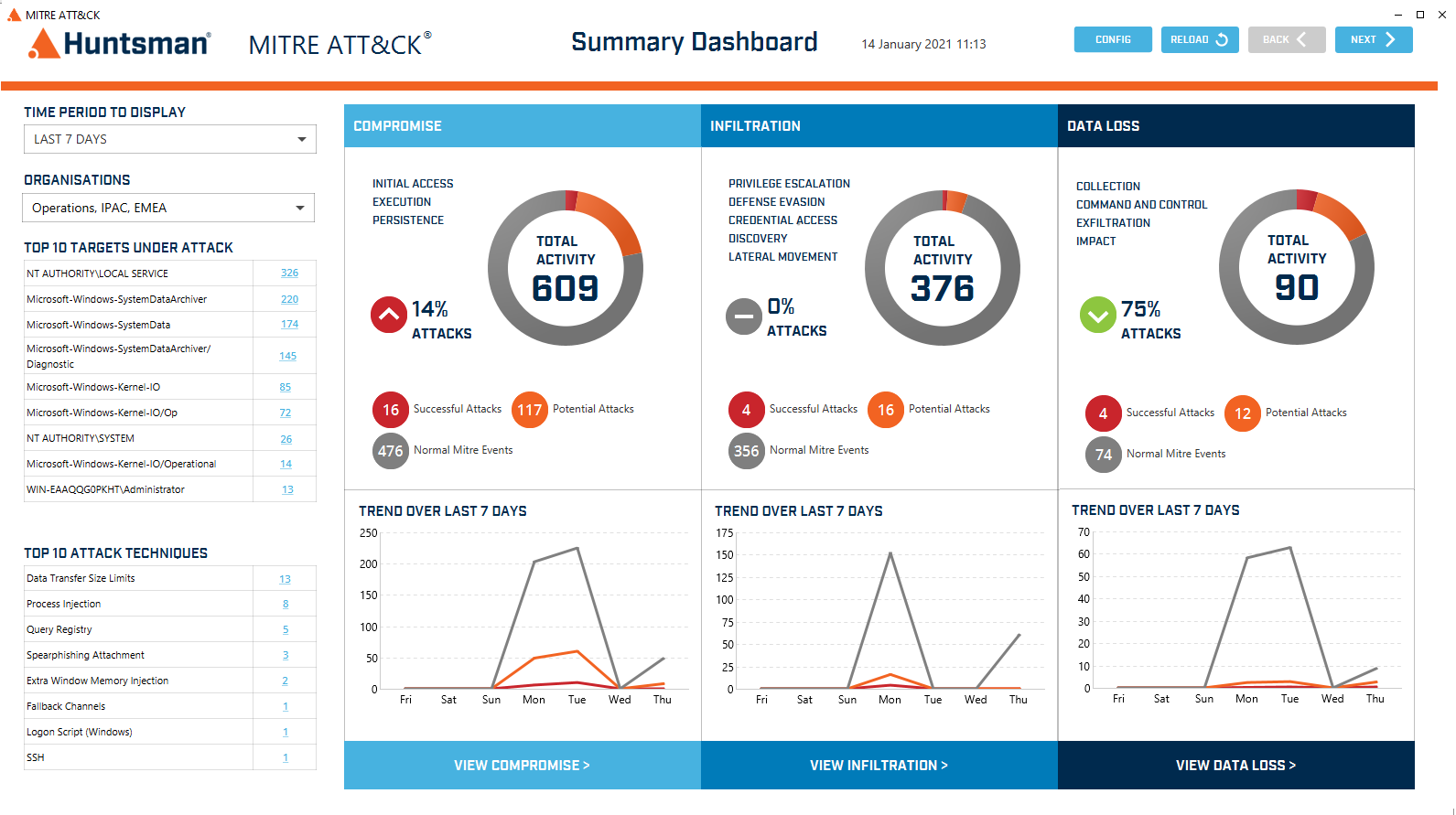
Our cyber security products span from our next gen SIEM used in the most secure government and critical infrastructure environments, to automated cyber risk reporting applications for commercial and government organisations of all sizes.
-
Products
Products
-
Solutions by Industry
Solutions by Industry
Any organisation can be the target of cyber attackers or find itself exposed through the actions of malicious insiders. Leverage our industry specific cyber security awareness to help reduce risk.
Industries
-
Learning & Resources
Learning & Resources
Access our industry-leading resources to improve your cyber resilience
Trending this Month -
About Huntsman
 About Huntsman
About HuntsmanSince 1999, Huntsman Security has been on the cutting-edge of cyber security software development, serving some of the most sensitive and secure intelligence, defence and criminal justice environments in the world.
Quick Links
- Blog
- Partners
- Contact Us