Our cyber security products span from our next gen SIEM used in the most secure government and critical infrastructure environments, to automated cyber risk reporting applications for commercial and government organisations of all sizes.

for all organisation types and sizes

with easy to access alerts and reporting

to reduce analyst workloads, simplify threat investigation and limit the time at risk

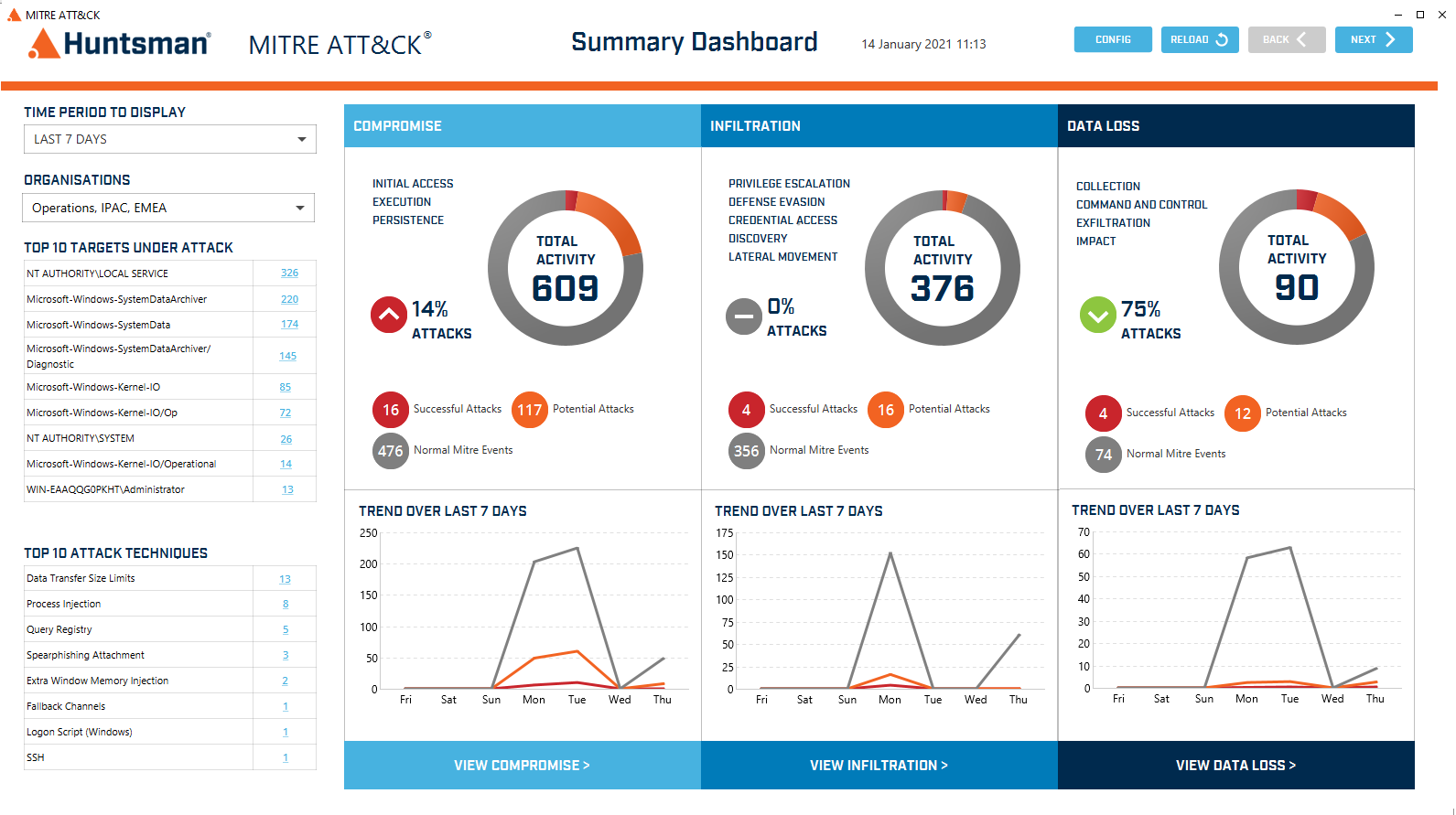
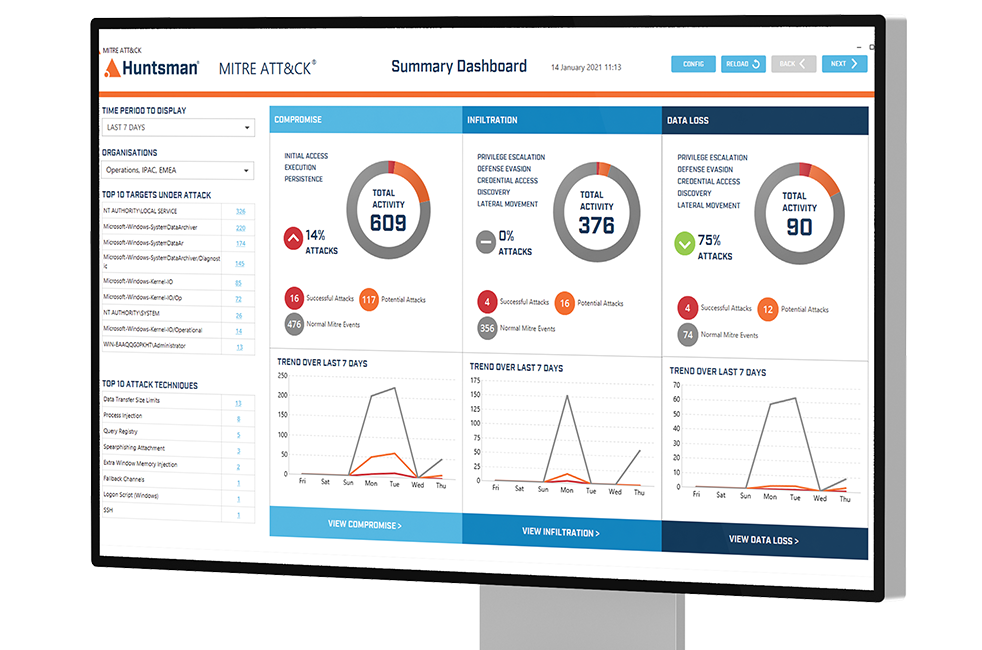
MITRE ATT&CK® Summary Dashboard
The cyber adversaries that once targeted the government, defence and intelligence sectors are now focussed on the wider economy. Any business of any size in any sector can fall victim to a well-resourced and motivated attack.
Huntsman Security’s Enterprise SIEM is trusted by defence agencies and government departments, as well as businesses globally. It is easy to implement, offering a highly efficient cyber threat detection and response solution for your organisation. Our experience in defending against today’s increasingly sophisticated cyber-attacks, and providing reliable defence-grade security threat detection, incident management and compliance reporting solutions, is as relevant to the commercial sector as it is to sensitive government systems.
Whether your organisation follows a broad framework like ISO27001 or NIST; is subject to industry standards like HIPAA, PCI-DSS or other regulations; compliance is a major part of security risk management and good governance.
With a comprehensive library of out-of-the box alerts, rules, queries and customisable dashboards, Huntsman’s Enterprise SIEM, enables you to quickly analyse threats, establish control effectiveness and network activity; for actionable reporting and alerting.
Enterprise SIEM’s advanced, high speed in-stream processing and analytics engine is limited only by its virtualised, cloud or hardware platform. Deployments routinely handle in excess 100,000 events per second. Flexible back-end storage and data archive management means data is available, queryable and retained to suit any use case.
Automated data collection and multi-source threat intelligence ensures detection and data enrichment, to hasten high-speed telemetry, threat verification and response orchestration, and speed up incident resolution of only verified threats.
With its defence, telecommunications and managed security services credentials, Huntsman’s Enterprise SIEM is proven in mission critical environments under the most demanding conditions.
Successfully dealing with the time-critical demands of threat resolution and compliance, with security standard accredited environments like the UK’s GPG13 and the Australian ISM, means that Enterprise SIEM is up to the task.
For enterprise customers, this means having complete faith in the ability of Enterprise SIEM to meet your monitoring and threat detection needs in efficient, reliable and flexible ways.
|
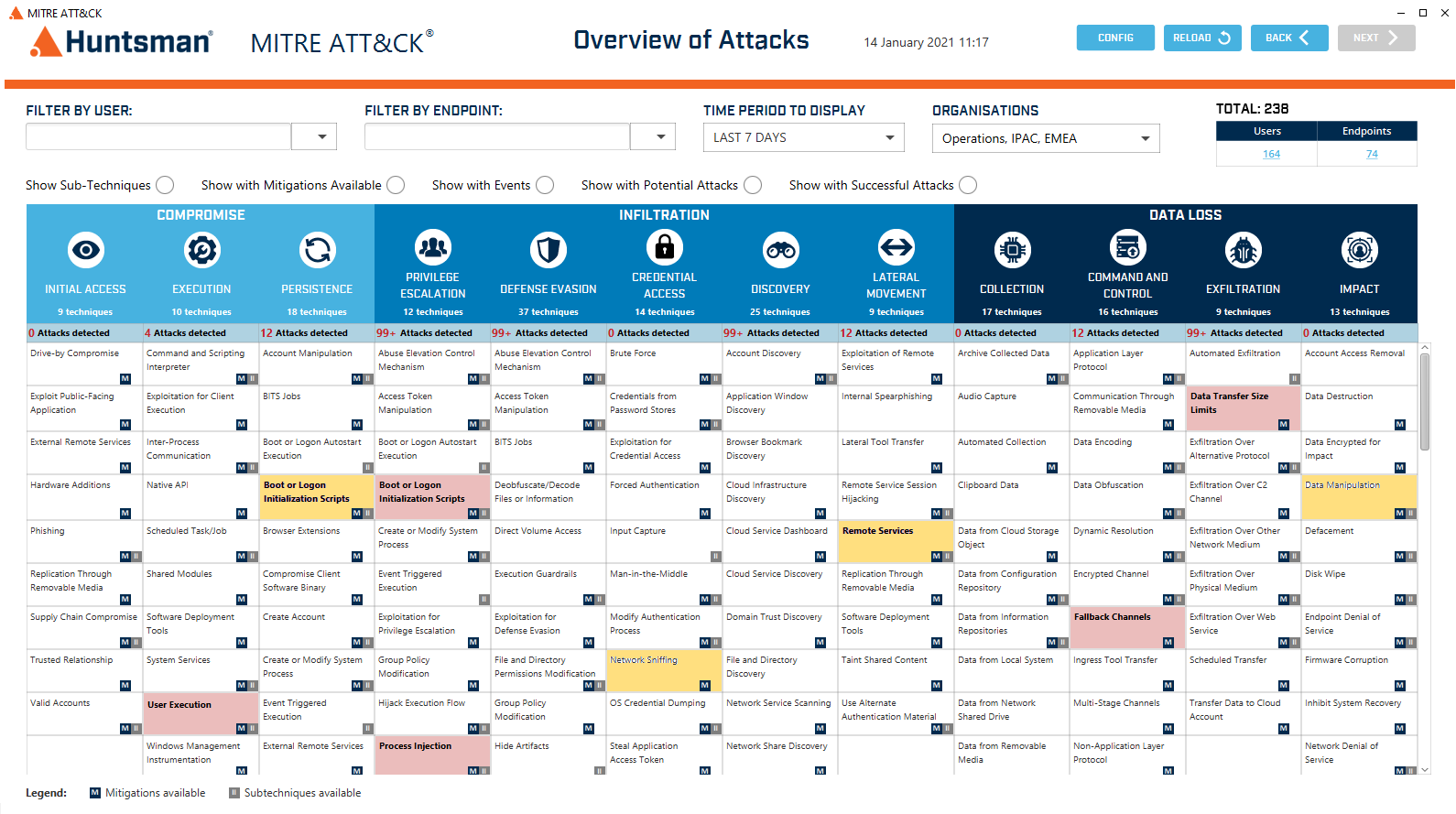
Huntsman Security’s Enterprise SIEM incorporates a new easy-to-use dashboard, for SOC or IT teams to access the MITRE ATT&CK® framework and quickly detect threats and identify and classify their type and severity.
Enterprise SIEM enables the user to specifically match their response and mitigation strategies to today’s leading threat knowledge base.
For organisations investing in broader cyber security risk frameworks, the new SIEM MITRE ATT&CK® threat heatmaps add a dynamic, new security layer to add improved visibility and context to your security management activities.
Detecting a threat and generating an alert is only the start of a complex set of interdependent security operations activities. Huntsman Security’s Enterprise SIEM with its “analyst-centric” workflows, supports the alert triage, investigation and response lifecycle.
Starting with threat verification to automatically gather evidence to enrich alert data and eliminate false positives, Enterprise SIEM allows alerts to be tagged and prioritised to aid triage and classification.
The LiveView interface allows users to pinpoint assets or users at risk, through multiple views of attack information from both the user and endpoint perspective. This simplifies and accelerates critical cyber security decisions and response timeline.
The Huntsman Enterprise SIEM’s incident management interface tracks issues as they are opened, investigated and closed, with full history reporting.
Simple, yet flexible deployment options for on-premise, virtualised and cloud environments support scalable data storage architectures and multi-tenancy for federated enterprises.
Huntsman Security’s Enterprise SIEM natively supports a wide range of data sources and technology platforms and includes a custom API and GUI driven collection tool to simplify data collected from new or otherwise unique data sources.
Flexible, hierarchical data storage enables the available physical, virtual and cloud-based storage to be maximised so there are no limits on the size of the environment, or the volume of data held and queried. For longer term storage and retention purposes, data can be archived to file storage.
For large, federated organisations, multi-level security domains and managed service providers, Huntsman’s Enterprise SIEM can collect data from different domains or organisational units. Its true multi-tenancy means data stores, security policies and security configurations can be easily managed across a range of different monitored networks.

As the sophistication of cyber-attacks continue to increase, threats are inevitable – that’s why our SIEM leverages responsive in-stream processes to streamline workflows and reduce hand-offs, to deliver fast and responsive threat detection and incident response.
Huntsman Security’s Enterprise SIEM analyses and prioritises alerts in real-time, as part of an in-stream process to fast-track investigation, escalation and resolution, to deliver relevant and reliable security information.
Supporting a complete detection, analysis and response process, Enterprise SIEM offers greater levels of efficiency and reliability for your security operations team, reducing the workload on analysts and increasing your ability to quickly identify and manage threats.
Utilising multiple views of attack information by user or endpoint, Enterprise SIEM can quickly locate and tailor an effective defence, improving your SOC team’s responsiveness and effectiveness.
Huntsman Security’s Enterprise SIEM correlates detections and potential attacks against their potential impact. By referencing threat intelligence feeds to inform the system of patterns, indicators of compromise and details of internet addresses that have been implicated, the SIEM systematically analyses the available information.
Coupled with data enrichment, and the facility to gather real-time information from affected hosts or endpoints at the time of the alert, Enterprise SIEM enables an operator to verify the nature of an alert and quickly resolve false alarms, safe in the knowledge that the supporting evidence automatically gathered by the system confirms the benign nature of the event.
This time-saving capability frees up analysts to focus their efforts on real issues, with full visibility of the details of any active threats detected in the environment.
Huntsman’s Enterprise SIEM accelerates the SOC team’s capacity for decision making with streamlined workflows, automated threat verification and data enrichment from alerts or activity logs, to quickly and easily ascertain the true nature of an alert.
It allows the operator to rapidly understand the nature of a potential breach, and to swiftly respond to (i) mitigate the attack to eliminate a potentially damaging situation; or (ii) escalate it, and create a full incident case file for wider investigation.
This doesn’t just save time; it reduces your time at risk. It means the same team can handle more alerts and proactively hunt for threats.
Visualisation of cyber-risk data is integral to the diagnostic process, and the clarity of that information is key to operational dashboard effectiveness and informed security reporting.
Any data set within the system can be easily translated into a report and automatically published to a relevant stakeholder to quickly and easily support your compliance and reporting needs.
Learn the what, how and why of the MITRE ATT&CK® framework and its critical role in mitigation, detection and reporting on cyber security operations.
Download the guide
Huntsman Security’s SIEM sits at the core of your Security Operations Centre (SOC) as a single, comprehensive, yet flexible multi-functional threat monitoring and response platform
LIVE INTERFACE & VISUALISATION
Real-time MITRE ATT&CK® heatmaps and threat summary + GUI driven query interface to optimise investigation and save time
Configurable alert rules and behavioural models, allowing the detection of the widest range of threats – including APTs
Centralised management & coordination of alerting rules, event collection, queries and reports for reliable security governance
Lifecycle visibility of alerts, threats and incident information for all stakeholders
SPEED & PERFORMANCE
Advanced, high speed in-stream event processing, analytics and response decision making – with capacity in excess 100,000 events per second
Behavioural anomaly detection to extend discovery beyond predefined patterns and signatures with machine-learning
Automatic collection and integration of multiple sources of Threat Intelligence, for enrichment, threat verification and orchestration, to speed up resolution of incidents and reduce false positives
Accelerated capacity for cyber security decision making with multiple views of attack information by users or endpoints, to pinpoint an asset/user at risk and quickly tailor a defence
WORKFLOW & SCALABILITY
Simple, yet flexible, deployment options and scalable data storage architecture
Support for virtualisation and cloud/on-premise deployment
Optimised for detection, correlation and reporting OOTB – an extensive range of inbuilt alerts for attacks, technology types and compliance standards
Support for a wide range of data sources and technology platforms (hundreds of technologies supported natively + data stream or source can be configured)
Broad range of pricing and licensing models to suit organisations of all sizes and complexity (inc. Capex and OpEx subscription pricing)
Huntsman Security’s Enterprise SIEM – An ‘always on’ cyber security analytics tool that deploys across your organisation, whether large or small, to provide a complete cyber threat detection, incident management and reporting system.
Our Enterprise SIEM guards the systems holding your sensitive data, IP, processes, contact and financial information, to protect you from unauthorised access, attack and damage.
Read by directors, executives, and security professionals globally, operating in the most complex of security environments.