In December 2018, the US Department of Justice charged Chinese nationals in an extensive global hacking campaign. The hackers, part of Chinese cyber espionage group APT10, allegedly accessed service providers in twelve countries. This is an example of Nation states seeking access to other government’s systems and information by attacking the data supply chain for security weaknesses; by compromising a managed service provider’s (MSP) systems an adversary may be able to pivot to the primary target, although often the MSP holds confidential information, in its own right, that could further the adversary’s goals.
This type of activity is not new; back in March 2017, the Australian Cyber Security Centre (ACSC) learned of a compromise in a construction company that services the Australian government. The malware used in that attack was also attributed to APT10; you can read the investigation report here. APT10 has been around since 2006.
In light of the most recent attack, ACSC released a guidance communication last week, on 11 January 2019, calling for cyber vigilance:
“Following the global compromise of managed service providers or MSPs, the Australian Cyber Security Centre (ACSC) is calling on Australian businesses and individuals to be proactive in implementing better cyber security practices”.
The full communication is available here.
How APTs work
It was the tactics, techniques and procedures (TTP) used in these APT attacks that identified the attacker as Chinese espionage group, APT10. Like many breaches, the adversary starts by sending well-crafted, very specific spear phishing emails to the target, having done relatively sophisticated research on the intended victim.
Using social media, such as LinkedIn and Twitter, they are able to find out a lot about their target before they craft an email. Most people who use LinkedIn say where they work, what team they work in, what their role involves and there is generally enough information about their work history to make social engineering straightforward.
Once APT10 has all this useful information, it’s not hard to create an email that sounds convincing. For example, if the target is a Windows system administrator, by claiming to come from an organisation whose technology the target is an expert in, with some serious information on a security vulnerability or something to do with an up and coming feature release, the administrator will likely believe it, especially if its timely and appears genuine. APT10 also has the resources to make sure this is as believable as possible, ensuring the email doesn’t have the usual grammar and spelling mistakes we’ve come to expect from phishing emails.
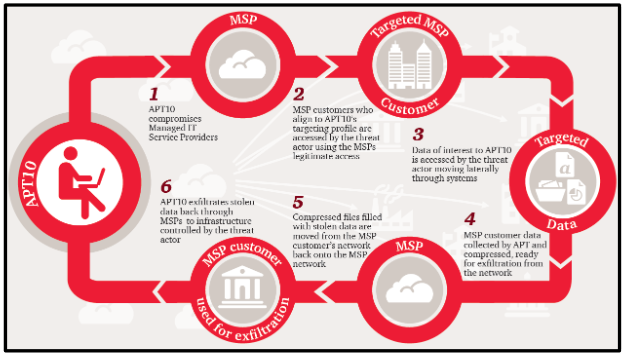
Figure 1 APT10’s targeting methodology (courtesy ACSC)
Once the victim has opened the email attachment, the malware executes and installs a back door for APT10 to use any time in the future. The spear phishing campaign was vast and spanned more than a dozen countries, with as many MSPs and government contractors as possible, being targeted. Once APT10 had accessed the MSP, they did not necessarily pivot to their government target immediately. Rather they’ll establish the beachhead in the MSP network until their organisation has a specific target to aim for.
Figure 1 depicts the methodology[1] APT10 uses to gain access to its intended target via their MSP (courtesy of ACSC1).
APTs Around the World
Over the past decade, there has been a lot of research by security firms on the nature of these advanced persistent threats. FireEye (and previously Mandiant) started with their seminal paper on the activities of APT1 (Unit 61398, Comment Crew), believed to be China’s People’s Liberation Army (PLA) General Staff Department’s (GSD), commonly referred to by its Military Unit Cover Designator (MUCD) as Unit 61398. Yet another military intelligence APT, of the 17 groups listed on FireEye’s website[2], nine of them are specifically attributed to a Chinese origin.
Other nations states such as North Korea, Iran, Russia and Vietnam also feature on that list of active APTs, highlighting the need for organisations to instil a culture of security and take mitigative steps within their businesses to better protects them from this persistent threat of espionage.
APT Mitigation Strategies
As mentioned earlier in this blog post, ACSC has released a communication detailing recommendations on how MSPs and businesses should mitigate against APTs. It’s very important that organisations develop comprehensive security programmes and mitigation strategies that improve their overall resilience to cyber-attacks.
To assist in developing such a programme, it’s a good idea to break it up into manageable stages. We recommend the following steps as a good place to start:
- Establish a risk management culture, where security risks and problems are reported and actively managed by the business;
- Choose between five and ten very specific technical security controls you can focus on implementing, rather than trying to do too much too quickly – the Essential Eight strategies recommended by the ACSC is an excellent baseline;
- Increase protective monitoring and security event logging to give you a fighting chance of detecting threats and investigating incidents;
- Establish an incident response plan and practice responding, looking for issues with people processes and technology so that you can address any shortfalls before dealing with a real incident;
- Roll out a security awareness training and cultural uplift programme to improve your organisation’s overall security preparedness.
The Essential Eight, Monitoring and Compliance
Most mitigation strategies are processes or procedural, but given most attacks target your information systems, you do need to look at how your systems are configured and build a picture (preferably in real time) of what’s going on across your network.
ACSC’s guidelines known as Essential Eight: Strategies to Mitigate Cyber Security Incidents[3] highlights eight key security controls that can be used to mitigate up to 85% of targeted attacks. Without doubt, any organisation implementing all eight of these controls will be better off and more able to defend against cyber-attacks from APT10 or any other attacker referenced on the FireEye website. Yet the Essential Eight does not include logging and monitoring, something we believe should be included in everyone’s cyber security programme to better measure the success of their mitigation controls.

Figure 2 The Necessary Nine – Essential Eight and Protective Monitoring
ACSC’s investigation report1 into APT10’s targeting of an Australian MSP sees “increased logging” as a primary mitigation strategy. The report says, “It is advised that logs be retained for as long as possible; based on the incident timeframe, a minimum of 18 months logging would assist with any future incident investigations.”
By installing competent SIEM technology into your environment, the event logs from every system, network device and application can be sent directly to a central system, and normalised so that sense can be made of it. Logs are often voluminous and contain irrelevant system data that cyber investigators don’t need, so having a toolset that sifts through it for relevant events and applies logic and rules to highlight potential issues pays big dividends to your security posture.
Cyber KPI’s and measuring the effectiveness of Security Controls
To further assist both your organisation’s risk owners and operational security team, it is critical that they understand their exposure at any one point in time. Having a Security Scorecard that monitors the efficacy of your security controls and delivers continuous detailed reporting against the mitigation strategies allows risk owners to make quick, informed decisions based on the nature of the risk. It also serves to let security teams see when patching hasn’t been applied or a problem has occurred with a backup, enabling a rapid response.
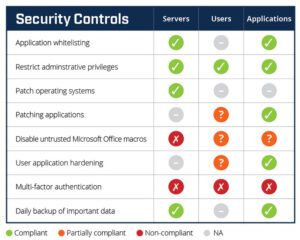
Figure 3 Huntsman Security Scorecard – monitoring Security Control effectiveness
Maintaining a Secure Baseline
Ongoing maintenance of your security controls and the overall security culture of your organisation requires a systematic compliance regime that continues to monitor compliance with the security controls and solutions you use. You should establish regular testing of your environment, such as your gateways to customer systems or your records management systems, to ensure you are meeting your own internal security objectives to protect your key information assets.
Having your security team manage compliance on an ongoing basis is the best way of maintaining a security baseline, as you don’t have to wait until the end of the year to find out from your test team that all your servers are missing patches. Rather, that end of year test should be finding things you would not typically know about, such as a deep configuration issues on the network, or finding a zero-day vulnerability in your database server.
Find out how to defend against APTs
If you’d like to find out more on how to establish a protective monitoring regime and ongoing security compliance capability contact the Huntsman Security team.
[1] ACSC’s Investigation report: Compromise of an Australian company via their Managed Service Provider
[2] APT Groups: Who’s who of cyber threat actors https://www.fireeye.com/current-threats/apt-groups.html
[3] https://www.acsc.gov.au/publications/protect/Essential_Eight_Explained.pdf
 About Huntsman
About Huntsman





