Various factors are converging to influence the need for better management of cyber security risk. Whether it’s to understand the effectiveness of security controls, isolate any weaknesses or to simply acknowledge cyber security as a corporate governance issue; the requirement for greater visibility of an organisation’s cyber security posture is a given.
Whilst the need for cyber risk measurement is widely acknowledged, delivery of reliable metrics is an ongoing challenge. Better cyber risk management requires better tools, tools that measure risk, discern change, identify gaps and map trends in a timely manner.
Improving your security defences
Security teams are rightly focused on defending their enterprise against attack. Using sophisticated threat detection and SIEM solutions SOC teams seek to isolate the threats likely to impact their businesses. Their defensive efforts are demanding and ongoing but ultimately, they lack some vital risk information that would massively assist their investigation and response efforts. Just imagine knowing where the gaps in your organisation’s security defences lie; and how it would assist SOC teams in improving risk management outcomes and raising the effectiveness of security controls.
Organisations should be asking some important questions: Are our risk mitigation efforts operational; and if so, how effective are they? Can we measure any gaps in their effectiveness to better manage our response efforts? By identifying these “uncontrolled” risks organisations can mitigate them and improve their security posture.
This sort of performance data can only come from within the organisation itself; where the state of cyber security controls can be dynamically measured and residual risks that might pose a threat to the enterprise determined. To be effective, security controls demand continuous, concise and systematic risk information.
Improving ineffective security controls
New technologies are now emerging that provide security stakeholders with real-time visibility of the effectiveness of their organisation’s security controls. This enables CISOs and risk executives to prioritise any remaining residual risks and quickly implement management strategies to contain or remediate them.
In order to measure risk effectively it’s important that even the smallest change can be quantified and a risk management response initiated. In cyber security a risk can change and quickly escalate to something that can threaten the business; that is why reliable, automated measurement processes are important. Adopting a systematic procedure across a standard cyber security framework is a good way to maintain the objective and repeatable assessment of security controls. There are a number of these frameworks in use around the world, many with significant similarities; ACSC Essential 8 (Australia), NCSC Top 10 (UK) and NIST (USA).
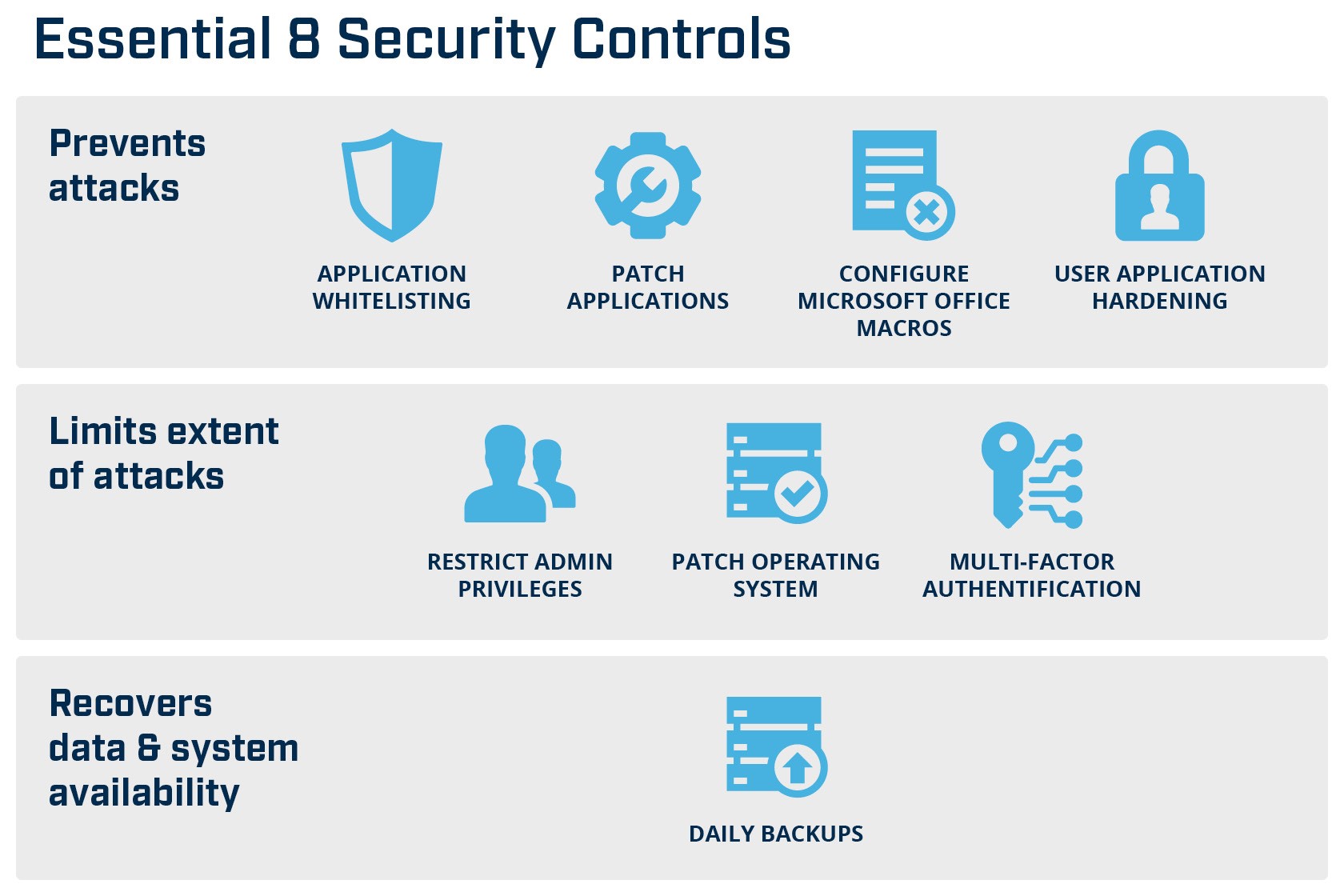
Australia’s ACSC Essential 8 Framework incorporates the eight most fundamental mitigation strategies. It is simple, measurable and has been found to mitigate 85% of targeted attacks. The framework embraces security controls for attack prevention, limitation of spread and data recovery and system availability.
Introducing Huntsman Security’s Tools for cyber risk measurement
Huntsman Security has released two cyber risk management tools, both designed to automatically measure each of the Essential 8 security controls effectiveness and provide reliable performance metrics.
Essential 8 Auditor
The Essential 8 Auditor executes a cyber risk audit and delivers an immediate view of an organisation’s security controls’ effectiveness. The Auditor confirms the presence of each control and determines the maturity level of those controls across the enterprise. The product can be used for internal cyber risk measurement, annual cyber risk attestations and as a benchmarking and performance management tool for security consultants, auditors and risk & compliance managers.
Essential 8 Scorecard
The Essential 8 Scorecard is broader in its capabilities. It provides the continuous audit and scoring of each of the Essential 8 controls; alerting immediately when any pre-set compliance levels are breached. The Scorecard includes a live dashboard for real-time diagnostics and response and automatically generates and distributes senior executive reports.
The Essential 8 Scorecard supports operations teams by identifying and providing information to mitigate ineffective controls so that SOC teams can better manage their pro-active and defensive security effort. Specialised operations and senior management focused reports provide performance trends for prioritising effort where and when it is needed most.
Improve your security controls and enhance your security posture
These new cyber risk management tools provide key risk information for operational and senior executive stakeholders to:
- Continuously monitor and manage their cyber risk performance over time
- Mitigate any risk that has come through a gap in the controls
- Report performance against a recognised security compliance framework
- Highlight the organisational cyber posture for all stakeholders
Whether you are looking to simply baseline the effectiveness of an organisation’s security controls or you want a tool to continuously measure and dynamically manage cyber risk, Huntsman Security’s Essential 8 products provide automated cyber risk measurement capabilities to assist risk management efforts and ultimately improve cyber resilience.
For more information about measuring the effectiveness of your cyber security controls please contact Huntsman Security.
 About Huntsman
About Huntsman



