In the UK, the National Cyber Security Centre (NCSC) runs an information assurance scheme called Cyber Essentials. Our blog post series looks at each of the framework’s five focus areas and offers practical hints and tips on security requirements and value to organisations wishing to follow its advice.
This is the second post in our series, you can read the first introductory one here. In this post we’ll look at Cyber Essentials ‘Secure Your Internet connection’ requirement and explain what it means plus give some pointers to consider when trying to secure your organisation’s gateway to the Internet to ensure threats stay on the outside of your firewall.
Secure the perimeter with a firewall
It may seem obvious to most people but using a firewall between your internal network and the Internet is one of the simplest yet most effective ways of protecting your organisation from hackers. Essentially, firewalls create a control point between your internal network and other networks (such as the Internet or even a partner or supplier’s network) where you can apply rules to prohibit certain behaviours, block malicious sites and control the flow of traffic.
The most common working example applies to almost every modern organisation, where the business requires a connection from the internal network to the Internet to allow its workers to send emails, visit websites and access cloud-based services such as those provided by Salesforce and Microsoft. The firewall acts as the gate and the gatekeeper, screening network traffic in both directions for signs of trouble, either allowing or blocking content based on rules. Organisations should consider the firewall their primary security control, even over antivirus software, since they reduce the likelihood of hackers gaining access to the internal network and stealing sensitive information. Without the firewall, the internal network would be wide open to anyone on the Internet who wanted to come and snoop around and start trying to hack each of the business’s computer systems (workstations, laptops, servers and storage systems).
Select a firewall to suit your business
Firewalls come in several flavours, so it pays to learn a little about these devices and pick the right configuration for your needs. Most user devices – laptops and workstations, whether they run Windows, macOS or Linux – have personal (host-based) firewalls built into them. On Windows, for example, the Windows Defender Firewall can help protect devices when they are away from the company network, with the ability to tighten up the security on the device when users are in public spaces, like airports, hotels and coffee shops. If the organisation runs a private network (also known as a Local Area Network or LAN), it needs a dedicated perimeter firewall, which sits between the internal network and the Internet (or any other external network).
Some Internet routers double as firewall devices, especially when you look at the consumer end of the market. These consumer devices are decent for home networks and small business set-ups, but you should check first with your Internet Service Provider (ISP) to see if they recommend a specific model since they may provide dedicated support for certain devices, thus giving you a support channel should there be a problem.
One caution though is that many of these consumer Internet routers don’t have the fine-grained controls you might want to lock down what the LAN can talk to on the Internet. Dedicated firewall products, that also have Internet interfaces, are better options for businesses. They are a little more expensive, however, the added value obtained from this kind of device is that it layers in the functionality that larger organisations use to protect their networks, at a fraction of the cost.
Segment your network to improve GRC
In addition to keeping out the hackers and preventing attacks, businesses use firewalls to segment their network, generally based on risk. Critical or highly sensitive data, for example, could be put on a separate network, with access granted only to a few key members of the executive team. Risk management is a critical factor in network architecture, so the business should consider which information assets need protecting the most and move them onto a protected network. Information such as personal staff and customer records, credit card data, trade secrets, contracts and banking information, financial statements and intellectual property are valuable, making them all a target for hackers.
Improve your cyber security compliance
Most modern businesses have compliance requirements, for example GDPR and PCI-DSS. If you are a UK public sector supplier you can add Cyber Essentials to your list of obligations.
Proving you are secure to an auditor is not an easy task since they need to see evidence that you have managed your security over the period leading up to the audit. Security devices produce millions of events that can tell administrators what’s been going on, yet many organisations don’t use these to their full potential since useful alerts can get lost in the enormous workload and volume of information to be reviewed.
Many business firewalls produce events from all their security functions, such as the intrusion protection system, VPN and antivirus capabilities, adding them to a logging database to provide a complete bank of information to determine your security posture.
Huntsman Security’s Cyber Essentials solution automates the job of sifting through all the firewall log data and presents the security status, along with the other four Cyber Essentials security controls, in a single pane of glass dashboard that works both at the management level as well as the IT level.
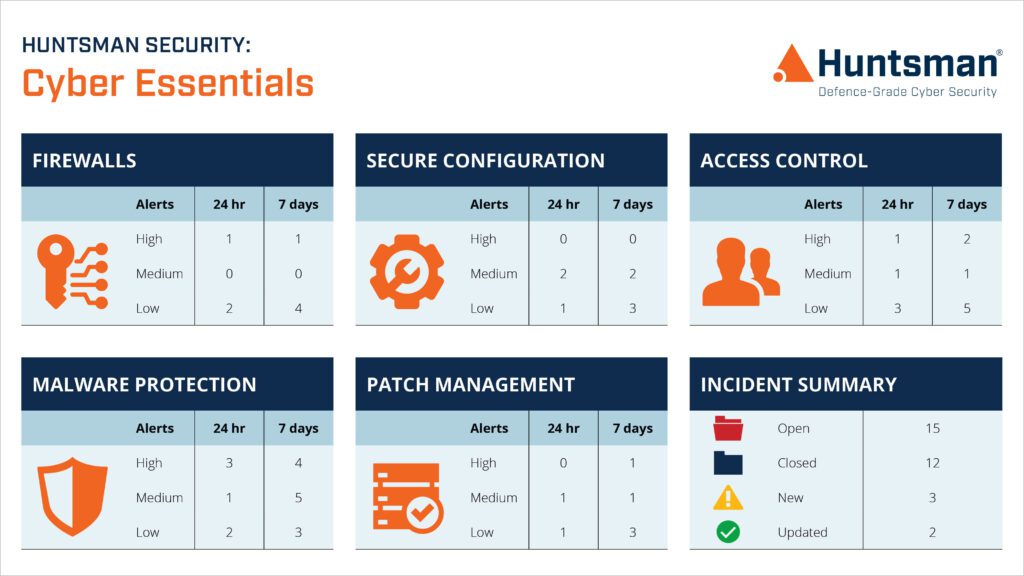
Huntsman Security’s Cyber Essentials summary dashboard
Firewalls play an essential part in your organisation’s security defences, so don’t underestimate their value to the overall security posture of your business.
Next steps towards Cyber Essentials compliance
In this post we’ve looked at the Cyber Essentials requirement to secure your Internet connection, explaining what firewalls are and how they can be used to protect your business.
In future posts will will look at the remaining four baseline technical controls and explain how each one can play a vital role in determining an organisation’s security posture.
 About Huntsman
About Huntsman



