Boards are quickly realising they must invest in cyber security to keep their businesses safe from adversaries, which is leading to a burgeoning industry with consistent year-on-year growth. While steady growth is excellent news for consultants, managed security service providers (MSSPs), vendors and security professionals, board executives must remain focused on achieving a calculable return on this security investment, rather than falling for the hype in industry messaging.
Cyber security improvements require more than just solution purchases, and boards must ensure that the overall calculable benefit of the solution exceeds the total cost of ownership of cyber investment. Business cases of this type can often be problematic. There are, however, other ways of keeping the business safe, without constantly spending on the latest next gen intrusion prevention system or firewall. Leaders need to evaluate how well their incident handling procedures work and how cost effective is their compliance monitoring approach.
Let’s explore this balancing act and look at how security teams can drive spending across the cyber landscape, while seeking solutions that boost their ability to remain vigilant and deal with incidents in the event they occur.
Technology Led
Security operations teams love technology. As an inquisitive and highly demanding engineering discipline, security analysts are the first to admit they often spend free time coding, playing with hardware and learning open-source security tools, to see what they can do. If teams were allowed to build security capability with unlimited budget, the operations centre would have all the latest tools and gadgets coupled together in the most complex manner imaginable. This risks having technology as the focal point of the business case.
The problem is, while the claims of new technologies are ambitious, the use cases are often narrower and directed to mitigate specific technical attacks, with limited capability outside of that scope. With an investment strategy focused predominantly on technology, organisations can see their security spend increase yet with only limited improvement in their overall security posture. For this reason, we recommend a conservative approach to security planning, considering the disciplines of operations, business risk, security management and corporate compliance, in an effort to ensure controls and processes are cost effective.
Compliance Led
Compliance, in its simplest form, is the process of aligning business activities with a set of predefined policies or guidelines to ensure the organisation meets these anticipated outcomes. Compliance is typically measured by way of an assessment or external audit and results are frequently elevated to board level. In particular, where the compliance regime is driven by laws and regulations. Failure to remain compliant can have serious ramifications for the business and its officers, whereby penalties or even revocation of a licence to operate can occur.
Within cybersecurity, the maintenance of a compliance system is often incorporated into an information security management system (ISMS) or policy framework and mandates that certain security controls are used to manage specific security risks. Compliance requirements are drawn from industry specific guidelines or standards, and in some cases multiple standards, where overlapping controls may apply. For example, a company operating in the finance sector may be required to align to the Payment Card Industry Data Security Standard (PCI-DSS), while in Australia the same company may also be regulated by APRA, in the UK by the FCA, or in the US by FR/FDIC/FTC. Financial regulators have their own sets of security control requirements to which their members need to adhere and be assessed. Many of the control requirements specified in PCI-DSS crossover with these other requirements, so organisations must understand these control mappings and reporting to ensure gaps are quickly detected and remediated.
Who Manages Compliance?
Compliance is a business governance issue and certainly bigger than cyber or even information security. Being under the corporate governance umbrella, the cyber security team is responsible for keeping the compliance management team informed of misalignment issues or implementation problems. It is important that the compliance function has the means to assess the ongoing ability of the organisation’s adherence to the standards and requirements, and initiate remedial action when something goes wrong.
Continual Monitoring
Operational monitoring, as per the normal business case for a SOC, focuses on detecting attacks or anomalous behaviour that may be indicative of a breach. This kind of protective monitoring is a vital component of any security plan but doesn’t address the issue of deviation from the organisation’s compliance baseline. The key to success in any compliance approach is to detect issues with control implementation or operation before they turn into a problem. For example, New South Wales government agencies must report on their maturity assessment against the Australian Cyber Security Centre’s Essential Eight, so detecting a control problem can circumvent a larger breach issue.
One of the controls in the Essential Eight, for example, is that the business needs to use Application Whitelisting to protect its computer systems from unauthorised applications. To achieve this the cyber security or IT team might enable Microsoft AppLocker to meet this requirement and report to the compliance team that it’s active. Over time, however, as updates are applied and systems administrators make technical changes across the environment, how can the compliance team know if the technical compliance based on AppLocker still meets their needs? The short answer is, they can’t.
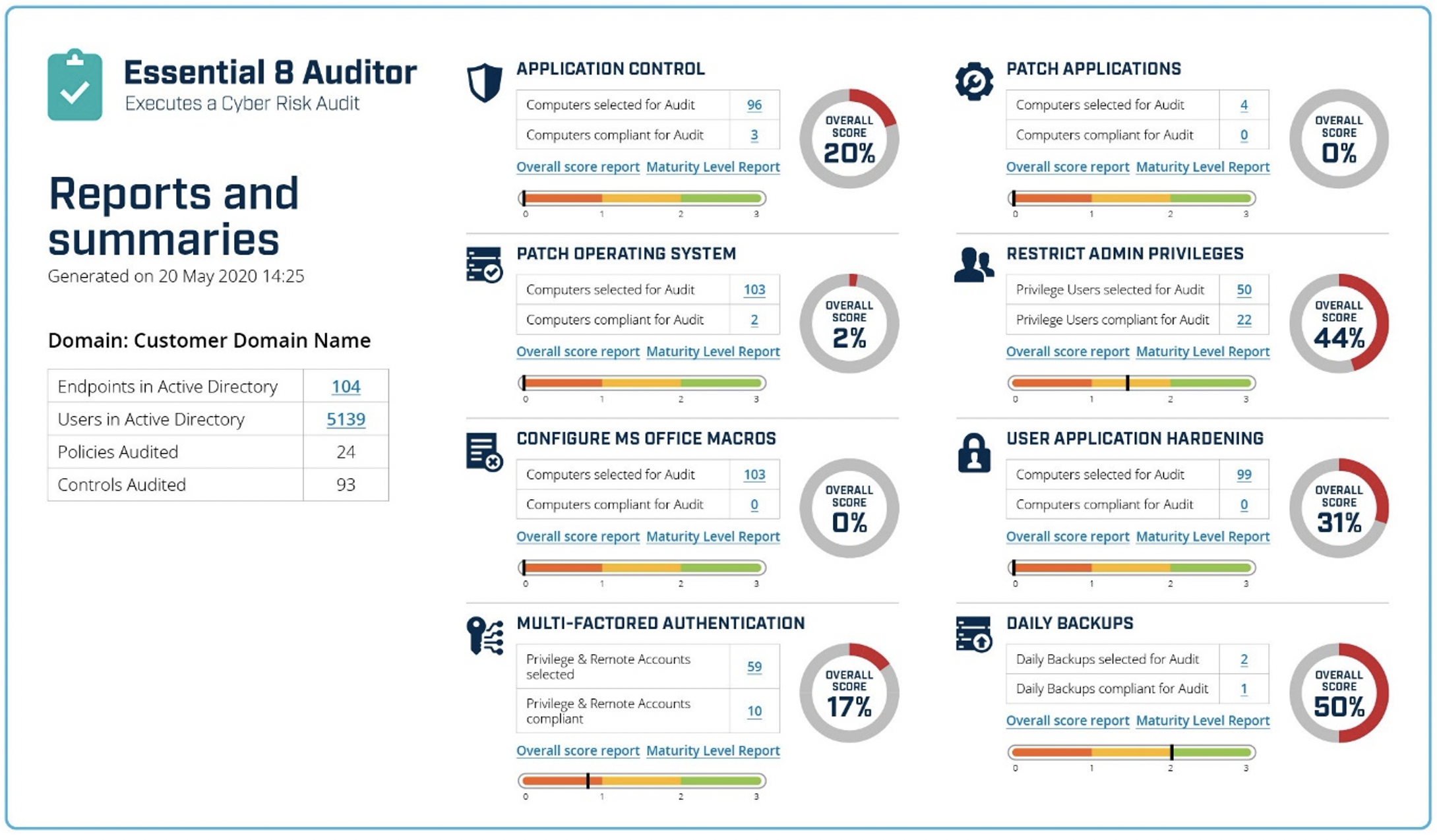
This is where tools, such Huntsman Security’s Essential 8 Auditor come into their own. The Essential 8 Auditor works by providing the compliance team with an immediate view of the status of their security control effectiveness against the framework. It collects the settings and implementation details of each control, such as Application Control, and presents this assessment along with any related configuration information back through dashboards (for example as shown in Figure 1).
Figure 1 – Essential 8 Auditor Reports on Control Implementations
Once the compliance team sees the true nature of their cyber security control performance they can begin an investigation to understand the gap and begin to uplift the efficacy to a better level. Since this report provides a snapshot of how well compliance is tracking, management teams can run these assessments periodically to see trends or quickly detect issues for remediation before an external audit happens.
More mature teams want to see compliance issues as soon as they occur rather than waiting for a report to run, which is why we also created the Essential 8 Scorecard. The Scorecard uses a continuous monitoring approach to provide a real time view of implementation details of each cyber security control, with the details gathered directly from production systems. Figure 2 shows the equivalent dashboard for the compliance team, with a series of trendlines over time against each of the monitored controls.
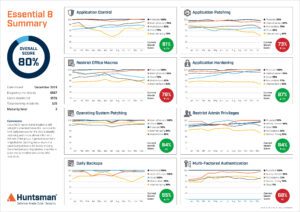
Figure 2 – Essential 8 Scorecard Summary for Compliance Team
Continuous monitoring is a vital component of maintaining an organisation’s compliance status and visibility and is hard to achieve without the use of technology that reports insights in a way that is clear for all levels of management.
If you want more information on how Huntsman Security can help you maintain and report compliance levels of your security controls directly to your engineering, and even management, teams, contact our experts today.
 About Huntsman
About Huntsman