Auditing is the mainstay of business governance, since every organisation, no matter the size, is required to undertake at least one review of some aspect of their operations each year. Explore ways to hasten the IT risk auditing process and quickly uncover non-compliance with continuous, adaptive risk and trust assessments.
Anyone who is involved in information security or cyber matters will know that auditing is a core component of any effective security programme, since assurance is the cornerstone of remaining secure as the world around us changes. Businesses are seeking systems that can hasten the auditing process and quickly uncover non-compliance, since these gaps are often exploitable vulnerabilities. Adding to the requirement, security executives don’t want to wait 12 months until the next audit since they understand that vulnerabilities are discovered every day, so an entire year of being exposed to serious threats is an untenable position.
By introducing a technology solution that comprehensively assesses security posture and provides continuous feedback on compliance deviations against the desired states, the business minimises human error while mitigating potential risks of interference.
In the United States, recent changes in the Public Company Accounting Oversight Board (PCAOB) rules now require auditors to report not just on the level of assurance in controls, but also on the availability and timeliness of evidence and the amount of human interaction between the systems and the audit function. Additionally, the PCAOB mentions the importance of appropriateness, stating:
“Appropriateness is the measure of the quality of audit evidence, i.e., its relevance and reliability. To be appropriate, audit evidence must be both relevant and reliable in providing support for the conclusions on which the auditor’s opinion is based.”
From a security point of view, appropriateness is critical and something every security manager or IT executive should be assessing and trying to remove any of the human friction between the control itself and the result of the assessment.
The more accurate measurement of control compliance the business gets the better. Also, the speed at which deviations are alerted to the appropriate team is vital since not knowing that a control has failed for many weeks or months could be catastrophic. Insider threats are also a problem that security managers are paying more attention to, and malicious insiders interfering with the results of audits is a major risk. If non-compliance is concealed, then the business could be exposed to or even undergo a major cyber incident without any of the normal indicators of attack.
Build an adaptive security posture with CARTA and Zero Trust
A relatively new approach, pioneered by Gartner Research, is continuous adaptive risk and trust assessment (CARTA[1]). CARTA is gaining traction as a strategic approach to risk management and extends to all aspects of IT and service management. By adopting CARTA, businesses assume all their systems and devices are potentially compromised, so everything needs to be assessed against a baseline of what the appropriate security target should be. Forrester Research has also aligned its thinking with this model with its Zero Trust[2] model, which again assumes that nothing in the environment is trustworthy and hence everything needs to be considered hostile when its place is considered within the IT environment. If you consider this from a security architecture perspective (see Figure 1), the auditing controls you build around any individual system will be very different if it’s considered a threat as opposed to being considered friendly.
Both approaches promote continual assessment and change the way we consider information risk and our defensive security countermeasures. The underlying requirement is that the business can continually monitor and react to change in state that indicates a threat.
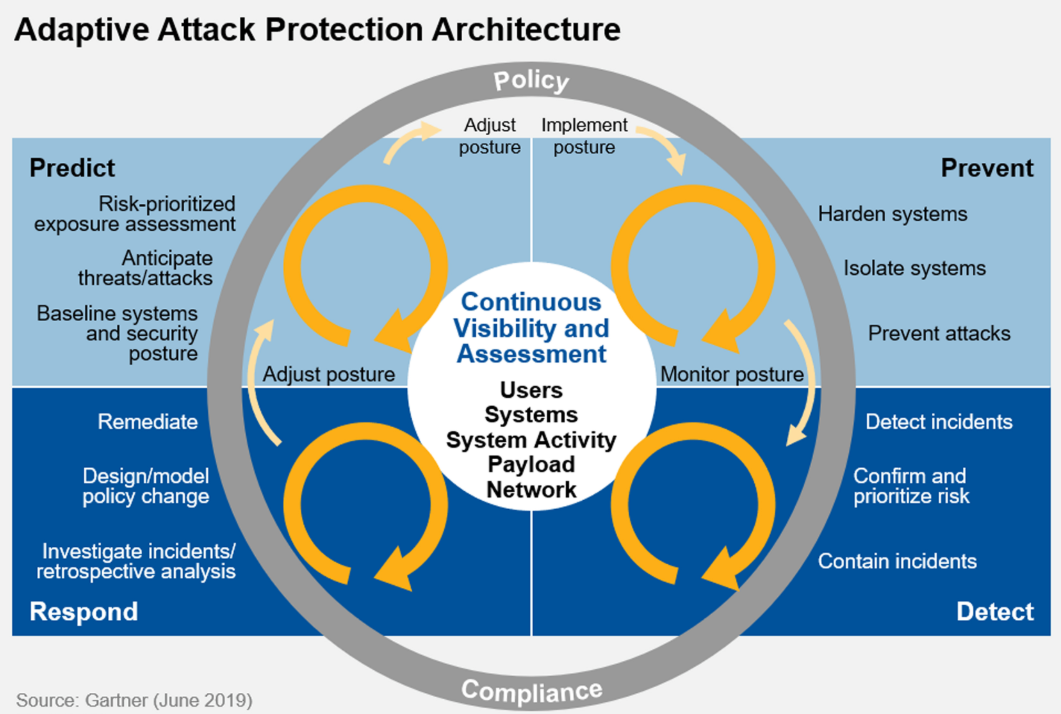
Figure 1 Gartner’s CARTA model promotes continual assessment of risks across the business
By taking a strategic approach to security control monitoring we are constantly checking if the controls we rely on to protect the business are working as they should. Since the security threat environment changes every day as new vulnerabilities are found, systems are upgraded or new services are introduced, the control compliance can also change. Continuous assessment allows security managers to make better decisions and reprioritise workplans so that any issues relating to critical controls can be quickly remediated.
To most security managers and IT operations managers, the cycle of threat detection and response is well known, but CARTA’s value comes from tying the work of the SOC back to the business risk management approach and ensuring the controls we rely on are doing their job. Without that, the SOC may not detect the threat in the first place, and their job becomes impossible.
Implementing CARTA
Any technology systems that produce logs (and most do) can report its status. In fact, if you wanted to manually adopt CARTA, then you’d been looking at the logs from hundreds, or even thousands, of log sources all day every day. In a security operations world, we have already addressed this issue with our Security Information and Event Management (SIEM) platform. However, requirements from our own customers’ senior management and audit and risk teams has led us to develop solutions that provide the perfect implementation of continuous adaptive risk and trust assessments.
Essential 8 Scorecard & Essential 8 Auditor
Huntsman Security’s Essential 8 Scorecard allows your organisation to continuously measure control performance, something that is a core requirement of CARTA. Security managers get an objective, quantitative measure of the organisation’s cyber posture that highlights and alerts on any gaps in defence strategies. Additionally, executive reports are distributed automatically enabling informed risk decision making at every level of the business, all the way up to the executive. Alternatively, you can utilise the Essential 8 Auditor for a one-0ff, immediate view of an organisation’s security control effectiveness.
Essential 8 Framework
The Essential 8 Framework, developed by Australian Government, has been found to mitigate 85% of targeted cyber-attacks. The eight core controls are globally recognised as fundamental to robust cyber hygiene.
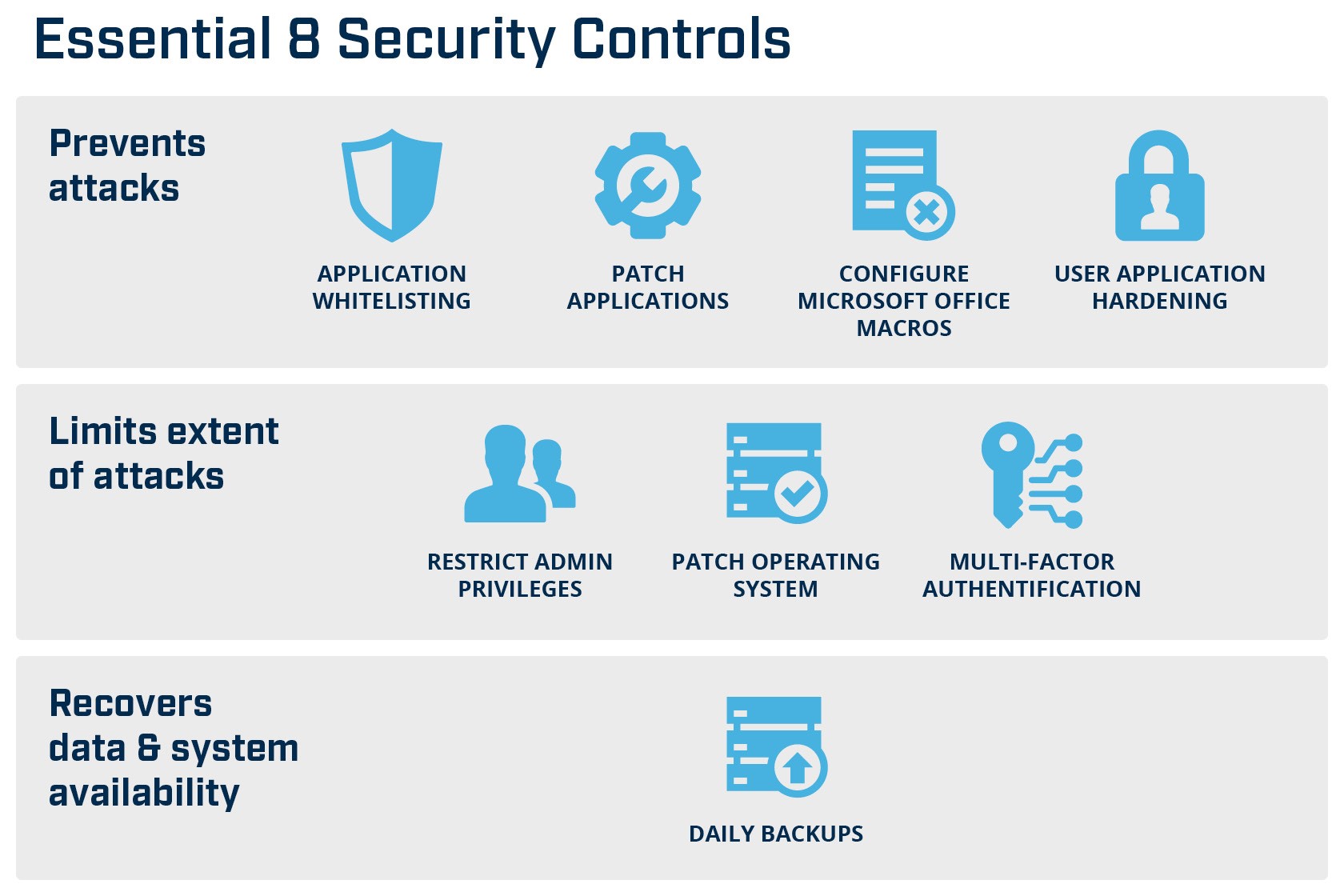
Essential 8 Framework – critical controls to protect your organisation
By introducing continuous adaptive risk and trust assessments across your risk environment, you gain visibility immediately. No more second guessing and no more nasty surprises when the audit cycle comes round. Do you have a current measure of your organisation’s cyber hygiene? Find out more here.
[1] CARTA is discussed here.
[2] Zero Trust is explained well in this article.
 About Huntsman
About Huntsman




