The Office of the Australian Information Commissioner (OAIC) – Australia’s statutory agency for privacy and freedom of information – has released its third quarterly report on Australia’s Notifiable Data Breach scheme. It shows 245 reported data breaches between July and September, a number which correlate closely with the previous quarter.
Australian Data Breaches: Has Reporting Stabilised?
Malicious or criminal attacks remains the highest category of data breaches this quarter. Between 1 April and 30 June, 59% of data breaches were attributed to malicious or criminal attacks, while this latest report shows it dropping to 57%, yet remaining significantly ahead of the other two categories of human error and system faults. Figure 1 and Figure 2 show the similarities between the two reports.
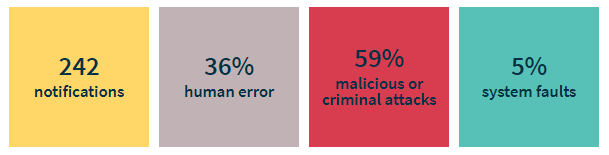
Figure 1 OAIC notifications between 1 April and 30 June
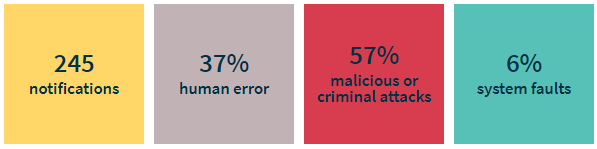
Figure 2 OAIC notifications between 1 July and 30 September
You might conclude, based on this quarter’s report and last quarter’s report, that the rhythm and frequency of cyberattacks in Australia is somewhat constant. In fact, comparing these two reports shows patterns of similarity across the other two categories of human error and system faults as well. Does this mean we can expect the same kind of patterns to continue in the future?
The reality is, at this higher level, it’s much too early to tell. However, even within the detail of the report there are a lot of similarities, so it’s certainly something to watch as further reports are released throughout 2019.
Phishing Remains Australia’s Biggest Cyber Threat
Data breaches relating to malicious or criminal activity totalled 139, and 96 of those were classified as cyber security incidents. Clearly the biggest threat to Australian organisations still relates to employees opening malicious attachments or clicking malicious links in phishing emails.
A significant percentage of incidents saw attackers exploit unpatched vulnerabilities, followed by incidents involving other kinds of malware, ransomware, and, “hacking by other means.” Interestingly, “theft of paperwork or storage devices was the second most reported source of malicious or criminal attacks (12 per cent).”
This tells us two key things:
- While cyber security controls may be established in organisations, they may not be operating at an optimum level; a process of continuous monitoring and review is vital to maintaining cyber resilience;
- Physical security is as important as ever in managing your organisation’s defensive strategy.
Australian’s Top Five Industries Under Cyber Attack
Health service providers, as shown in Figure 3, was the top industry sector reporting notifiable data breaches during this quarter. As you can see, across each of these sectors, it’s a close match between human error and malicious or criminal attack, while system errors account for much less. This graph (Figure 3) demonstrates threats from ignorance or data handing mistakes are as likely to cause organisations harm as cyberattacks, so security teams shouldn’t underestimate the importance of security awareness education and the introduction of robust security processes to better protect important or sensitive data.
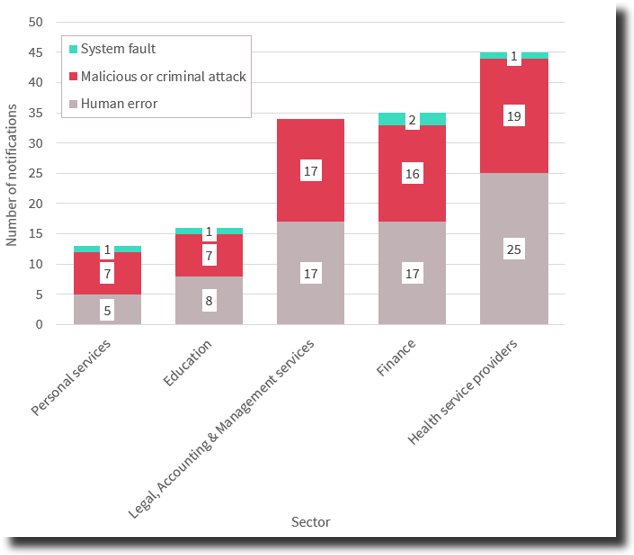
Figure 3 Source of data breaches — Top 5 industry sectors
Digging a little deeper into malicious or criminal attack breaches, in the health service providers sector, there were more thefts of paperwork or data storage devices than there were cyber incidents. Health service providers still rely heavily on paper-based forms in clinics and hospitals, so physical theft of paperwork and devices is not surprising.
If you compare this to the finance and legal, accounting and management services sectors, considerably less breaches were attributable to theft of paperwork or storage devices, rather most breaches were cyber incidents. Both industry sectors (finance, and legal, accounting and management) have moved much more quickly to online operations, with much of our conveyancing, banking and accountancy all being done online.
Interestingly, social engineering accounted for a few (just three) incidents across finance and health sectors, while social engineering was entirely missing from the legal, accounting and management services sector report. This could be due to the more process-oriented approach lawyers and accountants take to their work, or it may be nothing more than a coincidence, but it’s certainly something to watch in future reports to see if it stacks up as a hypothesis.
Cyber Incidents – external contacts equal more risk
Most cyber incidents reported this quarter relate to phishing, with compromised or stolen credentials coming in overall second place. Interestingly, the education sector is the only industry where this was revered, with three breaches relating to compromised or stolen credentials, and only two successful phishing attacks.
In the legal, accounting and management services sector, there were no ransomware attacks reported at all, compared to nine successful phishing attacks. This could indicate a predilection of susceptibility to social engineering for professionals in this industry or may simply be because lawyers and accountants frequently communicate with clients outside their organisation, so they interact more with people they cannot identify as trusted.
Take steps to defend your organisation’s assets
OAIC’s latest breach report clearly shows that the biggest threat to Australian organisations is that of malicious or criminal attack. Most of these attacks relate to cyber incidents, with phishing still being the prevalent means of attack. This illustrates that human fallibility and social engineering susceptibility remains the most significant vulnerability organisations face – and human weakness is not something we can easily patch. We need to find better ways to educate our staff, while boosting our capability in detecting and alerting on behaviours that leave our data exposed to cyber risk.
Make sure your organisation is using security enforcing technologies that assist in preserving the confidentiality, integrity and availability of your information assets, while developing a comprehensive audit trail to allow you to investigate and determine the extent of harm when an attack does happen.
Read previous blogs on OAIC Notifiable Data Breach Reports here and here
 About Huntsman
About Huntsman




