The Office of the Australian Information Commissioner’s fourth quarterly report shows an increase in the percentage of attacks attributed to malicious or criminal activity, as well as a continuing trend of growth in the overall number of attacks.
“Preventing data breaches and improving cyber security must be a primary concern for any organisation entrusted with people’s personal information.”
Angelene Falk, Australian Information Commissioner and Privacy Commissioner
Australian Data Breaches are Increasing
OAIC started publishing its quarterly data breach summary in early 2018, providing insight into the number and nature of cyber incidents reported throughout the preceding three months. The fourth summary report was released on the 7th February 2019, and covers the months of October, November and December 2018.
This latest instalment of the breach report completes OAIC’s first year of reporting and shows consistent growth in the number of incidents reported, as well as some interesting observations across different industries.
Following the same trendline as the previous reports, the leading cause of notifiable data breaches in the December quarter was malicious and/or criminal attack, with a total of 168 notifications. From the total number of notifiable breaches (262), 85 of them were attributed to human error, while just nine reports suggest system error was the root cause.
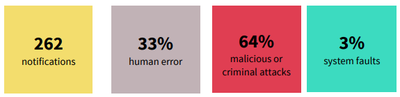
Figure 1 OAIC notifications between 1 October and 31 December 2018
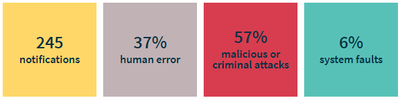
Figure 2 OAIC notifications between 1 July and 30 September 2018
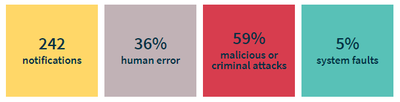
Figure 3 OAIC notifications between 1 April and 30 June 2018
Most data breaches resulted from compromised credentials (usernames and passwords). Of these, an expectedly high percentage were directly attributed to phishing attacks (43%), with a further 24% caused by compromised credentials through some other means.
In total, 67% of all attacks focused on credential theft, hence the Australian Information Commissioner and Privacy Commissioner’s comment that organisations need to secure their personal information better by improving the way they safeguard credentials. The Commissioner, Angelene Falk, followed on to say, “Employees need to be made aware of the common tricks used by cyber criminals to steal usernames and passwords[1].”
Industry Specific Cyber Security Challenges
The second similarity to the previous quarter’s report is that health service providers continued to top organisations reporting data breaches (21%). This was followed by the finance sector with 15% of the total number of breaches, followed again by legal, accounting and management services (9%), private education (8%), and then mining and manufacturing (5%).
This ranking reflects the same ordering as with previous quarter reports, thus it appears to be a pattern that is truly reflective of the effort threat actors are putting into attacking those sectors.
Malicious or criminal activity is an issue for the finance sector

Australia’s finance sector: 70% of breaches caused by malicious or criminal attacks
One interesting consequence of gathering these sorts of statistics is organisations can use them to help inform their security plans and development programmes. Take for example, the healthcare sector. 54% of healthcare data breaches resulted from human error.
This is contrasted with reports from the finance sector, where 70% of breaches were caused by malicious or criminal attacks. The healthcare industry needs to focus on security awareness and making people more accountable for protecting credentials, while the finance sector needs better security controls in place to prevent malicious activity.
The objectives of criminals may not be changing – they still want personal data that can be onward sold for the purposes of identity fraud – but the risks the healthcare sector is facing that relate to something it can completely control (employee behaviour) are greater, so a concerted campaign of security awareness seems in order.
Once you get into the finance and legal sectors, however, things are different. They are usually very good at following protocols and have good security measures in place to ensure insiders don’t make mistakes – multifactor authentication, separation of duties, compartmented networks, and delegation of administrative rights to those they trust. Therefore, these sectors need to focus on their technical security countermeasures and find ways to detect and respond better to attacks when they occur.
Detecting Attacks in the Sea of Data
Finance organisations, along with legal and insurance organisations and mining organisations have much to lose when a successful attack occurs. They often hold critical personal information relating to their customers, as well as direct access to their financial assets.
The mining sector may hold commercially sensitive contracts or prospecting reports that nation states outside of Australia would find invaluable. So, it’s vital that security programmes take this OAIC report into consideration and focus on detecting and responding to cyber attacks, especially those resulting from credential compromise.
The problem most organisations face is that the volume of data their security systems produce can be enormous. Literally billions of security events are generated every day by network systems, operating systems and applications, so sifting through all that data is a Herculean task. Technology systems that can analyse this data and determine what might constitute an attack are vital.
The value of Security Incident and Event Management systems
A Security Information and Event Management (SIEM) system is the best way an organisation can process all this data, since it’s purpose to ingest security events and correlate them (find patterns of activity) with known attacks. Furthermore, next generation SIEM technologies can create profiles of normal user behaviour and use these profiles to spot unusual activity – often a vital clue when credential theft is happening, since the volume of events coming from authentication systems under loading from a brute-force attack will shoot up.
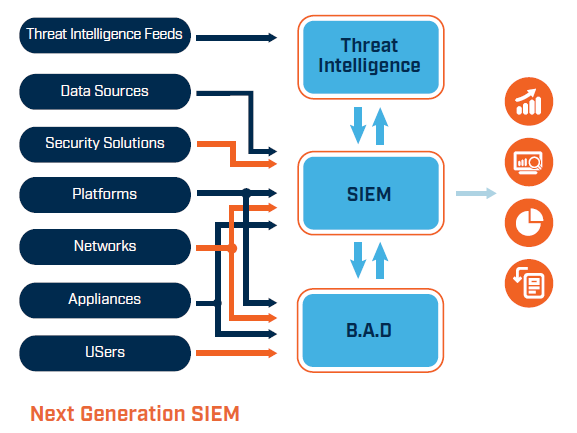
A SIEM helps address this technical side of security, allowing security managers and CISOs to focus on user education and general security awareness training. But what happens when there is a breach, be it malicious or accidental?
Be Aware of How to Respond to Attacks
Incident response is one of the most important stages of cyber threat management, but it’s the least well understood or rehearsed. In the same way that organisations use fire drills to educate their staff on what to do if their building goes up in flames, the security team needs to factor incident response drills into their organisation’s preparedness.
Response drills should factor into security awareness programmes, since knowing what to do if there is an incident (or even if a user clicks on a phishing link) will oftentimes be the difference between stopping an attack before it causes damage and a devastating outcome that could be existential to the organisation.
As Angelene Falk said, “Employees need to be made aware of the common tricks used by cyber criminals to steal usernames and passwords.” This extends to knowing exactly what to do if an attack happens. “If a data breach occurs, early notification can help anyone who is affected take action to prevent harm. By changing passwords, checking your credit report, and looking out for scams using your personal information, you can help minimise the harm that can result from a data breach.”
Read previous blogs on OAIC Notifiable Data Breach Reports here, here and here
[1] https://www.oaic.gov.au/updates/news-and-media/notifiable-data-breaches-for-october-december-2018/
 About Huntsman
About Huntsman







