Squeaky clean cyber hygiene has never been more important. Several Victorian hospitals in Australia were recently hit by a ransomware attack, causing many of their most important administrative systems to be shut down to prevent the malware from spreading. Included in those areas of the business affected by this attack were systems running their financial management, internet and email services, many of which have taken over a week to restore.
Health care providers were also forced to disconnect patient record systems, booking systems and their internal management systems from the internet to properly contain the spread of the malware, causing widespread disruption.
Interestingly, Victoria’s auditor-general had previously warned the state’s health care provider that their IT systems were “highly vulnerable” to attack, when their own internal security auditors discovered exploitable weaknesses in systems that granted them access to patient data. You can read the full report here if you are interested.
The audit report states that “We found staff user accounts at all audited agencies with weak passwords, which were accessible using basic hacking tools. We successfully accessed administrator accounts, which are a key target for attackers because they give ICT staff access to all system files. We also found that health services rarely used multi‐factor authentication (MFA), even for ICT staff and administrator accounts.” Cyber Hygiene was poor.
What can critical services providers, such as healthcare, do to elevate their cyber hygiene and raise their defences against these kinds of disruptive cyber attacks?
Implement an effective cyber risk framework
The Australian Cyber Security Centre (ACSC) has recommended eight effective cyber security controls that would have reduced susceptibility of these Victorian hospitals to the ransomware attack. This framework is known as the Essential 8.
ACSC’s Essential 8 includes multifactor authentication, patching of applications and operating systems, and application whitelisting, in this list of essential security controls. If they were all used within the Victorian health care providers’ infrastructure, there is a strong possibility that the ransomware would not have been able to gain control. Application whitelisting, for example, prevents unknown executable code from running, so if this was protecting these Victorian hospitals, the ransomware would have been identified as “unknown” and prevented from running. If the malware cannot execute, it is rendered inert.
ACSC published a suite of advisories and how-to guides for all aspects of the Essential 8, which can help organisations plan and implement each control. In their introductory guide, called Strategies to Mitigate Cyber Security Incidents, ACSC lists several approaches for each control, while in the companion document, Strategies to Mitigate Cyber Security Incidents – Mitigation Details they go into a lot more detail. Both guides are recommended reading for anyone looking after their organisation’s ICT systems, irrespective of size or complexity.
Users with weak passwords is one of the most common vulnerabilities affecting Australian organisations, and it’s something that is easily fixed. By introducing a second factor of authentication, known as multi-factor authentication (since you can string together as many as you deem necessary), it becomes virtually impossible to take over an account, even if the password remains weak. Without the second factor, which is often something the user carries (like a token or their phone) or something they are (fingerprint scan, retina scan, facial scan), the attacker can’t use the password. To obtain that second factor, the attacker’s job is much harder, since they need to go after a specific user, and in some cases, they need to physically obtain the authentication device, so the risk to them elevates exponentially. Most cyber attacks are opportunistic, so these would almost certainly be prevented. Only attacks carried out by a determined hacker with specific goals, who has the funds and technical expertise to continue would have a chance of success, but if all ACSC’s Essential 8 controls were fully implemented, then they would likely remain unsuccessful.
Measure security control effectiveness
Organisations that adopt the Essential 8 often run an implementation programme that identifies the impact of rolling out these changes to the organisation and fully operationalising them. However, once that programme of work completes, it becomes incredibly difficult to remain compliant as the nature of ICT systems is that they frequently change. Patches, updates to applications, hardware maintenance, technical refreshes, and new operating systems are all likely to happen over the following few months and years, and with each patch or upgrade, the basic cyber hygiene controls included in the Essential 8 could be broken.
Benefits of regular testing and auditing
Without testing or regular auditing, it’s often impossible to see where controls have been weakened, leaving the organisation again open to attack. The issue this time is that while previously the organisation may have been cautious since they knew they were vulnerable, now that they believe they are protected by the Essential 8, complacency may set in. For example, before implementing the Essential 8, a ransomware incident reported to the security team may have seen them drop everything and launch a full-scale incident response activity. But now they think they are protected by Application Whitelisting, they might deprioritise the incident, not realising that infection is now raging through their organisation.
What can organisations do to monitor compliance against the Essential 8?
Continuous compliance monitoring solution
Huntsman Security has developed a compliance monitoring solution that provides continuous measurement of dynamic cyber risk, known as the Essential 8 Scorecard.
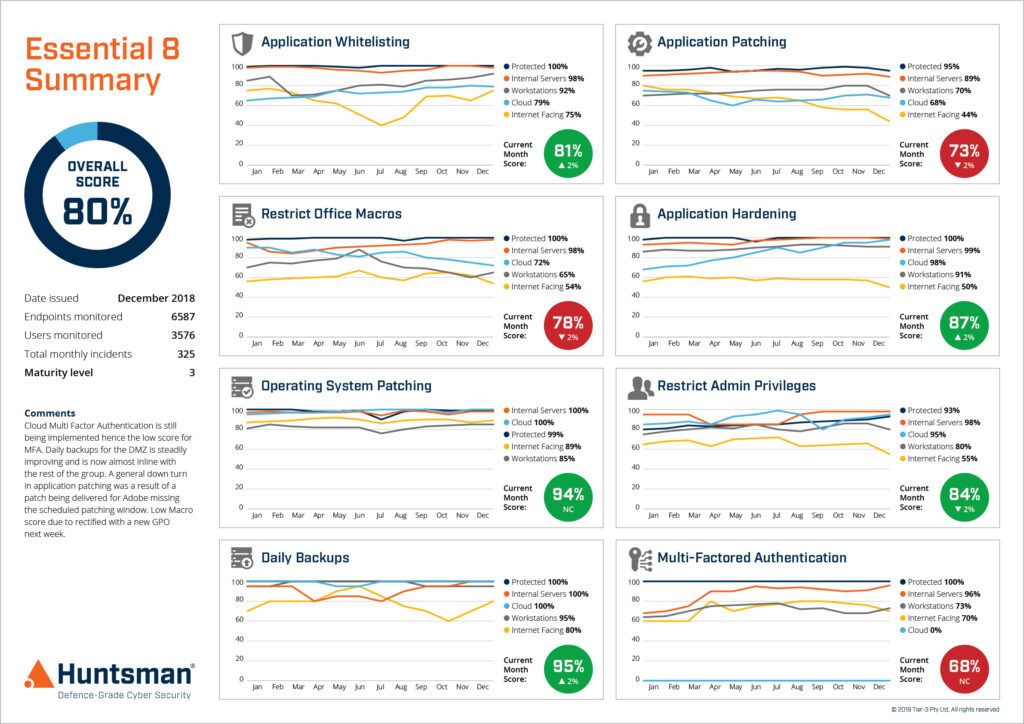
Essential 8 Scorecard – Trend Report
The Essential 8 Scorecard provides measurement of each of these security controls, allowing management to continually monitor the cyber health of the organisation. At the management level, the scorecard displays the organisation’s maturity against the Essential 8 framework and gives an immediate view of coverage across the entire environment. Since it also monitors each control in real-time, non-compliance is reported on a live dashboard showing the risks against each control. Management reports are automatically distributed to the appropriate stakeholders (CIOs, Auditors and Compliance & Risk Managers), while operational reports are sent to the relevant security teams with details of each control’s status.
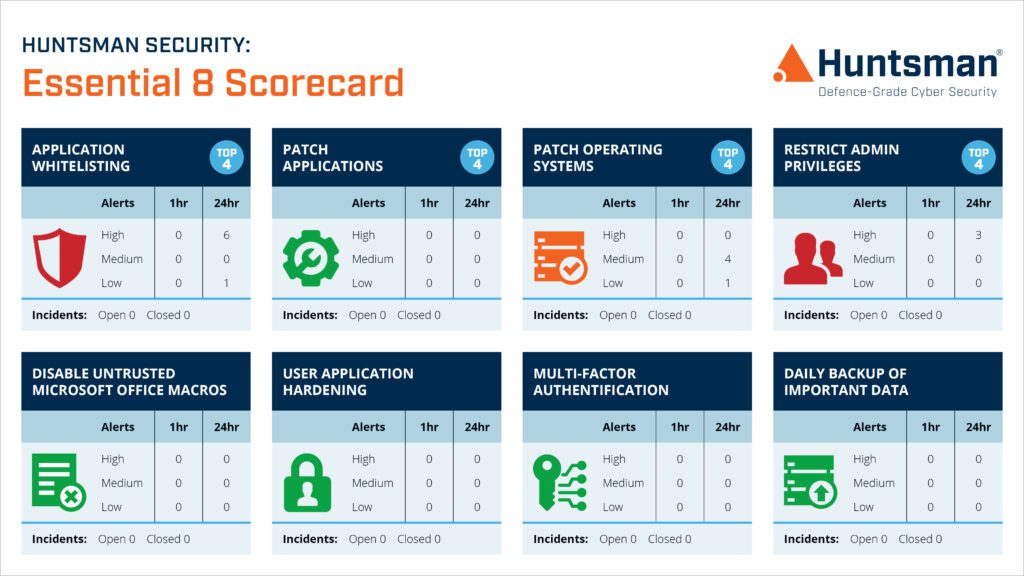
Essential 8 Scorecard – Operational Dashboard
In addition to the real-time compliance dashboards, security analysts receive alerts when non-compliance occurs, so the security operations centre or incident response team can mobilise, investigate and remediate before it becomes an issue.
If Victorian healthcare providers were to implement and maintain the Essential 8, they would significantly elevate their security posture and could well have prevented or significantly reduced the impact of the recent attack.
 About Huntsman
About Huntsman




