Organisations introducing threat hunting into their operational security team’s remit will encourage a proactive approach to detecting and responding to sophisticated cyber threats. Threat hunting demands disciplined and focused effort using threat intelligence to inform the investigation team on what to examine. Incorporating the MITRE ATTACK Framework into your organisation’s threat hunting model is the best way to determine which tactics, techniques and procedures (TTPs) to search for across your environment.
Fundamentals of threat hunting
It’s essential to understand that threat hunting is not like other operational security activities, since it’s a proactive measure taken to search for and respond to attacks that were not detected by the traditional Security Operations Centre (SOC) means. Threat hunting is not straightforward. It’s a challenge to document such rapidly evolving adversarial techniques, and unlike creating correlation rules for a Security Information and Event Management (SIEM) system, hunters don’t base their investigations off patterns or signatures. Instead, they use detailed threat intelligence relating to the anatomy of the attack and the motivations of the threat actors to decide what to look for.
Threat hunting is a hypothesis-based approach to searching through the enterprise infrastructure for evidence of active threats or previous attacks. It’s directly related to malware and hacking tools, and the evidence sought by the hunting team correlates with digital artefacts left behind when an attacker traverses through the network or compromises a system. Threat hunting will often lead to an incident response activity should indicators of an attack be detected.
As a hypothesis-driven process model, the hunting team builds a profile of an assumed attack, then determines the kind of evidence that attackers might leave behind. Each hypothesis drives a cycle of investigation beginning with deciding how the actor gained initial access, then modelling each path the attacker may have taken once the initial foothold is gained. At each stage of the attack, and going down each branch of investigation, the hunter looks for indicators of attack in event logs and file systems and system configurations, and if no activity exists, they follow the next branch of the attack tree.
Threat hunting with MITRE ATTACK
ATT&CK is a useful threat intelligence resource developed and maintained by MITRE. Behind the matrix lies a knowledge base of attacker TTPs, all of which are based on real-world observations collected and curated by MITRE’s security team.
Tenacity is a crucial attribute of threat hunters, since it can be tedious work to ensure no digital stone remains unturned. However, using the MITRE ATT&CK matrix, the investigator can build contextual threat models relating to their particular organisation, profiling threat groups who may be seeking to steal their information, then building attack models of the tools and techniques they would use to meet their objectives.
ATT&CK tactics expose why certain techniques are used, and the investigator can then determine the kinds of tools the attacker would use to be successful. Tactics help threat hunters categorise attacks against their systems into phases across a timeline, from initial access through to data exfiltration and gaining persistence on the network. At each stage of this ‘kill chain’, attackers leave behind digital fingerprints which are the evidential artefacts hunters are seeking to uncover.
Security control effectiveness
By focusing on adversarial behaviours and threat group profiles, hunters broaden the scope of their attack hypotheses, and subsequently cast the net wider in terms of the artefacts they look for. The threat model developed for their own business is used to describe post-compromise attacker behaviour within their infrastructure, which quickly exposes the expected system behaviour the attacks cause as the attack unfolds. What this means is, the hunter can search for residual digital fingerprints from previous successful attacks, determine if the attacker was successful and determine which security controls were either ineffective or missing.
The same findings can also inform the SOC team of what kinds of alerts to monitor for, and how they translate into indicators of attack or indicators of compromise as the SOC develops new correlation rules.
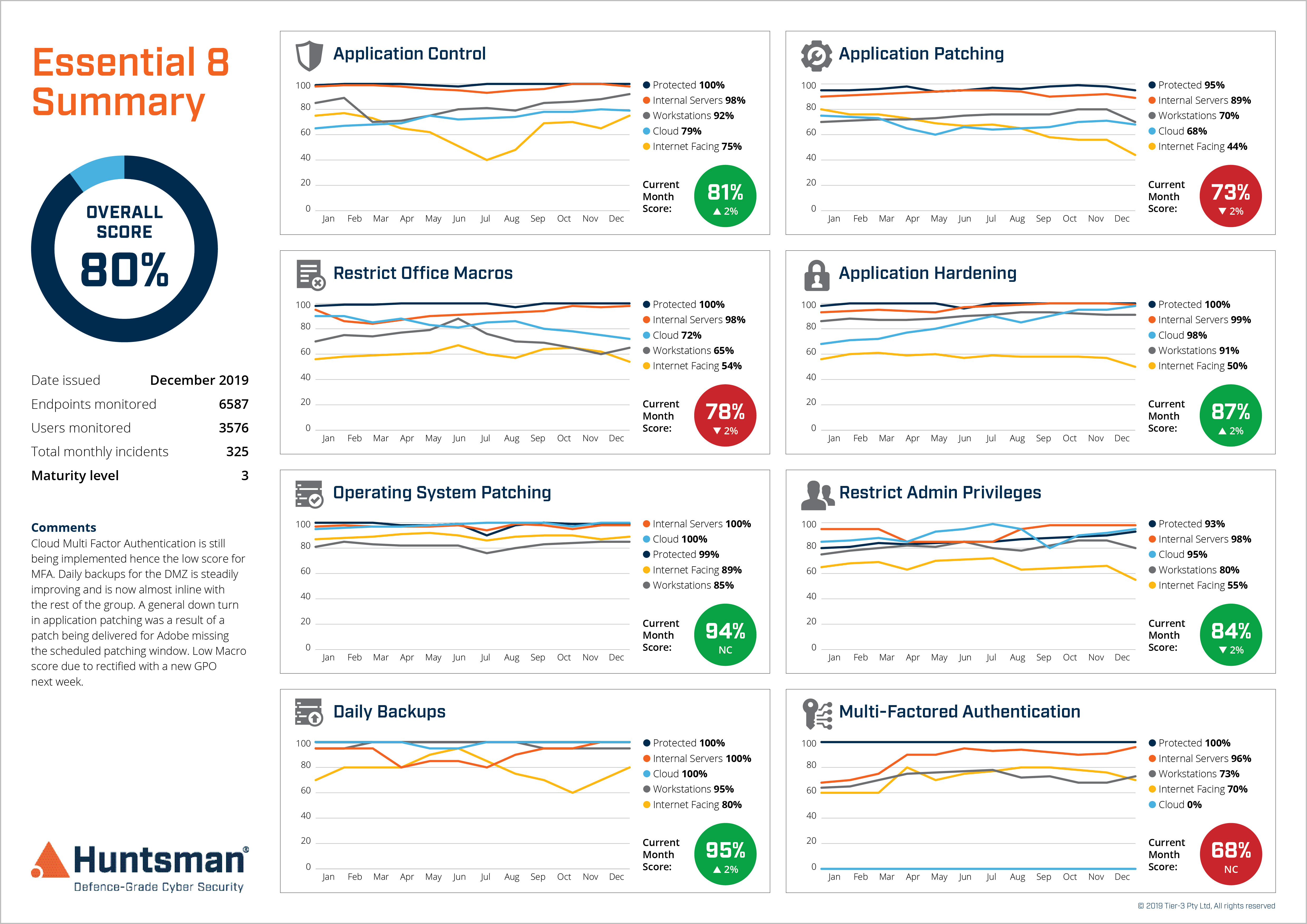
Essential 8 Scorecard – Security Control Performance Trends
The threat hunting continuum
A successful approach to threat hunting is for the incident response team’s technical experts to take on the role of threat hunters. When not actively participating in incident response, they are turning their hand to developing hypothetical attacks, profiling threat actors, and determining how they target your systems. From there, the hypothesis is developed and the hunt begins.
The technology platforms underpinning modern SOC activities – SIEM systems, vulnerability management systems and endpoint detection and response systems – play a large role in hunting, since they can make vast data sets accessible and provide a level of context that would otherwise be impossible to achieve. As modern SOCs are also shifting to using the MITRE ATTACK Framework to categorise their correlation rules and alarms, it makes sense for the threat hunting team and the SOC team to collaborate.
As a continuous cycle of hypothesis development, profiling, data gathering, investigation and back to hypothesis refinement, the hunting team’s efforts are focused on well-defined objectives. The outcomes are always clear – it’s a matter of answering each question with a definitive yes or no. A formally defined scope for each investigation ensures the next iteration of developing a hypothesis is relevant and builds on the previous step. As an output of each step in the hunting continuum, the team can feed indicators of compromise and indicators of attack, all of which are relevant to the systems and context of your organisation, to the SOC team to develop new detection rules. This means that as the hunting team’s work continues, the SOC is also continually updating the monitoring and detection capability, thus continually elevating your organisation’s security posture.
Threat hunting adds significant value to your SOC and takes threat management to an advanced level.
 About Huntsman
About Huntsman



