The Australian Parliament hack, dubbed Australia’s “first national cyber crisis” by the Australian Signals Directorate, shows us all too clearly the risks associated with a targeted cyber breach. When valuable information is accessed the damage can be irreversible. This is particularly true for any country’s critical infrastructure sector. The enduring question remains, realistically what can organisations do to fend off the advances from sophisticated, targeted attacks?
In a previous blog, we wrote about the state of security in Australia’s Victorian healthcare organisations after several hospitals were hit by a ransomware attack. That denial of service attack caused important administrative systems to be shut down to prevent the spread of infection (kind of ironic in a healthcare organisation). For these healthcare providers, Victoria’s auditor-general had already assessed their cyber hygiene as poor, and “We found staff user accounts at all audited agencies with weak passwords, which were accessible using basic hacking tools.”
Critical infrastructure cyber security is critical
Critical infrastructure organisations provide the services that the country relies on for every aspect of life, such as the supply of food, energy, water, transport, communications, health and finance (including banking). A major attack on any one of these aspects of our national infrastructure would be incredibly disruptive, to the point where it could spark a national crisis. However, the underpinning ICT systems keeping these services operational seem increasingly at risk from the kinds of targeted cyber-attacks that are becoming more prevalent.
Australia’s Trusted Information Sharing Network (TISN) for Critical Infrastructure Resilience coordinates sharing of information and encourages cooperation across industry sectors to address the kinds of cyber security threats and business continuity challenges we are now facing from nation states and cybercriminals. The TISN makes a point of referencing cyber security as a major risk and has many publications that explain how cyber risk management and governance, along with technical security controls should be incorporated into resilience strategies.
What we know is that a reasonable proportion of critical infrastructure organisations operate as self-insurers, where no third-party insurance cover is funded, rather they cover liabilities and wear the risks themselves. Most modern insurers include aspects of cyber risk management in their assessments of their clients’ premiums, and in some cases won’t issue cover if there are inadequate security controls in place to defend against attack (or only issue cover at a high premium). Yet critical infrastructure organisations electing to self-insure have no such obligation since they are choosing to wear the risk themselves; our most crucial national infrastructure could be less well-protected than many mid-sized businesses, who have to introduce cyber security controls to get the third-party insurance they need.
The Essential Eight is a Good First Step
The Australian Government’s Essential Eight cyber security framework’s is one of the most effective and practical pieces of advice that any organisation can follow to get started in building cyber resiliency, even if no other security programme or countermeasures are in place.
By implementing just three of these eight controls – patching applications, patching operating systems and using multi-factor authentication – many targeted cyber attacks would be prevented. Victoria’s auditor-general reported that the healthcare organisations it audited, “had weaknesses in aspects of their ICT security. Common weaknesses include inconsistent patching practices, ineffective user access controls and incomplete knowledge of ICT assets.”
Consistent patching is vital to cyber health, as are verified backups and uplifting security awareness (albeit security awareness is not covered in the Essential Eight). Following a cyber incident, organisations will launch a dedicated project to patch their systems and applications and uplift their security posture. Yet ongoing maintenance of their security posture is often lacking, since there is no transition to business as usual operations for that new patching approach. Within a few months, things are back to as they were, as more vulnerabilities are discovered in the complex ICT systems they use.
Without doubt, critical infrastructure providers should take the Essential Eight as the goal of a cyber security review and implement the controls as widely as possible to lift their security posture.
Ongoing Assessment and Compliance
Our recommendation is that organisations, even those that self-insure, implement the Essential Eight controls in such a way that is sustainable and continually assessed.
Huntsman Security’s Essential 8 Scorecard allows organisations to report on their security posture through these eight vital security controls, allowing service management teams to prioritise remediation work when necessary rather than security being something that requires long-winded projects to discover the vulnerabilities. If the organisation falls behind on its patching or the backups are not working properly, it’s flagged with the appropriate management teams on the dashboard and the work can be prioritised.
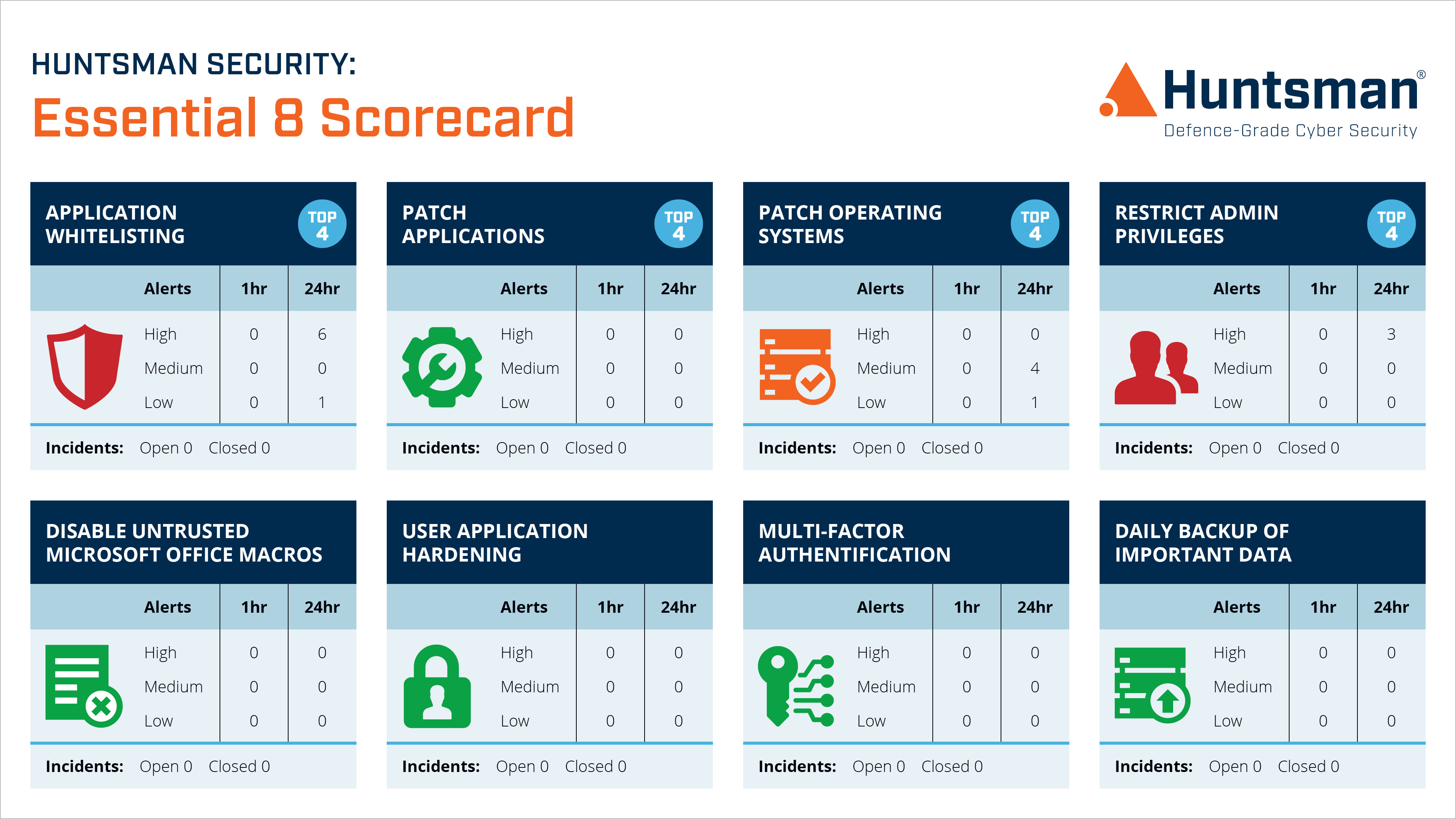
Essential 8 Scorecard – Operational Dashboard
The scorecard automatically gathers relevant security and compliance data from operational systems and highlights when the status of those systems has changed to reduce the security posture. Each control is monitored in real-time, so as soon as a system becomes non-compliant the relevant management team will know.
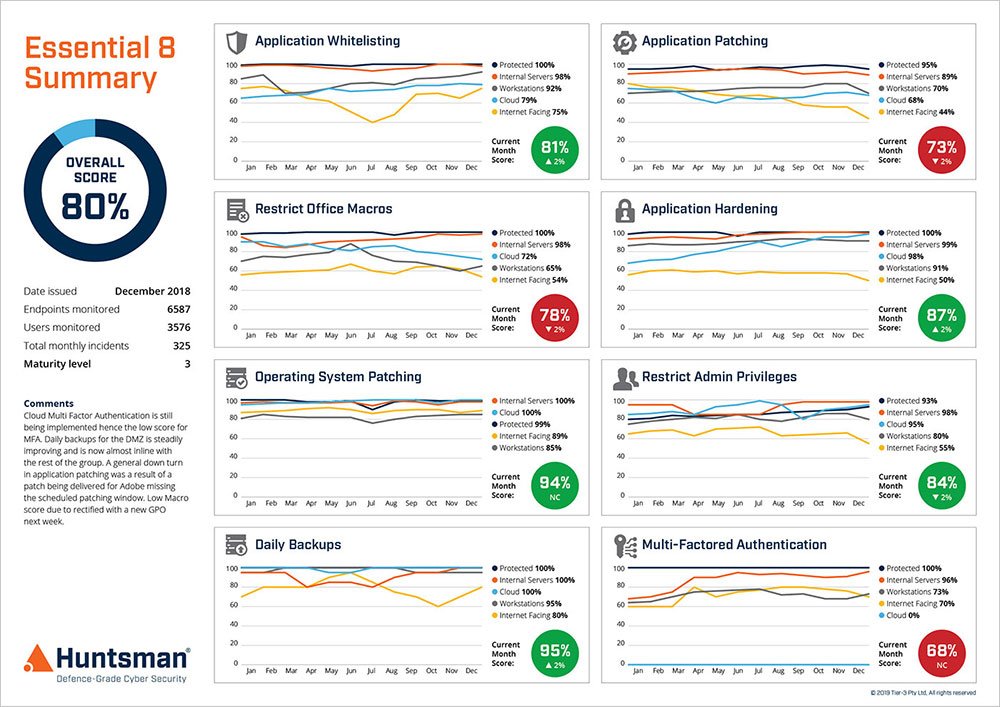
Essential 8 Scorecard – Trend Reporting
The Essential 8 Scorecard helps business risk management teams properly understand their liability, especially as self-insurers, and ensure critical infrastructure providers are better placed to mitigate the risks relating to well-funded, sophisticated cyber threat actors.
 About Huntsman
About Huntsman




