This blog looks at how the MITRE ATT&CK matrix can be used to complement the work of your incident response team in the Security Operations Centre (SOC). It explores how it can help incident responders structure and streamline their investigations. You can read earlier MITRE ATT&CK posts here, here and here.
MITRE ATT&CK recap
The MITRE ATT&CK matrix comprises a knowledge base of threat related data, based on the profiles of specific threat groups (also known as Advanced Persistent Threat or APT groups), along with the tactics and techniques they use to achieve their objectives. With 12 tactical categories, from initial access through to mapping the impact of successful attacks through to the techniques that adversaries use to destroy or steal data and disrupt operations.
ATT&CK is widely adopted across the security industry, from vendors and service providers to in-house security operations teams who use its threat intelligence to inform their development of correlation rules, based on mapping each technique to the relevant technology systems in the organisations they defend to determine how best to detect its use.
Getting started with ATT&CK for Incident Response
The process SOC teams use to develop correlation rules (the detection rules used to match specific system logs and events to adversary techniques) is relatively straightforward. Using a combination of architecture models (i.e. knowing precisely which systems they are protecting and how they act under duress) and threat models relating to specific adversarial behaviours, the SOC develops detection rules that trigger alarms when those conditions are met. However, the same process can be reversed by incident response teams and used in a proactive way to assist in investigations to speed up the determination of how the attacker penetrated the network and moved to their final objectives.
Start with containment
Let’s assume the SOC team has detected an attack somewhere in your enterprise and hit the escalation button to call in the Cyber Security Incident Response Team (CSIRT). The very first thing that any CSIRT team will do is analyse all the relevant data and quickly make a call on the impact the breach may be having on the enterprise then move to the containment phase. Containment is where they ringfence the threat to restrict its movement through the environment, thus limiting the impact the attack has on the rest of the business. Once the CSIRT team has set containment measures in place, the next stage of the response plan is usually to investigate the nature of the threat and determine how it infiltrated the environment. It is at this stage when MITRE ATT&CK becomes an incredibly useful reference model.
The nature of the threat
The CSIRT team will determine what kind of threat or exploit they are dealing with so that latter actions account for any possible mitigations the attacker might have to being investigated. By using the MITRE ATT&CK matrix, the team matches techniques discovered by the SOC to determine what stage of the kill chain (the chain of activities adversaries follow to achieve their objectives) they are looking at. Let’s say for example, a SOC alarm triggers when an attacker ties to brute force one of your privileged accounts. This technique is listed into the Credential Access tactical category of the ATT&CK matrix, as shown in Figure 1.
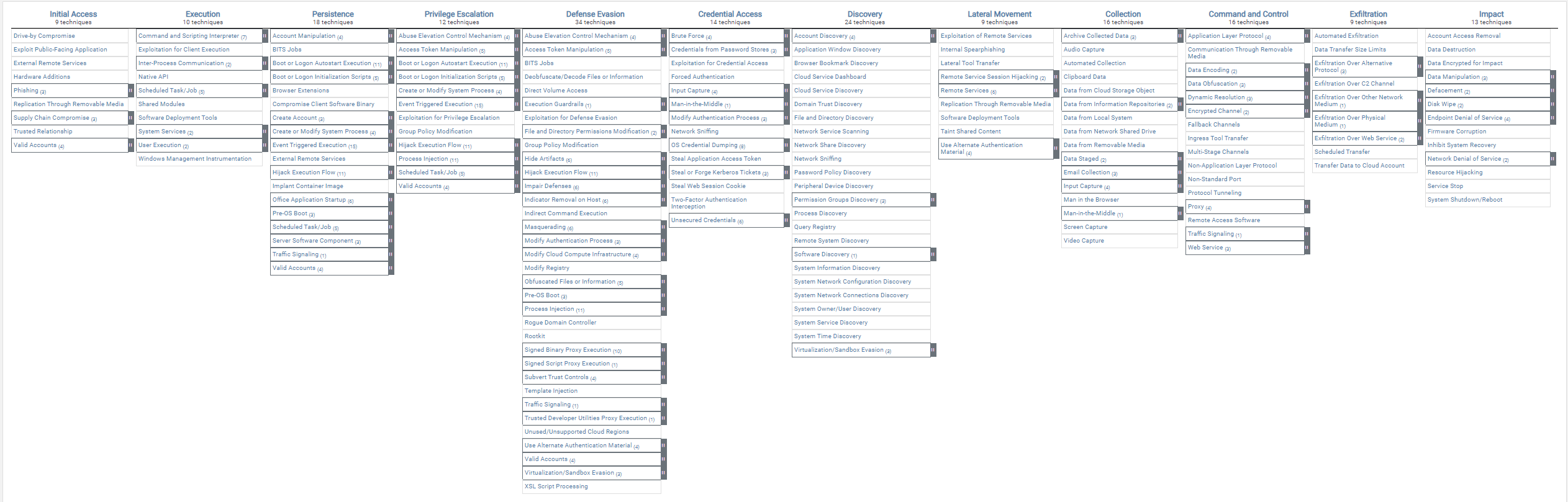
Figure 1 The MITRE ATT&CK Framework
If the investigator drills into the details of the Brute Force technique, they get the following information:
“Adversaries may use brute force techniques to gain access to accounts when passwords are unknown or when password hashes are obtained. Without knowledge of the password for an account or set of accounts, an adversary may systematically guess the password using a repetitive or iterative mechanism. Brute forcing passwords can take place via interaction with a service that will check the validity of those credentials or offline against previously acquired credential data, such as password hashes.”
MITRE ATT&CK Matrix, 2020
Now what the investigator can do is work backwards from this tactical category of Credential Access to determine how the attacker got into the systems in the first place to launch this attack.
Threat Actor profiles
Threat actor profiles, based on MITRE’s threat intelligence on known APTs, can be used to map observed behaviours to possible adversaries. Incident responders will also know what kind of business they are protecting, what information an adversary may be targeting and what kinds of objectives they might be seeking to obtain. This collection of threat actor profiles mapped to in-context targets within your organisation is what security teams call a threat assessment, since it guides the business on which adversaries may be targeting them and what their objective is, for example business disruption or stealing confidential information.
The threat profile for APT39 contains a list of the exploitation tools and malware that were used for various stages of the attacks they have been responsible for in the past. Figure 2 shows a sample of the software tools APT39 has used previously.
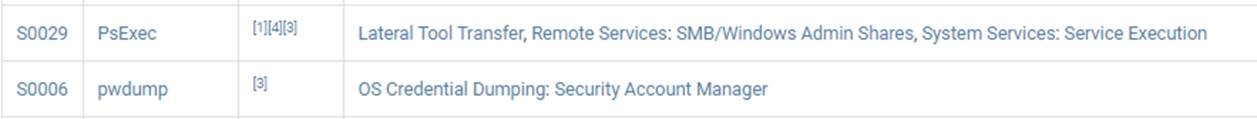
Figure 2 Hacking tools frequently used by APT39
Each tool or technique causes an effect on the target system, usually resulting in the production of logs and events the SOC can collect and report on. By looking at the technique of Credential Access technique of Brute Force, ATT&CK lists the threats groups using this technique, as shown in Figure 3.
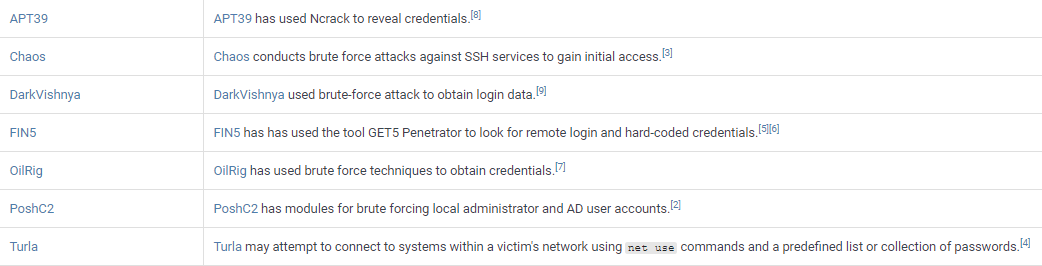
Figure 3 Adversary groups known to use Brute Force techniques to steal credentials
Working backwards
Now that the incident response team has a possible threat group that may have initiated the attack, they can use that profile to work backwards along the kill chain to look for techniques in previous tactic categories. The previous category is Defence Evasion, so by looking at the APT39’s list of known techniques, the following (Figure 4) techniques can be investigated for their use within the organisation’s infrastructure.
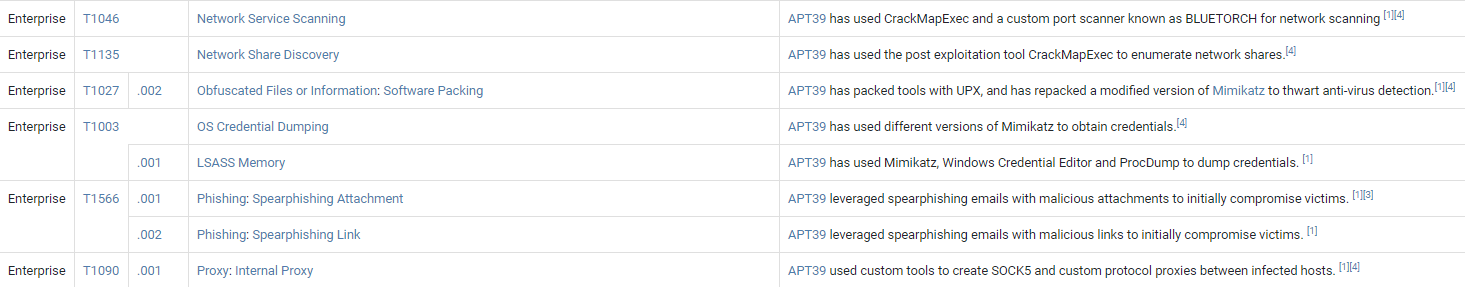
Figure 4 Techniques used by APT39
The list shows a technique called Obfuscated Files or Information. Adversaries use this technique to make malware harder to discover or access by using encryption or encoding it in an obscure manner so that SOC teams have a harder time detecting its presence.
Finally, through this branch of investigation, the CSIRT team looks at the procedures used to obfuscate files and information and can use the intelligence from the long list of procedures to search for evidence and artefacts falling into this category. For example, some adversary groups use PowerShell Base64 obfuscation for hiding malware. The team can now start looking for this kind of hidden data, knowing that the method for finding it has been detailed by one of the many research companies contributing to or referenced from the MITRE ATT&CK framework. For example, FireEye’s report, Not So Cozy: An Uncomfortable Examination of a Suspected APT29 Phishing Campaign, contains an overview of all the techniques used in this attack, including details on the use of PowerShell Base64 obfuscation.
Finishing off the investigation
Once the CSIRT team has found evidence of one of the techniques in the Defence Evasion category, they can move on. It’s very likely this is the one that was used to move to the next stage, so they don’t need to keep looking for other techniques – this short cuts the investigation process since it provides a more targeted view of how the adversaries accessed and moved through the organisation’s systems. By systematically working backwards, the incident response team can eventually determine how the attacker gained initial access, thus allowing the IT team to patch or reconfigure the vulnerable ingress point and stop future intrusions of this nature.
Huntsman Security has adopted the MITRE ATT&CK matrix into its security platform. If you want to explore building a SOC and using the MITRE ATT&CK matrix to detect and respond to threats, please contact us via the button below.
 About Huntsman
About Huntsman






