No one will dispute that managed security services (MSS) are in high demand and many IT service providers are assessing the viability of MSS as a business model to see if it’s something they should offer. Yet, the specialised nature of security services, especially the ones that complement core MSSP services such as monitoring and incident response, are often out of reach.
To offer penetration testing, digital forensics or open source intelligence analysis, your organisation needs people who have the relevant experience and certification in doing those activities, and these resources don’t come cheap. To build these into your service portfolio is a costly exercise when you don’t yet have demand from your customers. Nonetheless, customers typically want one MSSP who offers every service rather than having to manage multiple contracts. So, how can you offer all the Managed Security Services needed to please customers, while reducing the start-up costs and keeping business risk to a minimum?
What Constitutes Core MSSP Services?
At their most fundamental, MSSPs offer just two services to meet their customers’ requirements. These are:
- Protective monitoring; and
- Incident notification.
Protective monitoring is most in demand, where every customer engaging a service provider needs their systems and networks monitored for cyber threats. Service providers typically offer this, along with incident notification, as a package of services from their Security Operations Centre (SOC) and may market it as SOC services.
Monitoring is normally provided using a Security Information and Event Management (SIEM) system, possibly integrated with User Entity Behavioural Analysis (UEBA[1]) and a network monitoring tool, such as Snort[2]. This can mean that risks posed by malicious insiders can be mitigated as a component of core SOC services, rather than being sold as an additional add on at extra expense – a feature that MSSP customers will appreciate!
Ways to Approach Additional Managed Security Service Offerings
Depending on whether the customer knows in advance which services they want, or whether they mature into it once the core services are running is moot, since at some point they will be looking for the following service categories:
- Consulting
- Device management
- Product resale
- Security testing (penetration and vulnerability)
- Compliance monitoring
- Incident response/digital forensics
As a Managed Security Services provider, it’s important to look at the investment needed for each of these and determine whether you offer them from your own staff, or you build a subcontracting framework that allows you to engage experts as and when you need them.
Some of these services make sense to provide in-house, such as compliance monitoring and product resale. These two are easy to set up, since they are more about extending SOC monitoring to focus on compliance dashboards and having the right contracts in place with suppliers to resell their products. Compliance, and measuring the effectiveness of your security controls, can be made even easier with a Security Scorecard, since its purpose is to monitor key security controls and ensure they are always performing within tolerance, notifying the SOC when something slips out of compliance.
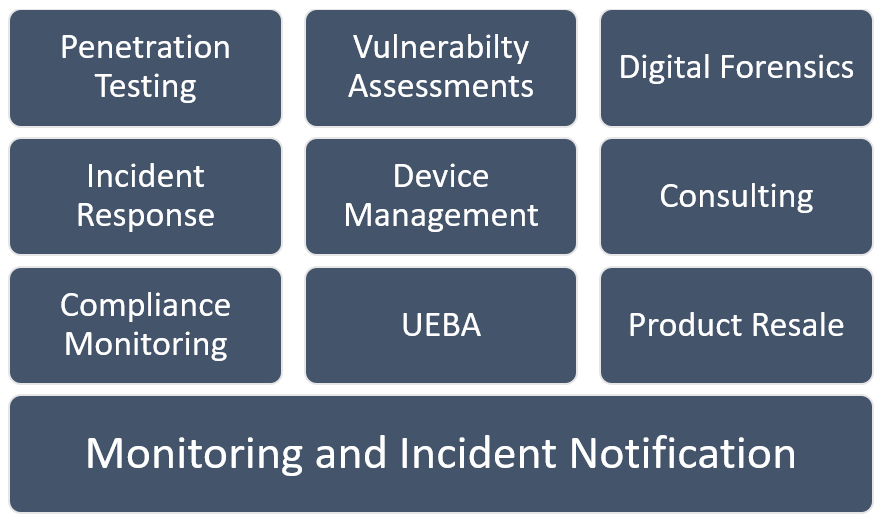
Figure 1 Full list of MSSP service offerings
Figure 1 shows the list of MSSP service offerings from core at the bottom (monitoring and incident notification) to the most complex and technically challenging at the top (penetration testing, vulnerability assessments and digital forensics).
Incident Response
As a provider of Managed Security Services you should be careful about the extent of incident response services you say you can provide, since onsite incident response can require the responders to take control of an evolving threat situation and competently steer all parties involved towards a conclusion where the impact to the customer is, as much as possible, minimised.
Given the nature of major incidents, customers will often be in a state of disarray, with senior executives demanding answers while looking for scapegoats to blame for losses or service interruptions. The incident response team needs to be professional, keeping everyone else cool and focused, having previous experience in handing similarly complex incidents is most valuable. Often this team of experts is not the team of analysts in your SOC, so before you offer this, make sure you have the skills and capability to do so.
Device Management
Device management is an optional service that many MSSPs see as a low margin capability that would only be provided if there is no other way to win a contract. Managing security devices, when you don’t also have control over other onsite technology, can be troublesome and often it’s better to help the customer see their IT services provider is best placed to provide this, since they already manage most of the customer’s infrastructure. A better option is to integrate your SOC service with the 3rd party service and ensure that all security device management outcomes are understood by both parties, so any request from the SOC to block a threat is turned into appropriate actions at the end device level.
Consulting
Consulting is a very broad service offering that conceivably covers many outcomes for customers. Some service providers offer a lower level service catalogue of consulting activities, such as:
- Security architecture reviews
- Policy assessment
- Compliance reviews
- Incident readiness assessments
- Training and workshops
These are just a few of the items that consulting teams deliver to customers, but really, it’s any activity that requires someone with expertise to come to site in an advisory capacity. All MSSPs should be able to offer consulting on the implementation of their core services, even if it’s just deployment advice and integration advice for their services, i.e. how the customer should react when they get an incident notification.
Other consulting activities, if not in the current workforce skillset, should be provided through a subcontract with a specialist provider who has the experience and certifications needed to offer these.
Subcontracting Additional Services
The additional services that you cannot provide directly can be provided through a carefully constructed contract framework with other providers who have the skills and experienced staff to offer these. There are two approaches to this:
- Either resource augmentation contracts, where the contractors work on your team as one of your employees and the customers doesn’t know they are contracting to you rather than permanent employees. From the customer’s perspective, it shouldn’t matter, but they may question your honestly, especially if they know that person works for another company and you are presenting them as an internal resource, or;
- What’s better is a full business-to-business agreement where you sell the value of the partnership and the 3rd party company as experts in this field. The fact that you have acknowledged the experience gaps in your portfolio and sought ways to provide these services to customers through one, easy-to-navigate, contract is where you should focus.
The only caveat on the aforementioned model is that you need to carefully compose a non-compete agreement with your subcontractors, to make sure everyone understands that your customers are your customers and they should not be approached directly for work by your subcontractors. There is always a risk that a specialist subcontractor, especially a very small provider, can get blinded by the revenue potential of going direct to your MSSP’s customers, not realising that this breach of trust damages every party in the relationship.
Build Sustainable Security Services
Subcontracting specialist services ensures MSSPs offer the full portfolio of security services while growing their customer-base and tendering for business in markets they may not typically work in. Just pay attention to the nature of the subcontract relationship and ensure it is mutually beneficial for all parties.
[1] https://searchsecurity.techtarget.com/feature/User-behavioral-analytics-tools-can-thwart-security-attacks
[2] https://www.snort.org/
 About Huntsman
About Huntsman



