Cyber threat actors are continually innovating in an attempt to bypass modern cyber security controls. Security systems must adapt at the same rate or faster to ward off this evolving threat, otherwise the criminals will eventually win. Organisations often rely on annual security reviews to assess their ongoing security posture, identifying deviations from an approved control set that leave them at risk. Nevertheless, security managers also require the means to monitor their organisation’s security posture in real-time, since waiting for the annual audit leaves them blind to non-compliances prior to the review. Let’s look at how key security controls can be continually monitored to provide a level of assurance that’s otherwise impossible to achieve.
Countering the Evolving Threat
Cyber threats are measured as a function of the risks they pose to the business, irrespective of whether the target is information, systems or personnel. Cyber Security demands solutions that deliver risk management outcomes, with specific risk mitigation strategies countering the immediate threat as well as the evolution of threats over time.
Businesses can adopt a governance framework to manage their security posture, adding rigour and focus to their overall security programme and identifying key security controls to manage cyber risks. Frameworks like ISO 27001 or the payment card industry’s Data Security Standard (PCI-DSS) are excellent approaches for establishing this kind of organisational governance, with each of these requiring a formal audit and official certification review to remain compliant. However, there is a long period of time between audits, up to twelve months between formal reviews, which leaves security managers crossing their fingers and hoping for the best in terms of their compliance with each of these controls.
Security managers require the means to continually monitor their security posture and the health of security controls employed to manage risk. If the security posture changes or individual controls fail to operate effectively, an alert should be raised and the problem fixed before it is exploited by an attacker.
Cyber Security Scorecard
The idea of using a scorecard to determine how well a business functions has been around for some time. Metrics are captured and analysed to allow management to see how the business is performing, allowing them to seek better ways of operating to optimise operations. In manufacturing, for example, key performance indicators (KPIs) are used to measure and report on the percentage increase in revenues, the percentage reduction in operating costs and the percentage reduction in returned goods.
Measuring the Efficacy of Security Controls
In cyber security, metrics relating to each of the business’s critical controls can be used to monitor their efficacy and ensure the business’s security defences remain intact. The question is, how can you obtain this level of visibility over security controls, when many of these controls relate to entire infrastructure capabilities, such as patching operating systems or taking regular backups?
The best approach is to pick a small number of key controls that, if working as they are designed to, deliver the greatest amount of risk reduction to the business and that can be monitored used technology, so you know immediately when something deviates from the baseline.
Pareto’s Principle in Cyber Security
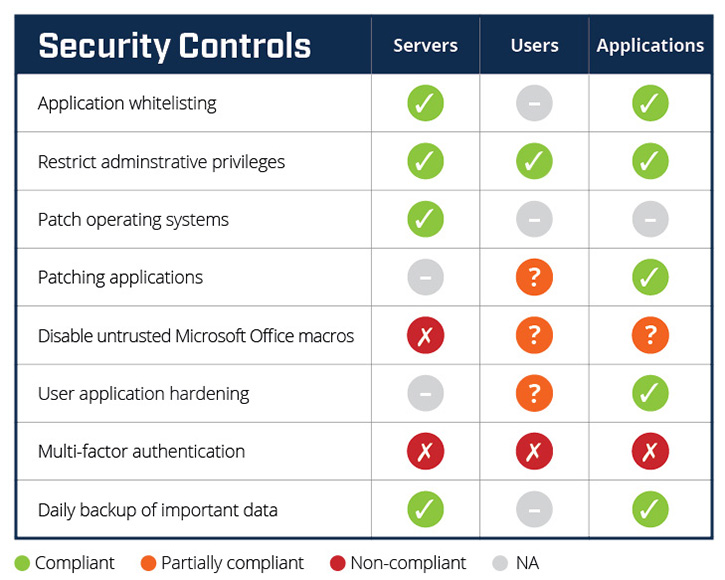
The Australian Cyber Security Centre (ACSC) has identified eight critical security controls that they say defend against 85% of targeted attacks, known as The Essential Eight. Using these controls as the basis of your scorecard means you can rest assured that the business is reasonably protected. This means the security team can focus on the more complex task of managing the remaining 15%.
Real-time Monitoring of the Essential Eight
The Essential Eight mitigates the most common targeted cyber-attacks, with the top four controls defending against the majority of attacks. Yet, most security programmes come unstuck, since a lack of visibility means too much time is spent analysing the implementation of these basic controls, and they never find the time to tackle the hard stuff.
A systemic approach to monitoring controls is required. This can use technology to proactively gather data and present it as something with tangible meaning, identifying weaknesses or non-compliance within the operational environment. Reporting on the overall patch state, for example, helps the business know where patches have or have not been applied and hence, if a critical patch is missing, that information can be used to prioritise the service management team’s work to remediate that issue.
Start Measuring your Cyber Posture
Protective monitoring is a core discipline in security operations. Security information and event management (SIEM) systems are commonly used to collect and process the flood of security events produced by security and operating systems and applications, to provide the visibility needed to detect the threats targeting the business.
Huntsman Security Scorecard
Huntsman Security’s SIEM can monitor anything that produces security information and events. The Huntsman Security Scorecard is a Computer Assisted Audit Technology (CAAT) that utilises SIEM type collection capabilities to monitor the efficacy of your security controls.
By configuring the organisation’s CAAT to monitor critical business assets and systems for their compliance against your key security controls, such as the Essential Eight, you gain real-time visibility of their performance; and adjust as necessary.
Take the first steps to gaining visibility of your cyber posture and improving the cyber resilience of your organisation by downloading the Security Scorecard Overview

 About Huntsman
About Huntsman