To ensure threat data is processed into cyber security threat intelligence quickly, analysts rely on their technologies to verify and contextualise it.
Why Raw Data is Not Cyber Security Threat Intelligence
One of the greatest weapons cyber security operations teams have for fending off cyberattacks is high-quality, verifiable and actionable cyber security threat intelligence. But beware, labelling raw operational data as intelligence is overvaluing its importance. Customers will quickly learn that much of this “Threat Intelligence” is little more than a stream of IP addresses, URLs, hashes and signatures; and all you can do with it is a basic block or search.
To realise any value from threat data, it needs to be processed, verified and contextualised so that the business can trust it and act upon it. Ingesting threat data into your security technologies, such as firewalls, IPSs and SIEMs, can allow you to counter a variety of attacks, but only if that information has relevance to your business, so the protection it offers is specific not just generic.
Cyber Security Threat Intelligence: The Intelligence Lifecycle
Military and national security doctrine has documented the intelligence process for hundreds of years. Intelligence analysis and production has been refined over centuries of warfare and espionage, with the difference between data, information and intelligence well defined.
The intelligence process takes operational data through several stages of maturation, from individual data fragments through to contextual, actionable intelligence products, verified by multiple sources. Furthermore, the process shown in Figure 1[1] transforms the data through three clear stages: the data is first processed into information then, through analysis and production, it gets published as intelligence. Finally, the system allows for feedback which informs the analyst whether the sources were good enough to allow them to meet their end goals.
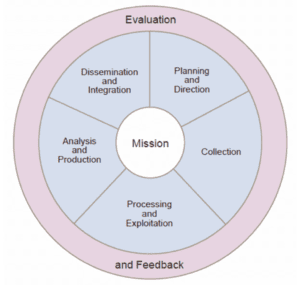
Figure 1 Taken from Joint Publication 2-0 U.S. Dept. of the Army
Intelligence analysts assess operational data against command objectives (their business requirements) all day long, verifying it against multiple disparate sources to authenticate and validate it. Critical intelligence products are weighted by their significance to the requirements: attributing value, reliability and context. Only then is the intelligence product published and only then can it be acted upon. But how does this apply to cyber security and SOC operations?
Cyber Security Threat Intelligence: Open Source threat information
There is no shortage of Open Source threat information available on the Internet. You can subscribe to aggregated feeds, such as Hail a Taxii, which offer a stream of, “Open Source Cyber Threat Intelligence” in a format that SIEM technologies can ingest (known as STIX). The traditional intelligence model (Figure 1) suggests that this data is the input to the first stage of the process, but it still needs to be analysed, processed, validated and contextualised to be relevant to your situation.
The main problem with cyber security is that the time between a threat emerging and the operational team acting to protect the business needs to be as short as possible. Processing, validating and contextualising the data flowing in from threat feeds, such as Hail a Taxii, takes time but to capture an attack it needs to be fast. Rapid threat containment is crucial.
Cyber Security Threat Intelligence: Speed of data processing
To ensure threat data is processed into intelligence quickly, analysts rely on their technologies to verify and contextualise it. The technology needs business context and must have the smarts to validate what it’s seeing across multiple sources; preferably automatically, and at machine speeds. For example, when we get to the stage when technology determines an IP address found on a threat feed matched one from a web gateway’s log, and it initiates an automatic block in the firewall, we have succeeded, right? When the raw data is automatically taken through the intelligence process, resulting in a context-relevant action, then we can claim we are following the true intelligence process. In some cases, this is possible today, but there is still some ways to go before it’s working at all levels of operational, tactical and strategic analysis.
Cyber Security Threat Intelligence: Automated Threat Verification
Many intelligence capabilities are already possible, if your analysts know how to use all the features of your technology. Huntsman Security’s Next Gen SIEM SOAR can perform a variety of enrichment services including automatic threat verification and signalling of external technologies to automatically act on a threat.
As an industry, we are going through a scientific revolution, finally building in artificial intelligence, machine learning and behavioural analyses into our products, allowing us to finally get close to keeping up with the criminals. But collaboration is required to reach the goal, where threat feeds are only a small part of the intelligence puzzle. We need a variety of intelligence feeds, sourced and processed by analysts who can build operational, tactical and strategic intelligence outcomes for our businesses. Only then can we claim that we do Intelligence properly.
[1] https://www.dtic.mil/doctrine/new_pubs/jp2_0.pdf
 About Huntsman
About Huntsman