As an increasing number of regulators and industry bodies are adopting stronger policies and frameworks, monitoring cyber security controls has become an important area of focus for boards and executives.Executive teams are becoming increasingly accountable for their organisations remaining on the right side of authorities and the law. Yet, the gap between compliance goals and control effectiveness seems to be widening as IT governance fails to keep pace with changing security operations and technologies at the coalface.
Leadership teams must find a way to bridge the gap between compliance requirements and security control implementation so that any divergence can be quickly detected and rectified.
Mapping Compliance to Technical Controls
The communication of an organisation’s cyber security posture to the board requires the translation of technical information into clear and concise KPIs. It is vital that changes in these security metrics are appropriately communicated in a timely manner and in the language of governance and risk. Subjective assessment has now been replaced by automated technologies that provide evidence-based security risk information.
Most security policies and controls have their roots in proven strategies that eliminate or mitigate the risks identified from the successful exploitation of particular vulnerabilities. The successful implementation and operation of such controls will, in turn, limit the risk – likelihood or impact – of a successful attack.
The effectiveness of these controls can now be easily measured and any shortcomings quickly reported to senior executives and board members for their attention. For example, patching, as a control measure, is an effective way to reduce the risk of a software vulnerability being exploited by an attacker. If patches are regularly applied to operating systems, network devices and applications, the business will be more resilient to an attack (perhaps not impermeable, but certainly more resilient).
While the specifics of these controls may be complex and the realm of the security team, the board’s interest is whether the program is in place and operating effectively. Not unlike the intricacies of foreign exchange or any other business risk, the board doesn’t need to know details of the hedging strategy or the technicalities of the security vulnerabilities. It does, however, need to understand the nature and quantum of the risk and how it is being managed. In our digital world risk-based decisions need to be increasingly made in reconciling cyber and operational activities.
“I can see clearly now”
Performance dashboards and scorecards are being used to visualise the nature and performance of these controls against security policies and recognised frameworks. With clear visibility of the compliance, performance and trends for each of the controls, board members and executives can remain informed of their compliance situation and of anything needing their particular attention. A red or amber warning on the scorecard, for example, will instantly alert the board which can quickly dig into the issue with the appropriate stakeholders before attesting to their risk position. In this way the regular security control report is an aide memoire for senior executives and board members about the state of enterprise cyber security and any matters requiring their particular attention.
Engineering teams, working at the coalface to resolve technical challenges, are not as informed by RAG (red/amber/green) status reporting as senior management. From an engineering perspective this aggregate view is less helpful, as it lacks specificity and details necessary to identify, investigate and resolve risks associated with particular threats.
The reality, of course, is that both views are needed, one for operational details and the other as a summary report. As the business scans its systems for the existence of vulnerabilities, the same data can show engineers what needs to be fixed, where the risks lie. The matching summary view of risk, which highlights performance over time, can then be published to the board and other stakeholders for an accurate and reliable picture of the cyber security posture of the enterprise.
Compliance Requirements Tracking
As with any governance matter, boards and senior executives identify the framework within which they must operate. This will include legal and regulatory requirements, corporate policies and possibly other considerations as well. At the security level the security team will work with the internal governance team to define appropriate IT governance frameworks, security policies and compliance specifications that align with each of the vital business processes.
One such governance framework, is the Australian Cyber Security Centre’s Essential Eight, which provides a simple, cost effective set of technical security controls for any sized organisation. The eight technical controls collectively monitor the core cyber hygiene elements of an effective cyber security risk management program. Each control has an implementation maturity model, so organisations can benchmark their maturity level, between 1-3, and then systematically measure subsequent scores as part of their performance improvement program. These scorecard reports, published to boards and senior executives, provide comprehensive and granular insights into current enterprise cyber resilience maturity measurement, performance trending and risk identification.
The Value of Scorecards
The scorecard, underpinned by data analysis from production systems, provides a way to slice data for different views and audiences such that each stakeholder has an appropriate level of detail. Huntsman Security’s Essential 8 Scorecard provides dashboards suitable for all levels of the business, based on measuring real-time data from running systems, against the widely used ACSC Essential Eight framework.
An operational dashboard like the one shown in Figure 1 (below) is suitable for the engineering team and security operations manager to be quickly alerted if a control has a problem.

Figure 1 Essential 8 Scorecard – Operations View
The same data is used to present a management security report for board level executives which also shows performance trend lines, as shown in Figure 2 (below).
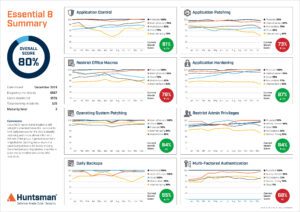
Figure 2 Essential 8 Scorecard – Trend reporting
By digging into the accompanying operational report, the security manager can investigate the specifics for each control and look at the report for a summary of what has happened and why.
In a digital world compliance is now an important security consideration for senior managers and boards, and these sorts of solutions are needed to provide confidence that the security team has it covered.
For more information on how you can build security posture monitoring and reporting solutions that inform both operations and senior management teams, or how Huntsman Security could help you deliver a compliance monitoring capability for your business, get in touch with our team.
 About Huntsman
About Huntsman




